DFIR Labs in the Cloud: The Future of Digital Forensics
Introduction
The surge in volumes of data stored by digital devices has created a headache for forensic examiners—too many devices piling up due to limited resources available in digital forensic labs. The core problem? A shortage of space to store evidence and insufficient computing resources to efficiently process it. However, there is a smart solution already making waves in other sectors. It involves moving a Digital Forensics and Incident Response (DFIR) lab to the cloud.
This shift simplifies the management of hardware resources and offers potential benefits. But is it feasible? The sensitivity of data handled by DFIR labs introduces a number of complexities to this equation.
In this article, we will cover the ins and outs of adopting cloud solutions in digital forensics and explore how DFIR tools, such as Belkasoft X, can embrace this change.
How cloud fixes typical downsides of offline labs
Traditionally, digital forensics labs operate within on-premises networks, frequently isolated from the internet due to security considerations. This setup subjects them to the inherent challenges of the offline reality:
- Storage and hardware upgrades: If there is not enough storage space for evidence or a hardware upgrade is needed, examiners have to initiate a lengthy process that entails making requests to the procurement department, approval from management, vendor selection, purchasing, installation, and more. The entire procedure can often span several weeks. In contrast, within a cloud environment, these tasks can be accomplished in a matter of minutes, if not instantly.
- Evidence sharing: In a traditional on-premises environment, sharing evidence with other departments or agencies typically involves the physical transfer of machines and hard drives, a process prone to logistical and security challenges. In contrast, cloud-based solutions streamline this task, reducing it to setting permissions and sending a link.
- IT maintenance: On-premises labs often require dedicated IT departments to oversee the installation and maintenance of hardware and software infrastructure. In the cloud, this responsibility typically shifts to the cloud service provider, minimizing the need for in-house IT expertise and infrastructure management.
So, why do digital forensics specialists still opt for on-premise labs? The primary reason is legal. In many countries, forensic labs are legally obligated to operate on computers disconnected from the internet. Clearly, this requirement cannot be met with cloud-based computing.
Yet, if we dive deeper into this subject, considering all the facets, it is evident that the cloud solution is not just an attractive choice—it is also a viable one.
Legal regulations for storing digital evidence
Forensic labs deal with digital evidence that often contains sensitive data, such as the personal details of suspects and victims. Therefore, let us begin by examining the regulations governing the storage of such data and the implications for storing and processing it in the cloud.
Obviously, we cannot look into each country's documents and can only make assumptions based on publicly available resources. None of the ones we found impose direct restrictions on storing digital evidence, including personal data in the cloud.

For example, in the USA, only Criminal Justice Information (CJI), such as Biometric Data, Identity History Data, Biographic Data, Property Data, and Case/Incident History have special requirements for cloud storage security. Cloud service providers (CSPs) that host CJI data must run background checks on the employees dealing with the servers that store it. However, digital evidence, such as computer and device images, is not considered as CJI, so technically, it can be stored in the cloud.
In Europe, personal data storage is regulated by GDPR and other associated documents such as EU Cloud Code of Conduct. They do not prohibit storing personal data in the cloud but outline specific guidelines that CSPs must adhere to.
Singapore has a Personal Data Protection Act (PDPA) that says "any organization that engages the services of a CSP still remains responsible for complying with the PDPA in respect of personal data processed by its CSP on its behalf and for its purposes." It implies that organizations must ensure their CSPs comply with local regulations and build their cloud infrastructure in accordance with PDPA guidelines.
Cloud security
Another important question is security. It is evident that the cloud infrastructure cannot offer the same level of security as offline environments, and cloud breaches are not uncommon. Nevertheless, cloud solutions can provide distinct advantages that enhance overall security and offer additional benefits for digital forensics:
- Identity and access management (IAM): Cloud platforms provide robust Identity and Access Management tools. IAM allows organizations to control who can access their resources and data, ensuring the chain of custody for the evidence. This level of control is often more sophisticated and efficient than what is achievable in traditional offline settings.
- Read-only storage: Cloud environments enable the implementation of read-only storage, which restricts data from being altered or deleted once it is stored. This feature can be particularly valuable in preserving the integrity of digital evidence, ensuring that it remains unchanged throughout the investigation process.
- High availability and disaster recovery: Cloud environments often provide high availability and disaster recovery options, ensuring that critical data and services remain accessible even in the face of unexpected disruptions or catastrophic events. This service further enhances the resilience and reliability of cloud-based solutions for digital forensics.
- Logging and alerts: Cloud platforms offer comprehensive logging and alert mechanisms. These tools provide real-time visibility into activities and events within the environment. Security logs can be monitored for unusual or suspicious activities, triggering immediate alerts if any anomalies are detected. This proactive approach to security monitoring can help mitigate potential threats quickly and effectively. Needless to say, event and access logs are much harder to tamper with than registries in a physical forensic lab.
Cloud types and service providers
What are the options for establishing a forensic lab in the cloud? Today's cloud service providers offer several configurations within their cloud ecosystems:
- In a public cloud environment, users share hardware, storage, and network resources with other organizations or cloud "tenants".
- A private cloud is dedicated exclusively to one business or organization. This option offers greater control, security, and customization over computing resources.
- Hybrid cloud solutions combine elements of both public and private clouds to cater to different services or data needs. This approach provides flexibility and scalability.
- The most interesting and relatively new concept is the government cloud. It typically only hosts public sector organizations and adheres to specific security standards set by the local government. Particularly, government cloud servers are physically located within the country.

The government cloud combines the advantages of cloud computing with strict security standards, and it can be the answer to the "no internet" requirement for DFIR labs. Here are some examples of such services:
- USA: AWS GovCloud (US), Google for Government
- UK: Oracle Cloud for UK Government & Defence, MS Azure UK G-Cloud
- EU: Oracle EU Sovereign Cloud
- Germany: Bundescloud (government-hosted and maintained)
- Israel: Project Nimbus (in cooperation with Amazon and Google)
- Singapore: Government Commercial Cloud (GCC)
In many countries, the public sector already uses government cloud solutions, making it possible for law enforcement agencies to integrate into existing infrastructures.
What about DFIR tools?
The next important question is whether forensic tools are ready to move to the cloud. Speaking about Belkasoft, the answer is "yes". Belkasoft X can run on Windows-based virtual machines deployed in cloud environments and supports analyzing images stored in Amazon S3 buckets.
The latter feature comes in handy when you use Amazon or other compatible cloud services to store and share acquired evidence. It enables you to access forensic images and memory dumps right from the tool, saving the time required to download data to your workstation.
Here is how you can use Belkasoft X to analyze an image in the cloud:
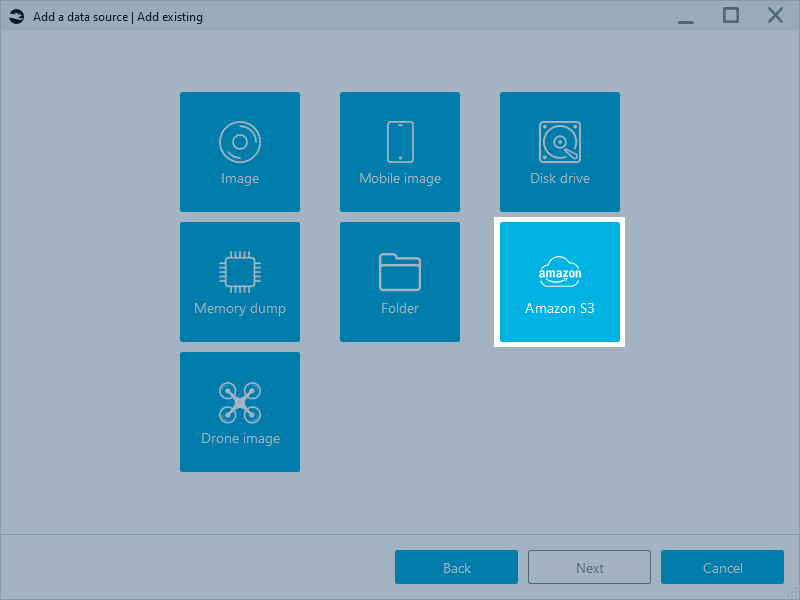
- Create a case and start adding a data source. On the case dashboard, click Add data source and select Add existing → Amazon S3.
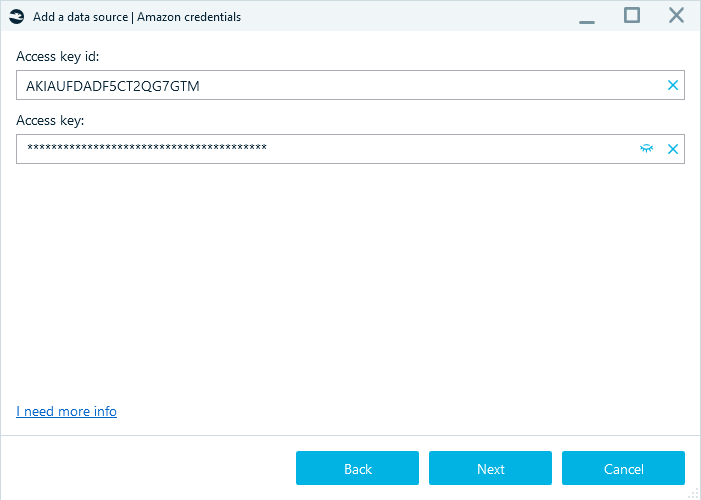
- Enter the access key to the cloud storage:
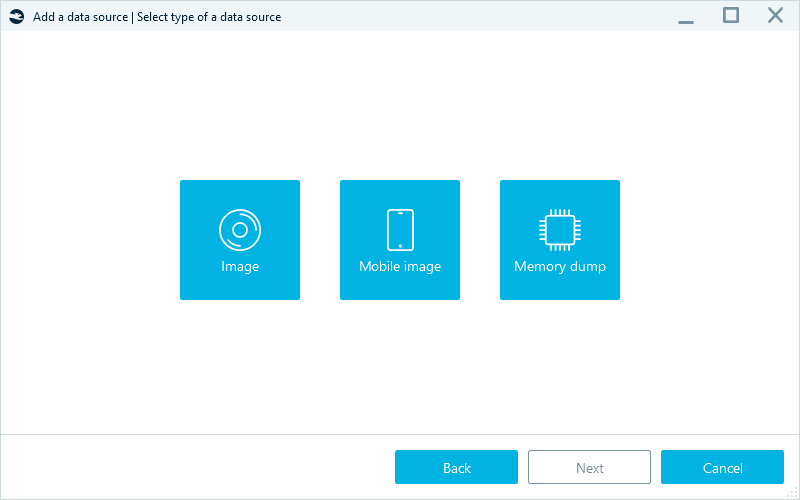
- Select the type of the data source you want to analyze:
- Navigate to and select the required item:
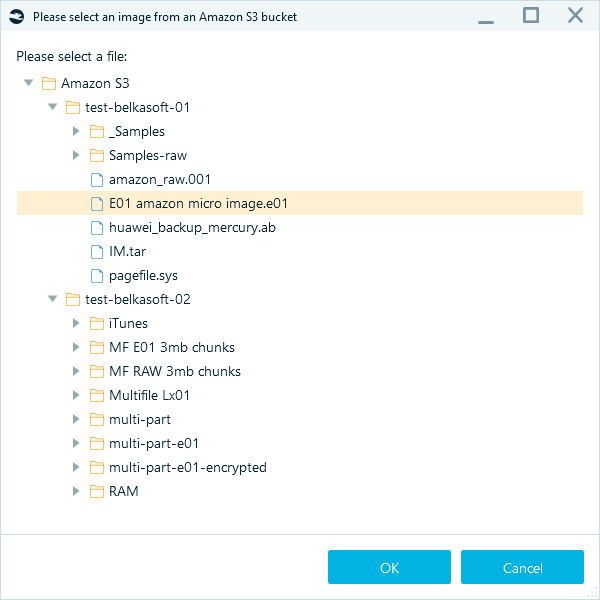
- Belkasoft X displays the selected data source. Click Next, and in the following windows, select the necessary options for your analysis.
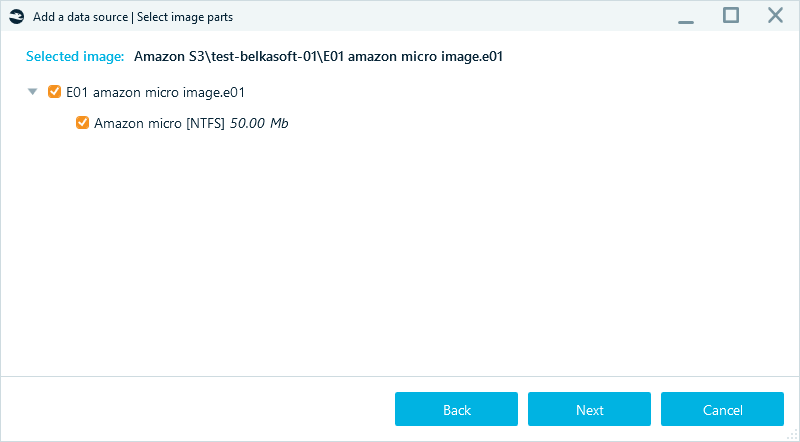
When Belkasoft X completes the analysis, you can examine the artifacts and file system and perform all your digital forensics or cyber incident response tasks as you do on locally stored images.
It is worth mentioning that Belkasoft X will not download the entire image onto your hard drive: at each point in time, it will only work with a small portion of the data being analyzed right now. It means that the data source resides in the cloud, and your Belkasoft case does not occupy valuable storage on your lab machine.
Working in a cloud environment
Now, let us explore how you can implement the advantageous features of the cloud for your digital investigations.
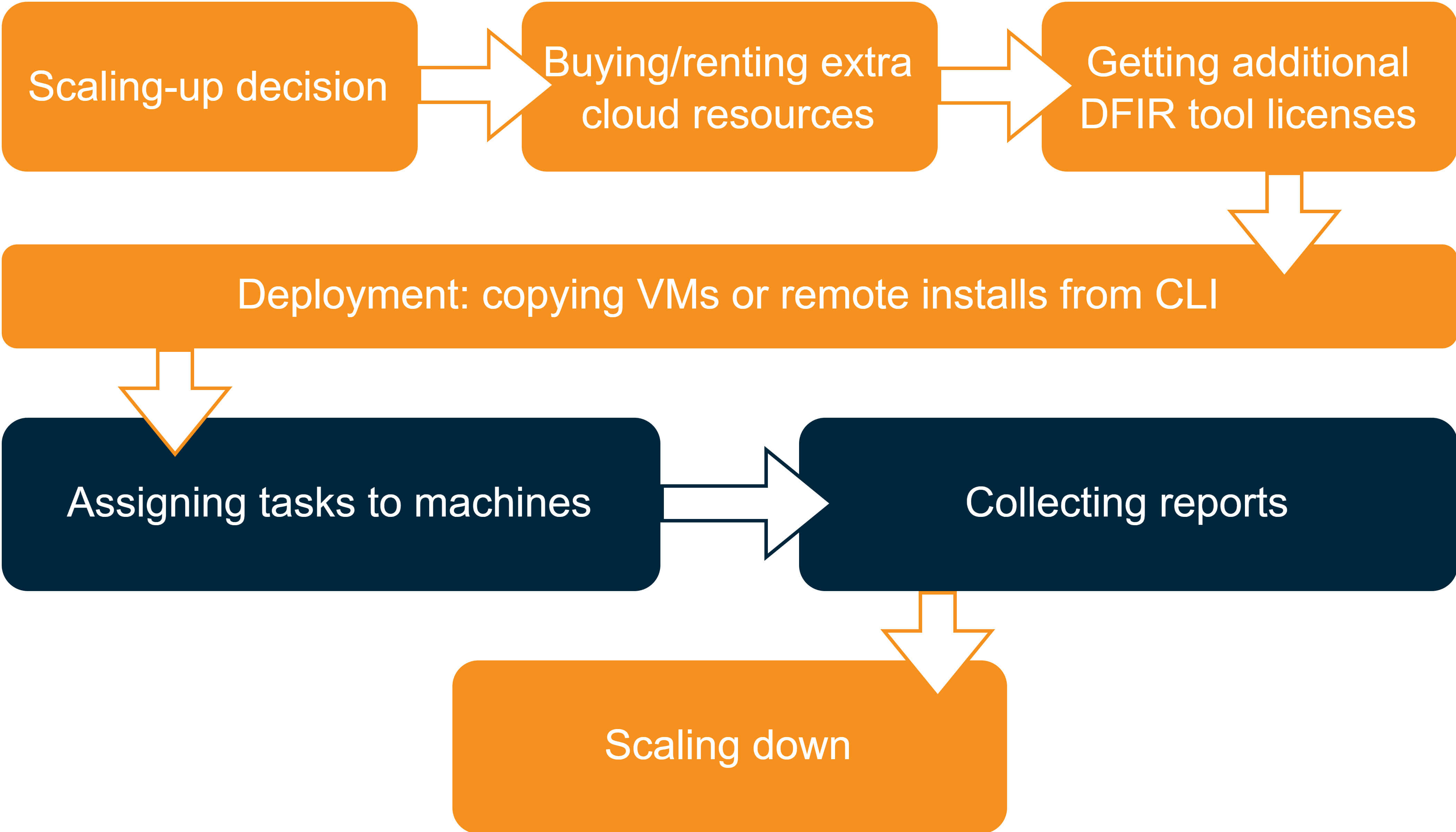
Imagine a scenario where you are faced with a data-intensive and time-sensitive case, and you need more resources to process it within the given timeframe or store all the evidence. How can you achieve this task working in a cloud-based DFIR environment?
- You decide to scale up and request additional resources from your cloud provider for your lab. Instead of purchasing them outright, you can opt to rent cloud resources. After all, not every case demands substantial storage and computing capacities.
- Next, you get extra tool licenses. For instance, with Belkasoft X, you do not need an additional dongle for this—you can add more users to your network dongle by updating just a single file on a single computer.
- Then, you deploy your digital forensic tools onto the new cloud computers. One approach is replicating an entire virtual machine image if you have a standardized image with all the pre-installed software. Alternatively, using Belkasoft X, you can run silent installation with automated licensing via the command line.
- After that, you proceed to assign tasks to the machines. It is up to you how you divide them, whether by data source or type of analysis. If you are using Belkasoft X, you can also leverage automation features to expedite your work.
- Finally, once the processing is complete, you collect the reports.
- If necessary, you can then choose to scale down. This process involves reducing the number of cloud nodes and storage volume being used and moving the data evidence to cold storage, which is typically more cost-effective.
Conclusion
Embracing the cloud can be a game-changer for forensic labs when dealing with the growing number of devices and their storage demands. Before implementing it for your lab, you first need to thoroughly study local rules and regulations to determine what you can and cannot store and process in the cloud. Keep in mind the government cloud option, as it is typically more secure and is vetted for working with sensitive data.
It might take some time and effort to get cloud-based DFIR labs up and running. Still, in the long run, all these investments will pay off by making investigations faster and smoother, reducing the number of pending cases, and ultimately, supporting the pursuit of justice.
P.S. You can help Belkasoft better understand your DFIR lab requirements by taking a 3-minute survey.
Did you like the article?
See also
- Another method to solve the data abundance problem is automation. Belkasoft has a series of articles on this approach