Cloud storage services are becoming more and more popular among businesses and individuals as they offer convenience in both file storage and platform independent file sharing. Meanwhile Dropbox accounts for around 34% of all hosting services. According to official Dropbox statistics, the number of users in 2021 has exceeded 700 million.
Dropbox is designed to store and share files and collaborate on projects. The service is available for installation as a desktop application for Windows, macOS and Linux, a mobile application for iOS and Android and Xbox app. Therefore, it can be accessed from a PC, tablet, or a smartphone, using a browser or desktop application. File changes on one device are automatically synchronized across all devices.
It is obvious, Dropbox and similar cloud services can easily be used by lawbreakers to store illicit materials in it, or, on the contrary, malicious users might try to obtain sensitive data stored in the app. Therefore, it is crucial to understand, what kind of artifacts can be found in various locations and know how to find evidence and traces of criminal activity when investigating Dropbox.
In this article we will focus on investigating a Dropbox desktop application for Windows, as both Dropbox and Windows OS are quite popular among users. We will use Belkasoft X, a digital forensic and incident response tool, to analyze it, and specifically we will review the case of a non-default synchronization folder and deletion of files in multiple ways.
Analyzing the Dropbox desktop app on Windows
The key Dropbox functionality is the possibility to synchronize any file change across various devices, where Dropbox app is installed.
During the Dropbox installation a user can choose one of two options:
- Store files locally, so files will be downloaded and stored on the hard drive
- Online only
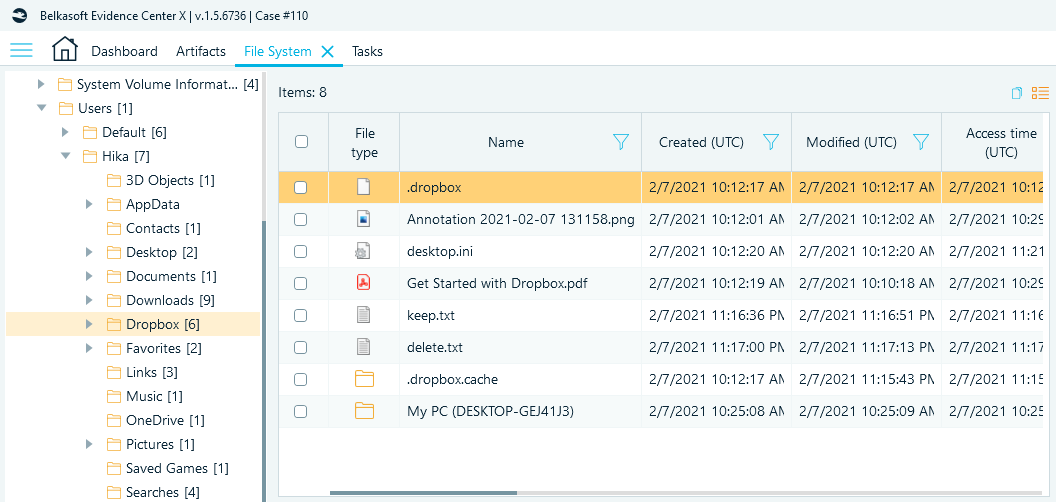
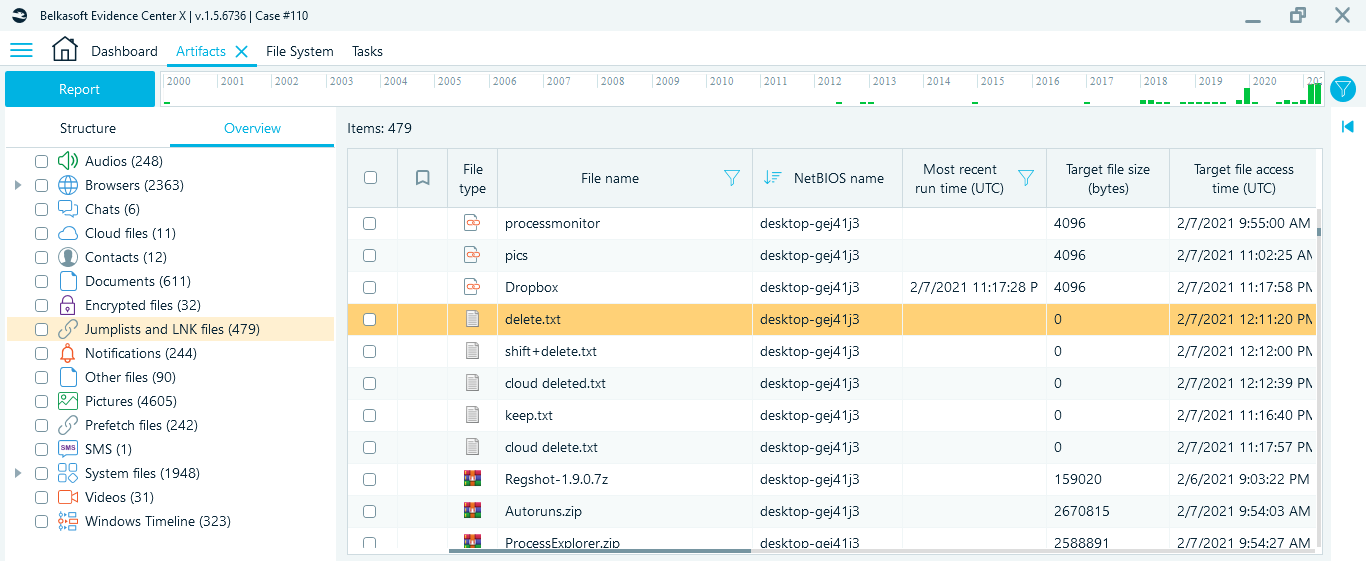
By default, Dropbox utilizes 'C:\users\<username>\Dropbox' as a synchronization folder, but the user can choose any location via advanced settings. Later this folder will be marked with the hidden '.dropbox' file that indicates the shared folder.
Figure 1. A hidden '.dropbox' file located under non-default Dropbox synchronization folder as shown by File System window of Belkasoft X
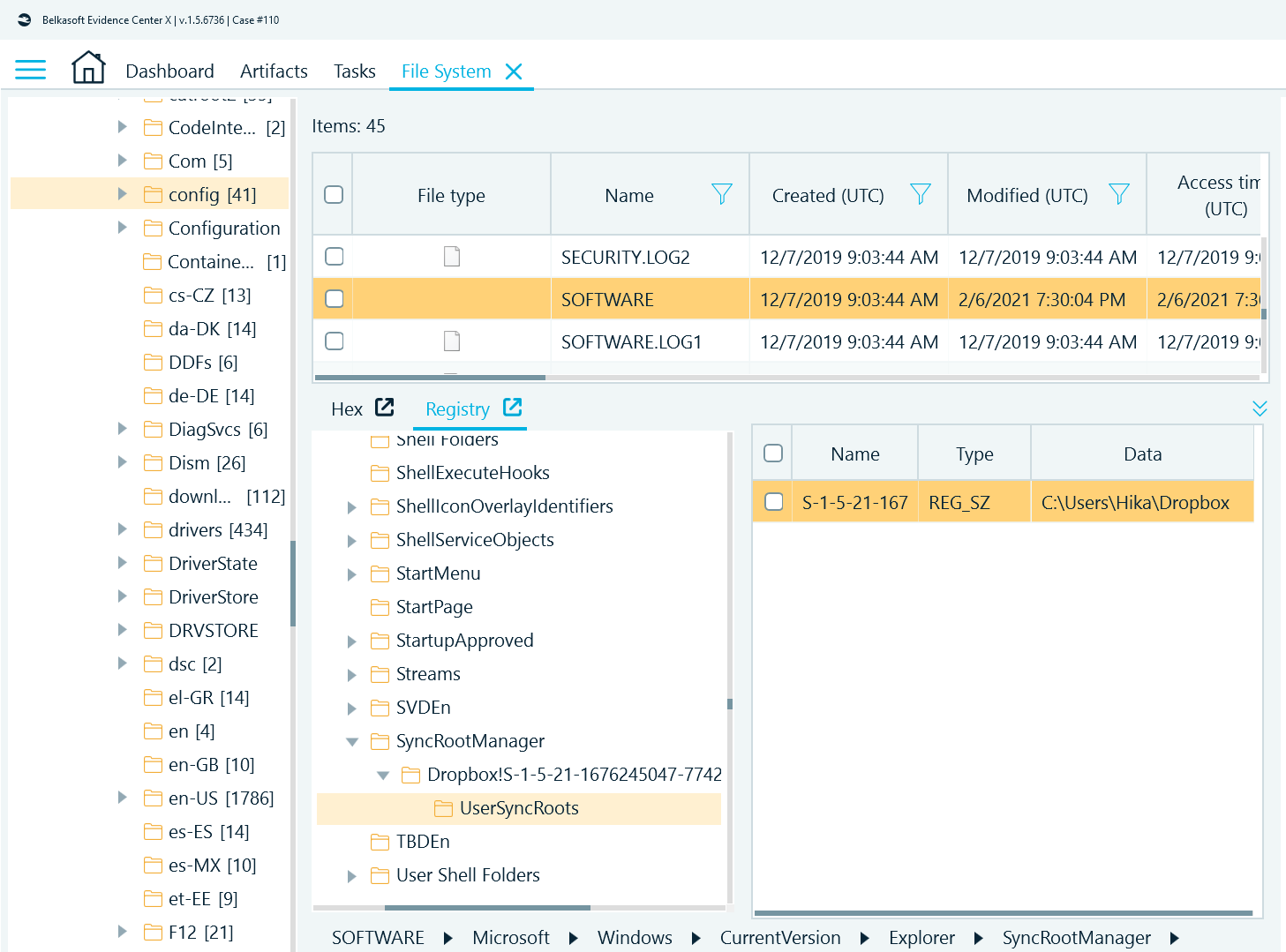
If a non-default folder is used for synchronization, information about this folder can be easily obtained from the following registry key:
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SyncRootManager\Dropbox!<SSID>!Personal\UserSyncRoots\
Figure 2. The registry key showing where the Dropbox synchronization folder can be found
To stay up-to-date and synchronize user data, Dropbox installs several services: 'dbupdate', 'dbupdatem', 'dbxsvc'.
Also, to run at system startup it uses 'HKLM\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run key' with the 'C:\Program Files (x86)\Dropbox\Client\Dropbox.exe' value data.
Other keys of interest are 'HKCU\SOFTWARE\Dropbox\ks' and 'HKCU\SOFTWARE\Dropbox\ks1'. These keys are used to decrypt encrypted SQLite3 databases, e.g. 'C:\Users\<username>\AppData\Local\Dropbox\ instance1\config.dbx' , that contains user email, host ID and Dropbox path among other settings.
Files protected with the ks key are located under 'C:\Users\<username>\AppData\Local\Dropbox\instance_db'.
The 'ks1 key' is used to protect files located under 'C:\Users\<username>\AppData\Local\Dropbox\instance1'.
Analyzing the Dropbox user data with Belkasoft X
The first step to find user files is to search for it in the synchronization folder.
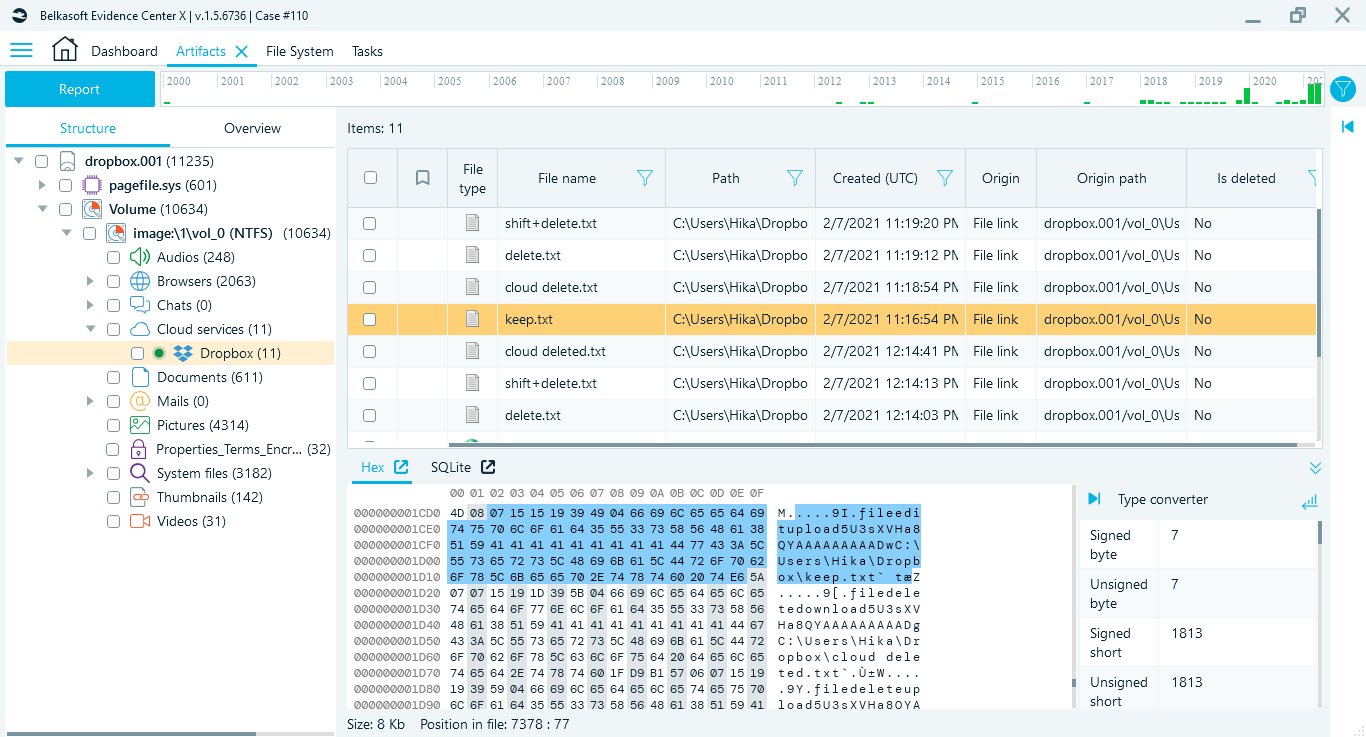
To demonstrate how Belkasoft X analyzes the existing and deleted files from the Dropbox folder, several files were created in the 'Dropbox' folder. Later three of them were deleted to check how many traces remain.
The files, which were used for testing are:
- keep.txt—the file, which remained in the Dropbox.
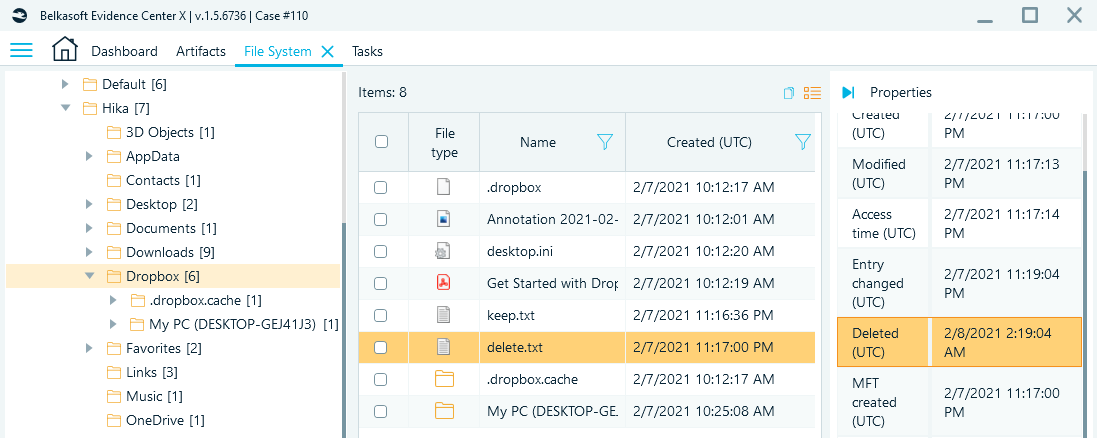
- delete.txt—the file, which was deleted using 'Delete' button.
- shift+delete.txt—the file, which was deleted using the 'Shift' and 'Delete' key combination.
- cloud delete.txt—the file, which was deleted via web interface.
You can find currently existing files in the synchronization folder as well as files deleted with 'delete' key. This is due to the file deletion mechanism in NTFS. For the same reason, such files along with their attributes can be found in the $Recycle.Bin.
Figure 3. The deleted file 'delete.txt' found in the Dropbox folder
Belkasoft X allows you to find both the name and content of deleted files as well as their timestamps. To find traces of files deleted in other ways, you can use standard techniques and view recently used documents: LNK files, Recent Documents, and others.
Figure 4. The 'shift+delete.txt' file in 'Jumplists and LNK files' node in Artifacts window of Belkasoft X
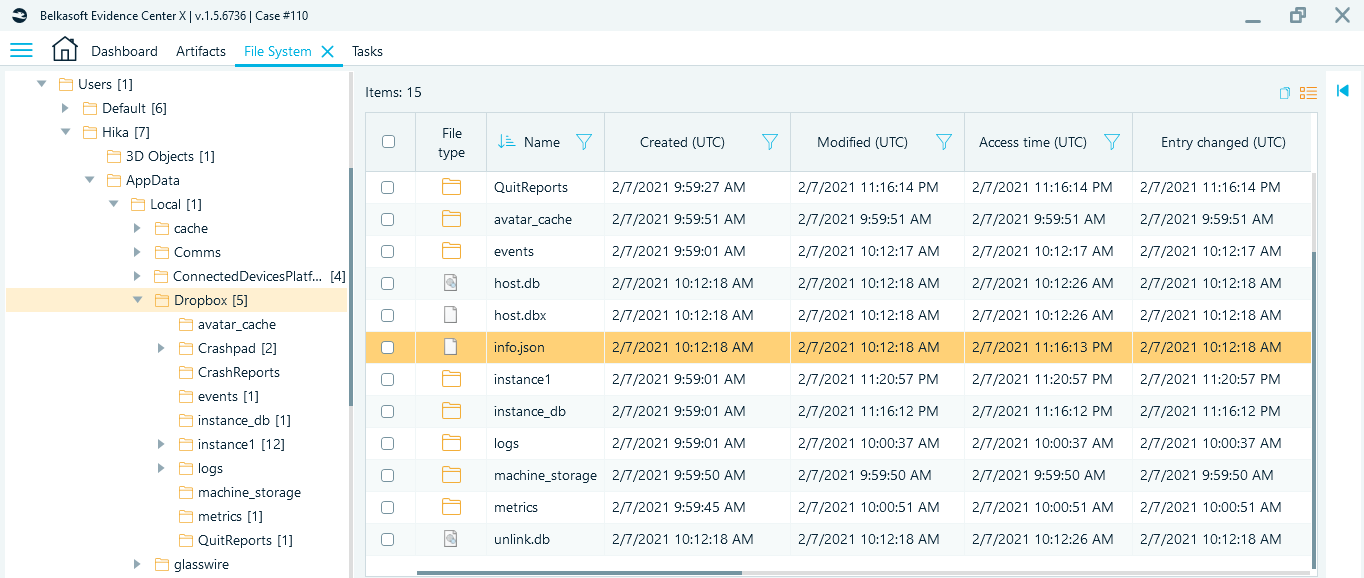
The second step of user data analysis is an investigation of the 'C:\Users\<username>\AppData\Local\Dropbox' folder. Here you can find the 'info.json' file that contains host ID, path to synchronization folder, and subscription type.
Figure 5. A 'info.json' file in 'Dropbox' subfolder
Path to the synchronization folder also can be found in the 'host.db' and 'host.dbx' files, but their content is Base64 encoded.
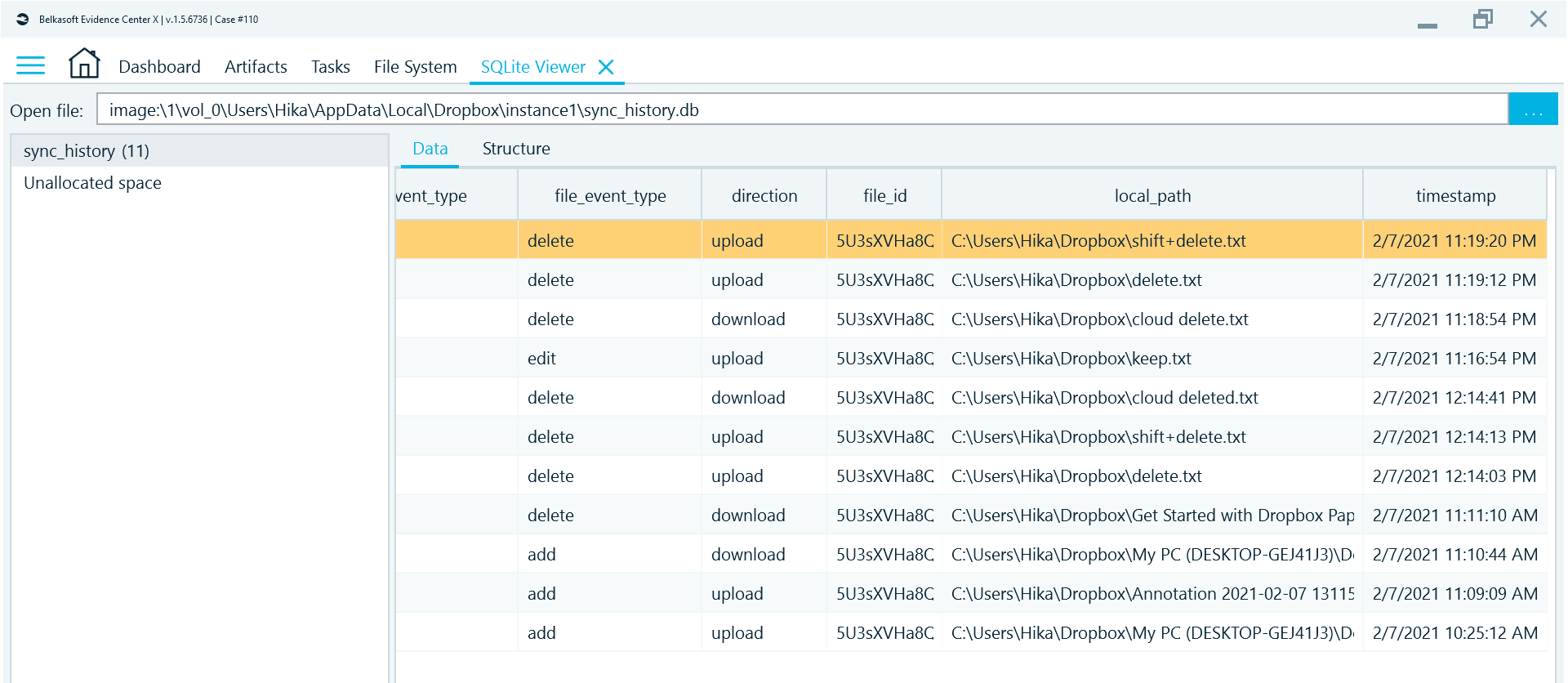
Under the 'C:\Users\<username>\AppData\Local\Dropbox\instance1\' you can find 'sync_history.db', an SQLite database with synchronization history, which contains file names, actions, direction, and Unix timestamps. The database is not encrypted, so you can easily recover recent actions performed with the files on the suspect’s host.
Figure 6. SQLite3 database 'sync_history.db' with synchronization history
If you have run Cloud files analysis during adding your data source to a Belkasoft X case, you will be able to find this information in the Artifacts >> Cloud services >> Dropbox:
Figure 7. 'Dropbox' folder with synchronization history in 'Cloud services node in Belkasoft X
One more important question that needs to be discussed is how you can deal with the cloud-based files, which are not stored locally. And now it is time to remember 'config.dbx' database, that was mentioned at the beginning of the article. This file is encrypted using the SQLite Encryption Extension and can be used along with the 'C:\Users\<username>\AppData\Local\Dropbox\instance_db\instance.dbx' to replicate the suspect’s host and get cloud-based files.
Encryption keys are kept in the registry ('\HKCU\SOFTWARE\Dropbox\') and protected using DPAPI, so the user's login password (or its SHA1) is needed for their decryption. After the decryption, the 'User Keys' are utilized to derive '.dbx' decryption keys using PBKDF2.
As a result, the following process is suggested:
- Get encrypted files 'C:\Users\<username>\AppData\Local\Dropbox\instance1\config.dbx' and 'C:\Users\<username>\Appdata\Local\Dropbox\instance_db\instance.db'
- Extract registry keys 'HKCU\SOFTWARE\Dropbox\ks' and 'HKCU\SOFTWARE\Dropbox\ks1' and decrypt them using DPAPIck (tool for Windows Data Protection API decryption)
- Encrypt extracted keys on an investigator’s workstation using DPAPI and add them to the registry
- Replace database files on an investigator’s workstation and launch the Dropbox to start the synchronization process.
Conclusion
In this article, we reviewed the Dropbox app, particularly, how it stores its data on a Windows computer and in the cloud. We showed how you can analyze it manually or with the help of Belkasoft X, a digital forensics and incident response software. You can try Belkasoft X for free at https://belkasoft.com/get.
With the information provided in the article you can find the Dropbox synchronization folder and deal with the encryption keys Dropbox uses to protect user data files. We reviewed important artifacts as well as how to get the Dropbox user data stored in the cloud.