Call logs, SMSes, emails, social networks communications and, of course, chats in instant messengers can give you a lot of important information in a course of a forensic investigation. Let's see how one single chat product can be examined from different aspects, each of which gives one more – unique! – part of puzzle.
In our case, the suspect had Skype installed on his laptop and mobile device which were seized and investigated with Belkasoft Evidence Center.
First part of the analysis is easy: chats are extracted from existing main.db, a SQLite database where Skype stores its history logs.
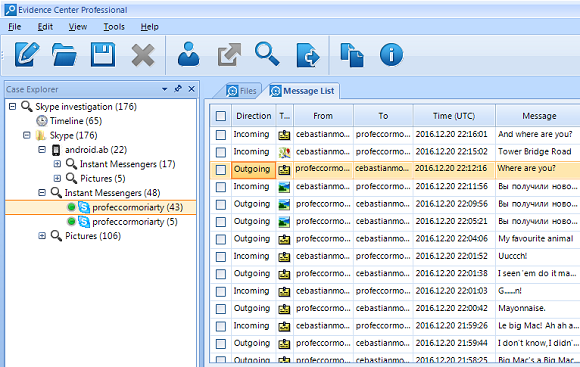
BEC automatically locates and extracts chat history from Skype database, as
well as hundreds of other messengers
Is this it? No, there are many things yet to be discovered!
First of all, BEC finds not just text chats. Looking in the Overview section of the product, you can note the following types of data extracted from the same Skype database:
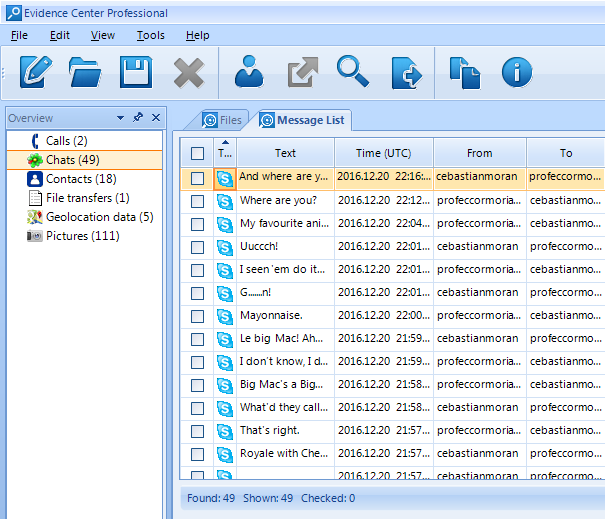
- Calls: Voice calls made via Skype
- Contacts: Contents of Skype address book, as well as interlocutors not added to it
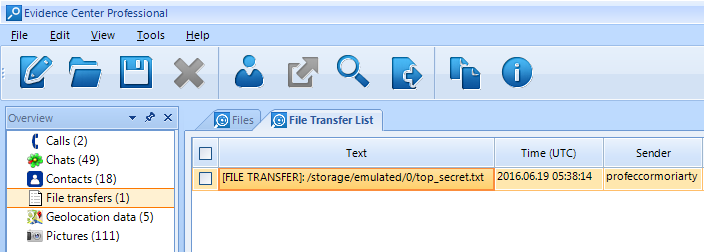
- File transfers: Files sent and received via Skype "Send file" feature:
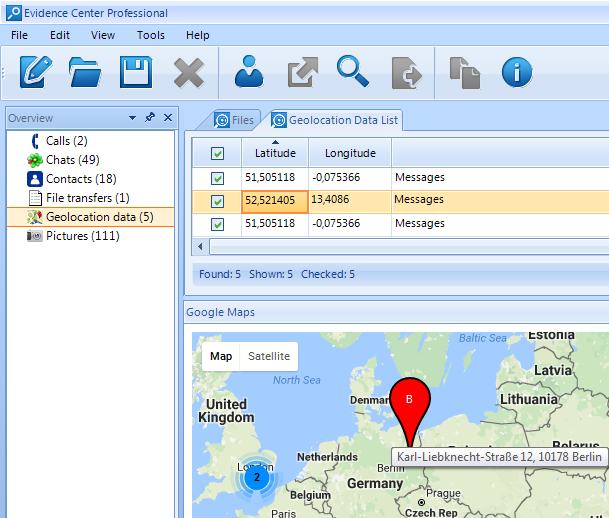
- Geolocation data: mobile Skype client allows a user to send their current location to an interlocutor. Belkasoft extracts this data:
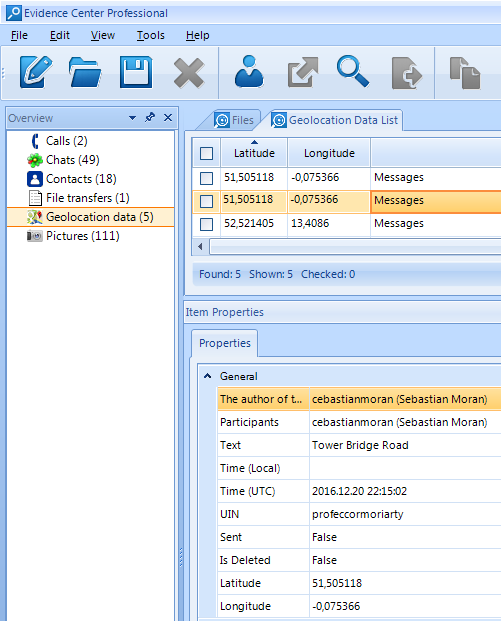
Besides, you can visualize one or multiple locations on Google Maps (if you have Internet connection) or Google Earth (if you don't).
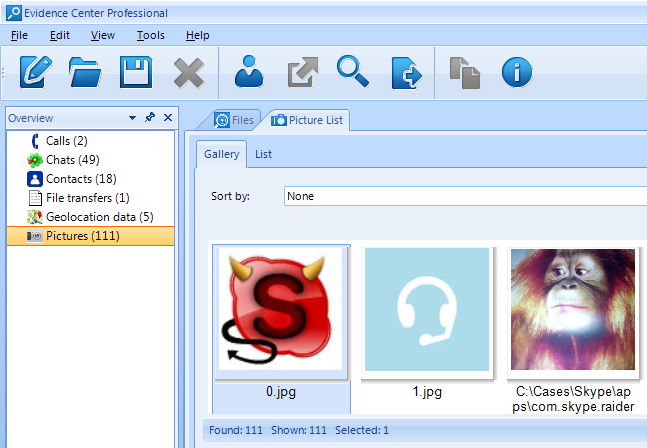
- Pictures: Skype allows a user to share photos inside a chat, and BEC shows such pictures:
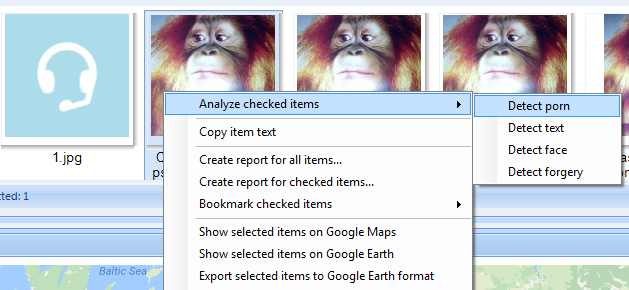
By the way, BEC can automatically analyze pictures for faces, skin tone and scanned text, if this is what your investigation about:
- This particular database did not contain other types of Skype artifacts, but there are more supported by BEC: SMSes, voicemails and so on
Now is this all? The answer is still no! What else is there?
Let us check if there is anything deleted in the Skype history. How to do that? With Belkasoft you can easily review deleted items in the convenient SQLite Viewer window. In order to populate this window with Skype data, one should select corresponding Skype profile in the Case Explorer window of Evidence Center:
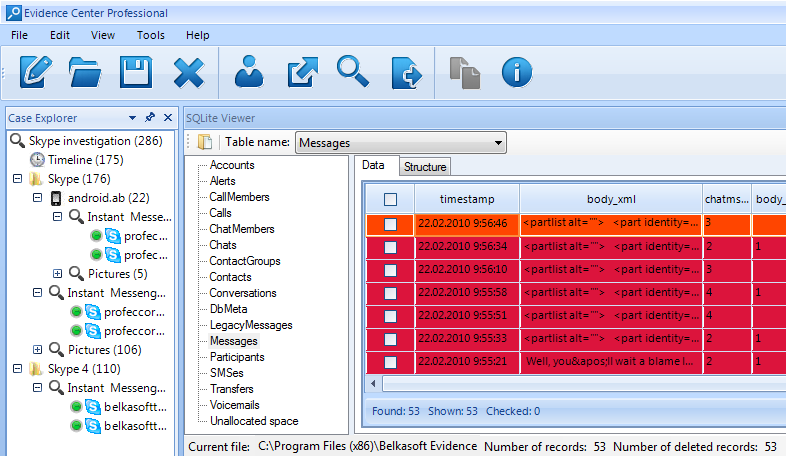
To the left of SQLite Viewer window you can see tables of selected Skype database. One of the tables is called Messages, and it stores chats sent or received. In the picture above you can see a number of records highlighted with red background. These items are originated from a special area of SQLite database called "freelist". This area stores recently deleted items, which Belkasoft can recover for you.
You are probably thinking: this has to be it, right? But once again, no! Let us pay more attention to File System pane of Evidence Center. What is the file named main.db-journal next to main.db database?
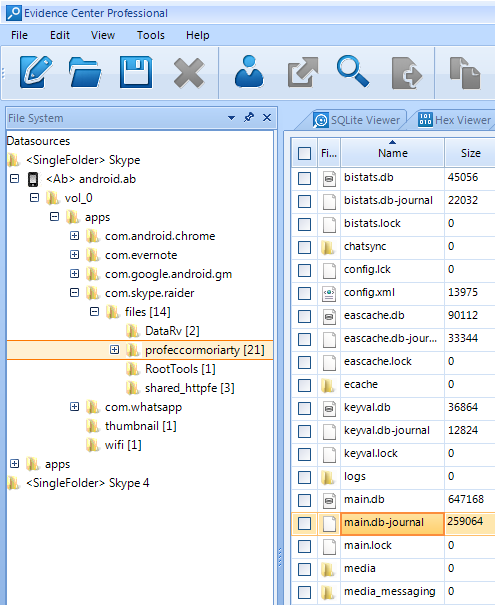
Evidence Center can visualize file system structure of computers and mobile devices (including Android backups). If we navigate
to the suspect's profile folder, we will see main.db file along with main.db-journal. The journal file is of significant size: more than 40% of the main database file!
What is inside this file? Is this information important? Yes, it is! Journal file is a SQLite auxiliary file which may contain records absent in the main database. If we go back to SQLite Viewer, we will see records highlighted with cyan:
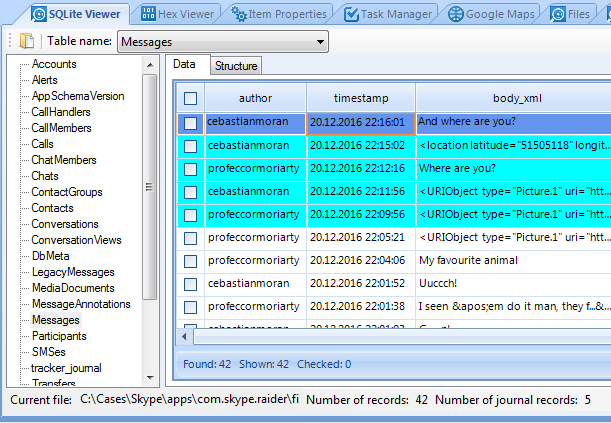
For chats, 5 extra messages were found in the journal file. For MediaDocuments table the number is even bigger: 370 items out of 1361. Thus, journal file information is not to be overlooked!
Now, this is it.
Joke! There is more.
Each SQLite database, if used frequently, contains unallocated space. Don't confuse it with unallocated space in a hard drive. This is a separate concept, and what is important to know is that SQLite unallocated may contain remnants of recently deleted items. This is not similar to freelist and, unlike info in freelist, unallocated space can contain random or damaged data. However, using data carving of unallocated SQLite space (built-in feature of BEC), you can recover meaningful data:
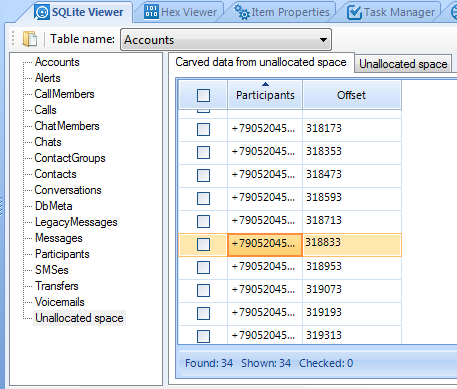
In this database only one field was recovered from Skype database
unallocated, but very important one: one of interlocutors' mobile phone number.
For those who prefer to verify results manually, BEC has low-level means for that. HexViewer window allows to visualize a SQLite record (allocated or unallocated), any file selected in File List, disk partition or volume selected in File System pane, or mobile phone backup contents.
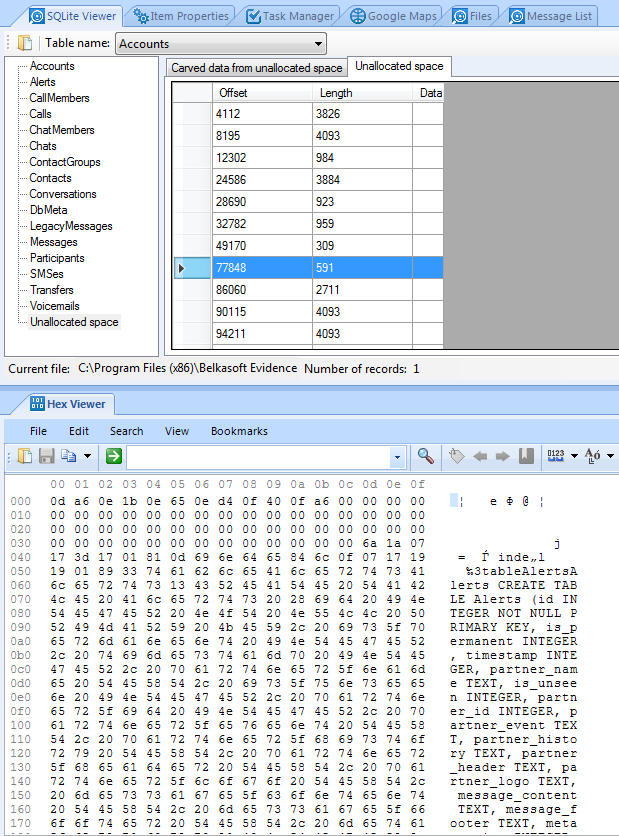
HexViewer shows binary contents of selected SQLite unallocated
space item
Fortunately, in our case the suspect's laptop was found switched on, so it was possible to capture Live RAM. BEC contains Live RAM Capturer utility as a part of its installation package. Live RAM Capturer is a portable tool, which can run from a thumb drive and dump all the memory of a running Windows machine. Then, the output can be analyzed in Evidence Center. In particular, Skype details can be found inside the memory dump if it was running at the moment of memory acquisition.
When we inspect File System pane of BEC, we can see that Skype.exe was indeed running:
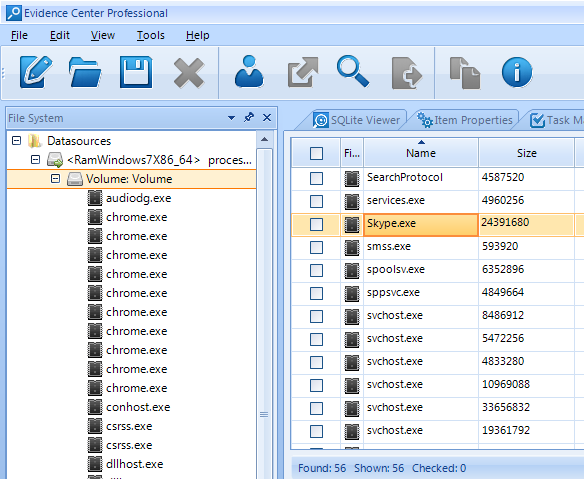
Now we switch to Case Explorer pane and trust the tool's ability to carve RAM artifacts:
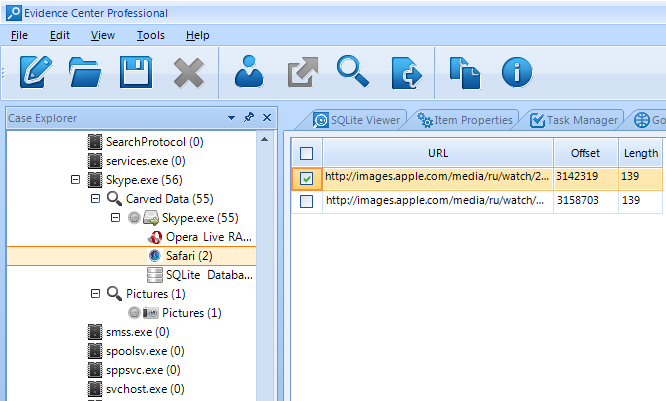
You can see that Skype.exe process memory contains links in Safari and Opera format. Some of these links lead to pictures which are still alive on Apple server:

Is this it now? Yes, that's it for this article, but just for the sake of brevity. We haven't covered Skype data carving of pagefile and hibernation file, as well as investigation of slack space, analysis of Volume Shadow Copy, processing Skype hidden inside virtual machines and Skype app for other popular operating systems such as Mac OS or Linux, and many more other potentially crucial aspects of Skype investigation. Be sure, however, that all of them are supported by the product reviewed in this article, Belkasoft Evidence Center (BEC).
P.S. We reviewed Skype app only, but did you know that Belkasoft supports several hundreds of other chat applications?
More details on BEC
- General info: https://belkasoft.com/ec
- Free fully functional trial: https://belkasoft.com/trial
- Sign up to free online webinar: https://belkasoft.com/webinar (NEW: Webinars in Spanish are now available!)
- Quote request: https://belkasoft.com/quote
- Belkasoft articles on various forensic topics: https://belkasoft.com/articles. One of useful articles to read is "SQLite forensics" article, explaining some of concepts from this article
- Belkasoft customers: https://belkasoft.com/customers
- BEC tutorials: https://belkasoft.com/tutorials
- Academic discounts: academic@belkasoft.com