Imagine you are on a crime scene (if you are law enforcement) or on-scene of a corporate incident (if you are an incident responder). You can see some running devices, which you know may contain relevant information, but for different possible reasons you cannot take them with you. Additionally, you are under time pressure, and the problem is that the lack of time prevents you from conducting full analysis of the devices.
There could be multiple reasons why you cannot perform the complete analysis, for example physical danger such as ongoing crime, a fire, or other risks. You may be required to perform some instant actions: for example, a responsible person gives you 5 minutes to decide what device to take with you or what files to copy. For corporate incident response, there could just be too many devices,which would take months to analyze entirely.
What is the desired outcome you are looking for?
First, you want to know if, among the devices present, there is any important evidence or not. Second, you want to identify the key evidence.
To achieve this goal, you have to answer the following questions: which devices are most important out of many on-scene? Do they contain important digital evidence? If yes, where is this important evidence located so that you can make a copy of relevant files for an in-depth investigation in a safe place, such as your forensic lab.
We suggest you try Belkasoft Triage (Belkasoft T), a tool specifically designed by Belkasoft to help you achieve the goal of finding important evidence when you are under time constraints.
Once we identified the problem and your desired outcome of the solution, how does Belkasoft Triage help you to achieve this goal?
1) Belkasoft T runs directly from the dongle
Belkasoft T is truly portable and does not require an installation. The product can run directly from the dongle which also acts as your license. Moreover, it is designed to not leave a footprint, with the exception of an inevitable small footprint caused by the fact that this is software which is run from a thumb drive. Windows will automatically remember the storage device, the last run executable, and antivirus may check the file and store relevant logs, thus the footprint is similar to the one left behind from memory dumping software (like Belkasoft Live RAM Capturer).

The good thing about the Belkasoft T dongle is that it contains its own storage inside. You do not have to plug in another thumb drive or hard drive, which may cause a bigger footprint and may also require extra hardware such as a USB hub for computers and laptops with just a single USB port.
2) Belkasoft T completes the analysis in just minutes thanks to its effective search engine
The product is designed to complete the analysis very quickly. First, it allows you to select a disk or a folder. If you are extremely limited on time, a good idea could be to browse for the current user folder since most of the user data sits under this folder.
Belkasoft Triage does not do full analysis of discovered artifacts and this is what saves an enormous amount of time. For example, an Outlook mailbox of 40 GB in size, may take up to an entire day to be completely analyzed, if you extract all the emails including attachments. If you want to find hidden or deleted data and run data carving or try searching for encrypted files, this will also take a while. Belkasoft T does not perform these actions, instead, it looks for application profiles and important system files only.
This by the way, means that you can miss some data. This is a natural consequence of not performing the complete analysis, which you must be aware of. You can either perform a quick search, or a full analysis, you cannot do a quick, full analysis. This is where you have to find the balance: if your goal is not to miss any evidence, this is not the tool of choice and you would be better off with Belkasoft X, which has the proper functions you would be looking for in this situation.
3) Belkasoft T locates multiple types of potentially important evidence on the computer being investigated
First, it can locate more than 1500 types of supported artifacts, such as browsers, chat and social network apps, documents, pictures, audios, videos, cryptocurrency transactions and wallets, mobile apps should their data somehow get onto a computer, and so on. It is important that it also shows you nested data sources such as Android and iOS backups, virtual machines, as well as various memory files. Finally, Belkasoft T locates important system files such as registries, jumplists, link files, prefetch, event logs and others.
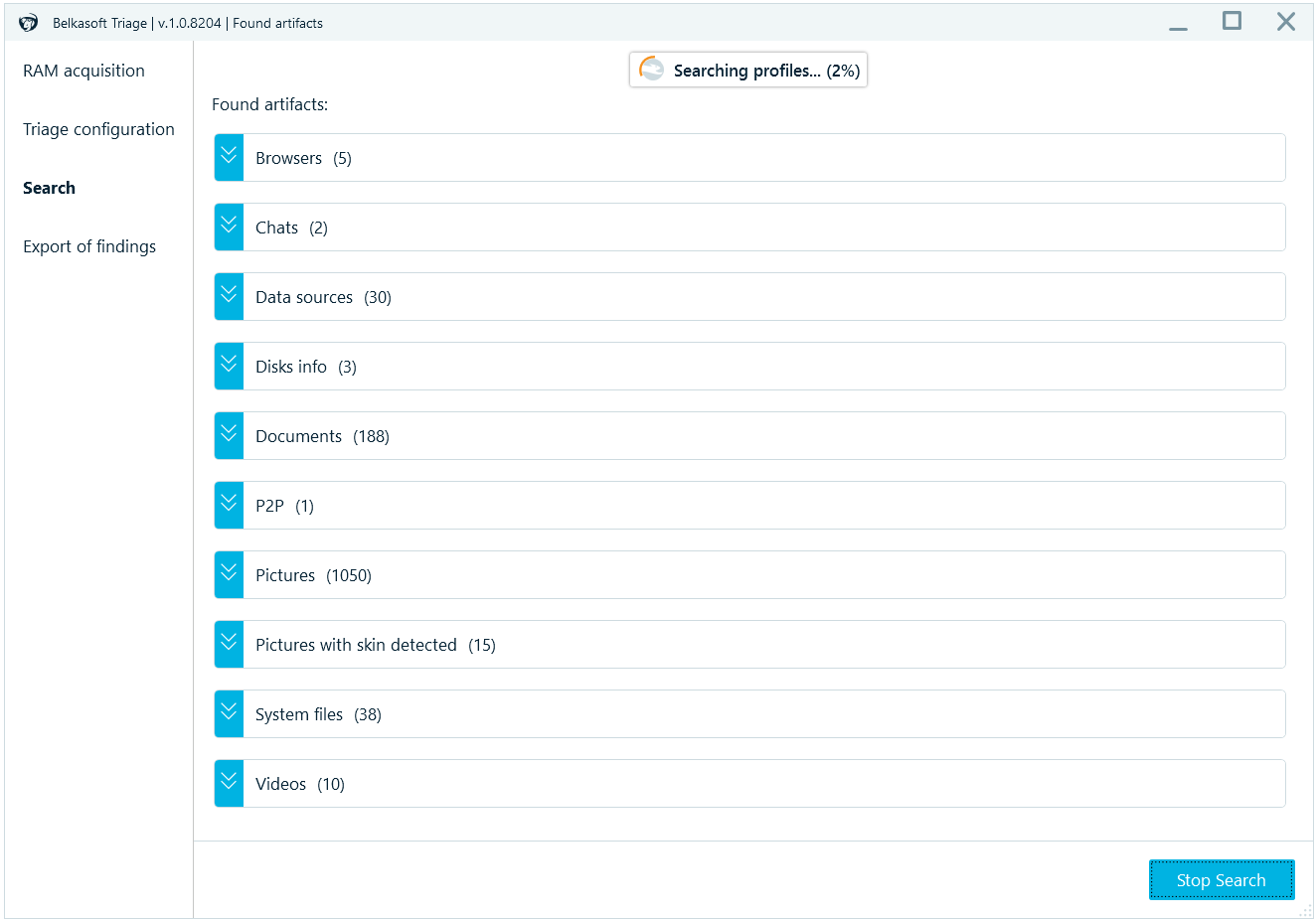
Apart from artifacts, the product will show you an immediate alert should any of two possible smoking gun signs be found, namely, a match of a hash value and pictures with skin tone. You can specify one, or multiple hash set databases and for the first occurrence of a match, we will show you a popup window. The product will not show you subsequent alerts because it is typically important that at least one match is found, to make a decision. Belkasoft T supports Project VIC, NSRL, and other types of hash databases.
4) Once artifacts are found, Belkasoft T allows you to select only the necessary profiles to be copied to the resulting image
The last step is to create a partial image of your findings. The product shows you a review page where you can see the results grouped by an artifact type and even filter by a file or a folder name. Then, simply select what you want to be included in your logical image.
Now you can safely leave the scene of the incident and you are sure that you have all the files you need to be analyzed deeper.
Apart from the application and system files, Belkasoft T also allows you to capture a memory dump which may give you tons of important information. If you have forgotten to do this with Belkasoft Live RAM Capturer tool in the first place, you will be prompted to run the memory acquisition as the first step.
Conclusion
There are many potential situations where you may have to identify and obtain digital forensic evidence in a short period of time, whether it is an ongoing crime, fire, or too many devices to analyze. In such cases, you may need to involve a so-called ‘triage’ to find out which devices and which files can be useful in your investigation or examination.
In such cases, you will benefit from utilizing Belkasoft T, a portable tool, which can run directly on a working Windows computer and effectively performs the triage analysis in just minutes. Belkasoft T is capable of identifying multiple types of potentially important evidence and selecting only required profiles to be copied to the resulting image. The tool’s output format is a standard TAR image which can be further analyzed with Belkasoft X or any other forensic products.
Note: For a limited time, Belkasoft offers discounts for the bundle of Belkasoft X and Belkasoft T. Contact our sales team for more information.
See also
- Get more details on Belkasoft T
- Investigating the Dropbox Desktop App for Windows with Belkasoft X
- WhatsApp Forensics on Computers (Windows PCs and Macs)