Apple first introduced USB Restricted Mode in iOS 11.4.1, and since then, the setting has seen several changes, especially in iOS 12 and iOS 13.
In this article, we intend to review USB Restricted Mode strictly as a factor that impedes investigations and then show you how to get past it using Belkasoft X.
What is USB Restricted Mode?
Figure 1. USB Restricted Mode in effect on a locked iPhone
USB Restricted Mode is a setting that forces an iOS device to stop all data communications through its port after a specific period (usually an hour) since the last unlock.
Essentially, if a user does not unlock their passcode-protected iPhone and does not connect it to a USB accessory within an hour, the iPhone will refuse to communicate with accessories or computers. In some cases, the iPhone might not even charge, especially when it gets connected to a computer's USB port.
In the Activating data connections security chapter from Apple Platform Security Spring 2020, Apple described its protection concept this way:
To improve security while maintaining usability Touch ID, Face ID, or passcode entry is required to activate data connections via the Lightning, USB, or Smart Connector interface if no data connection has been established recently. This limits the attack surface against physically connected devices such as malicious chargers while still enabling usage of other accessories within reasonable time constraints. If more than an hour has passed since the iOS or iPadOS device has locked or since an accessory's data connection has been terminated, the device won't allow any new data connections to be established until the device is unlocked. During this hour period, only data connections from accessories that have been previously connected to the device while in an unlocked state will be allowed. These accessories are remembered for 30 days after the last time they were connected. Attempts by an unknown accessory to open a data connection during this period will disable all accessory data connections over Lighting, USB, and Smart Connector until the device is unlocked again. This hour period:
- Ensures that frequent users of connections to a Mac or PC, to accessories, or wired to CarPlay won't need to input their passcodes every time they attach their device.
- Is necessary because the accessory ecosystem doesn't provide a cryptographically reliable way to identify accessories before establishing a data connection.
In addition, if it's been more than three days since a data connection has been established with an accessory, the device will disallow new data connections immediately after it locks. This is to increase protection for users that don't often make use of such accessories. Data connections over Lightning, USB, and Smart Connector are also disabled whenever the device is in a state where it requires a passcode to reenable biometric authentication.
The user can choose to reenable always-on data connections in Settings (setting up some assistive devices does this automatically).
A computer or connected accessory is unlikely to detect or recognize an iOS device on which USB Restricted Mode is in effect—since the lighting port ends up in charge-only mode. Therefore, USB Restricted Mode seriously deters third-party forensics tools from performing data acquisition or extraction tasks.
Even if a passcode-protected iPhone device is somehow obtained in its unlocked state, an investigator or researcher might still find the hour limit (for data communications over the USB port) too small a window to get to the office and set things up to acquire the device.
USB Restricted Mode was automatically enabled once users downloaded the iOS update, so Apple wanted it to go into effect on all iOS devices. To the untrained eyes, the purpose of the new USB setup may not have been so obvious because Apple claimed they wanted to improve security while maintaining usability.
However, given users complaints about the setting itself being inconvenient for them—and even more so in retrospect—we can safely conclude that USB Restricted Mode was targeted at forensics tools, which (at the time) were having so much success in cracking passcodes for iOS devices and extracting data from them.
How does Belkasoft X handle USB Restricted Mode?
With Belkasoft X you can rest easy and disable USB Restricted Mode on an iPhone.
The product disables USB Restricted Mode automatically during the checkm8-based acquisition process. You do not even need to perform manual or complicated maneuvers.
Figure 2. The Add data source screen in Belkasoft X showing checkm8
As you may have figured out already, the new function is extremely useful in situations where you do not have the passcode to an iPhone. Otherwise—if you did have the passcode—you simply would have unlocked the phone (to avoid dealing with USB restricted mode)—and then you could acquire data in AFU.
Now, even when you lack an iPhone's passcode and USB restricted mode is in effect on the device, you will still be able to acquire data in BFU—if you have Belkasoft's tool. More importantly, BFU acquisition can still provide you with a lot of data.
Below, you can see the comparison of results from one of our experiments—Belkasoft's checkm8-based acquisition from a passcode-protected iPhone with and without the passcode:
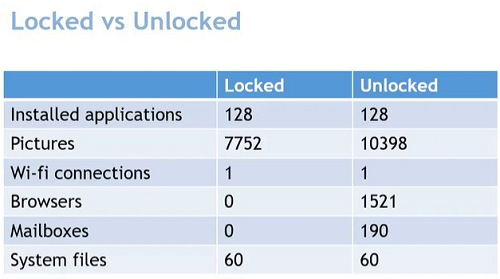
Figure 3. Table showing the difference in the volume of artifacts extracted from a locked and unlocked device
As a digital forensics tool, Belkasoft provides several advanced functions—such as checkm8-based acquisition, iOS agents, and others—that investigators and researchers use to acquire and extract data from iOS devices. The ability to disable USB Restricted Mode—a known impediment—simply enhances BEC's well-established capabilities for mobile forensics.
On what iPhones and iOS versions can Belkasoft lift USB Restricted Mode?
For the function that disables USB Restricted Mode on an iPhone, Belkasoft supports precisely the same iPhones models and iOS versions that it does for checkm8-based acquisition:
- Supported iPhone models—iPhone 5S to iPhone X
- Supported iOS versions—iOS 12.0 to iOS 16 beta
Conclusion
While Apple's USB Restricted Mode may have been a simple addition to the security setup in iOS devices for users, its introduction has made things more difficult for research and investigations on those devices. The new USB setting is not foolproof or infallible, however.
We established that digital forensics practitioners can use special functions in a tool—such as the one in Belkasoft X—to easily get past Apple's USB restrictions. This way, they can then proceed to acquire or extract data from iOS devices.

