The following story was told by our CEO, Yuri. Quoting it first person.

This story took place just a short few months ago. The team and I were chatting with one of our sales employees about a new trouble ticket that had made its way into our management system. We use a service management software which handles our sales and support emails, so every new email creates or updates a ticket.
This ticket in particular was new and what happened next, later appeared to be a misunderstanding between our team. From the dialog, I became confident that my colleague had checked the trouble ticket and that the email was legit. For these reasons, I bravely downloaded an attachment from the ticket and opened it on my workstation.
Undoubtedly, I am extremely suspicious and cautious when it comes to attachments in both my job and personal communications, even if I receive an attachment from a trusted source. But as I downloaded this attachment, something felt wrong based on the name of the file and accompanying text. I always use online viewers to view the contents of an attachment, rather than offline viewers to open such a file. I always have up-to-date antivirus software running on all of my machines, but of course I do not believe this alone is a panacea.

After opening the Excel document, I immediately knew something was wrong from what was displayed within the file and I realized that I am in trouble. I re-read the ticket to make sure that my assumptions were correct and now I clearly understood it was a scam. Cursing myself for stupidity, I instantly disconnected my computer from the Internet and started trying to figure out just how much trouble I was in.
Luckily, I have my tool, Belkasoft X, and the first thing I thought to do was to add my own drive to the product so that I could analyze my own $MFT file. This would help me understand what new files may have been dropped by a seemingly weaponized document. By the way, if you are aiming to achieve a similar task, just add your drive into Belkasoft X without analyzing it, go to our File System viewer and simply select recursive view at the top level of the content pane to be able to sort all files by creation time.
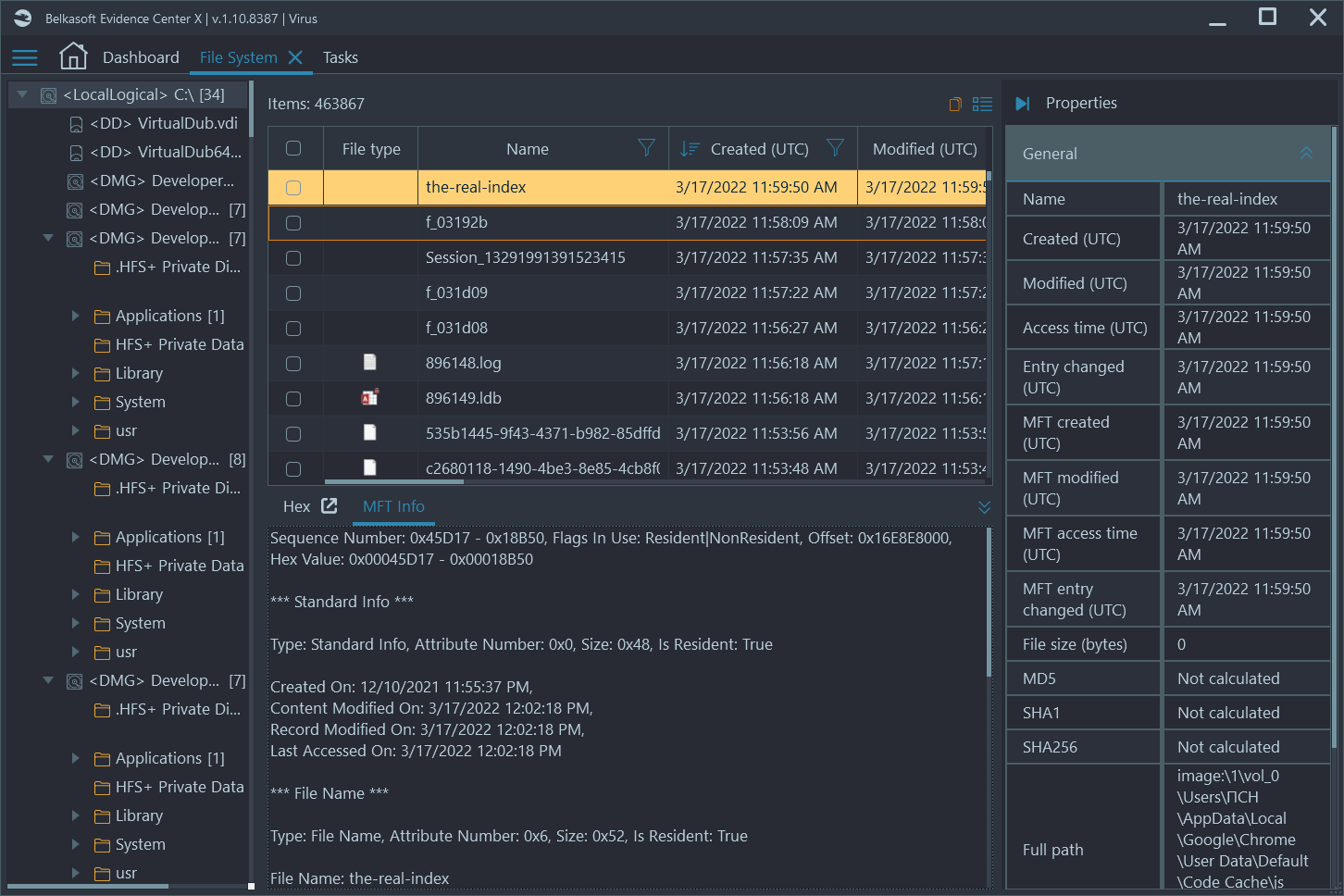
I immediately found the malicious Excel document, selected it, and then sorted all files by creation time. This allowed me to see all files that were created directly after the malicious one was opened. Surprisingly, I saw only innocent files including various cache files and system files.
Thankfully, this time I got off the hook with a slight fright. When, together with better specialist in malware than I, we analyzed the file in more detail. The malicious excel document appeared to be targeting a much older version of Excel, and that was why it had failed to drop any additional malicious artifacts and seize my computer. I did however, go through a few unpleasant minutes though.
There are no conclusions in this story. This is simply a reminder that even the technical savvy can make a mistake, leading to malware installation or really any type of malicious intent.
See also
- [Free On-demand Сourse] Incident Investigations with Belkasoft X
- The case of a missing girl and the power of a memory dump
- Browser forensics and the case of Casey Anthony
- Preserving chain of custody in digital forensics
- 5 Bloopers of a Digital Forensic Investigator
- Where did this chat come from? The 'Origin path' concept in Belkasoft X
- Why Belkasoft should be your tool of choice for Mobile Forensics