Your cyber security team is thoroughly prepared to counter phishing attempts, malware, ransomware, DDoS attacks, and more. Do you feel safe now? You should not be.
It is time to take a look inside your team. It may sound cynical and hopeless, but internal threats can wreak even more damage than outside data breaches.
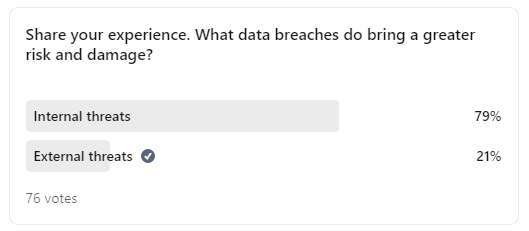
In Belkasoft's recent LinkedIn survey we asked, "Internal or external: share your experience please, what data breach elicits the greater risk and damage?"
79% out of 76 respondents said internal threats are more dangerous.
At the same time, we requested our guest experts to provide their detailed opinions on the matter.

|
Daniel Esquivel Chávez Kinshu Technologies Digital forensic analyst, an expert in IT-legal matters |
Internal or external: what data breach does bring a greater risk and damage?
Most of the investigations that I carry out using Belkasoft X are analyses of equipment in companies for information theft, including the Government. The subject is very sensitive and with Belkasoft we obtain the evidence from the forensic copy to the analysis of metadata.
What is harder to prevent? Why?
The most difficult or harder to prevent is always the internal employee, theft of information by trusted personnel, this is because they have access to it, and it is very easy to try to sell it. Information is power.
Which vulnerabilities and consequences of a data breach are harder to eliminate? Why?
Remove malicious code, even if it was executed by personnel without any knowledge of information, find the source, and be able to stop it from running on more computers.
What kind of insider behavior leads to threats more often: malicious, neglect, or accidental?
Accidental—the problem is the policies and permissions that users have, since they do not have any control, and they have access to everything, it hinders the security of the systems.
💡 Advice: Be careful what you download, where you browse and the permissions you give access to on your devices
 |
Oleg
Skulkin Group-IB Head of Digital Forensics and Incident Response Team |
Internal or external: share your experience please, what data breach does bring a greater risk and damage?
External. The thing is—it may be just a part of an attack kill chain. For example, many ransomware gangs exfiltrated data before deploying ransomware itself, and use obtained data as a secondary extortion technique. Also, many state-sponsored groups focus on data exfiltration as well, and, of course, they use quite advanced techniques to achieve this goal.
What is harder to prevent? Why?
The key to preventing both is proper monitoring and logging. Monitoring allows to catch both internal and external threats at the early stages of the attack lifecycle. Proper logging allows, at least, running a proper investigation if necessary. Another important thing is to configure access rights properly, so intruders have a hard time getting data of interest.
Which vulnerabilities and consequences of a data breach are harder to eliminate? Why?
Of course, to remove stolen data from public access. Especially, if we are talking about cyber criminals, they may publish exfiltrated data publicly, and it may be really sensitive data, but it may be from really hard to impossible to remove it from public access.
Another point is modern regulations, for example, General Data Protection Regulation (EU GDPR). So an organization may have not only reputational damage but also financial due to huge fines.
What kind of insider behavior leads to threats more often: malicious, neglect, or accidental?
Usually, malicious. For example, employees may leak data to third parties for money. But, of course, there are cases where it's accidental: default passwords may allow threat actors to access public-facing services with sensitive data.
💡 Advice: Systems may be very different, so it's very important to understand what's happening "under the hood" and focus not only on traditional forensic artifacts but also on the system's logging capabilities.

|
David Dietrich N-able Sr. Security Analyst |
Internal or external: share your experience please, what data breach does bring a greater risk and damage?
Between internal and external threats to your data, external is the more common, but internal is the more dangerous. Internal threats know the network, know what data is available, and may know ways around your safeguards to avoid detection longer.
What is harder to prevent? Why?
While external threats hammer away at your network 24/7/365, it's the determined internal threat that is harder to prevent. As mentioned previously, they know "the lay of the land," and can probably exfiltrate more data over time that a typical "smash and grab." If they're careful, they can steal your data, then resign, and take your data with them, giving it to a competitor. Nobody wants to see that happen.
Which vulnerabilities and consequences of a data breach are harder to eliminate? Why?
I would have to say weak passwords are the worst vulnerability, and sometimes are the hardest to eliminate. As for consequences, damage to your business reputation is probably the hardest to survive if you're part of a smaller company. That loss of reputation and trust is hard to regain and could cause a smaller company to shut down.
What kind of insider behavior leads to threats more often: malicious, neglect, or accidental
That would have to be accidental. It seems that, no matter what you do, there is always going to be someone who has to click a link.
💡 Advice: To guard against internal threats, follow least privilege access, enforce password complexity, and develop a robust training program to teach non-security employees about phishing, surfing, etc. Don't allow people to be local admins on their work systems. Enforce port security, and turn off USB access to anyone except system admins. In short, just follow the usual "best practices."
Whether you have internal or external company infrastructure threats Belkasoft corporate protection products will help to get the necessary evidence and patch the breaches.
Training on Corporate Cyber Investigations
Currently, Belkasoft offers training on corporate cyber investigations.
In this training, you will learn:
- How to analyze internet artifacts, such as emails and web browsing history
- How to use the built-in Connection Graph viewer in order to obtain an overview of connections (links between people) and their communications
- How to analyze system artifacts, such as the Windows registry, Windows 10 Timeline, and others
- How to detect and counter various anti-forensics techniques
- How to use carving techniques in order to recover deleted data from a hard drive and perform memory forensics
- How to narrow your search using Timeline view and HashSet analysis

