One of the biggest issues of modern digital forensics is the abundance of data. It is not rare to see a computer hard drive with 1Tb capacity, we have become used to hard drives with equal or greater capacity. However, smartphones can even have as much as 1Tb storage now! Given that modern DFIR cases can easily have a handful of devices, it is not uncommon to have a few dozen terabytes of data within a single case.
The problem that is commonly faced, is that it takes time to complete the analysis of all this data and to perform various preliminary work such as keyword indexing and searching against specific keyword files, file hash calculations, and searching against specific hashset databases. Additional preliminary steps may also include performing regular expression searches such as 'all credit card numbers', detecting specific types of graphics, and finding encrypted files and volumes. Many modern tools can easily take weeks for these tasks alone, which inevitably delays an investigator's work and causes growing case logs.
This is where automation can help.
Over the past few releases of Belkasoft X—our leading digital forensic, cyber incident response, and eDiscovery product—we introduced many improvements to our implementation of this unattended execution.
What can be automated with Belkasoft X
Now, Belkasoft X users can perform multiple tasks while running the product in the CLI (command line interface) mode:
- Create a case or open an existing one
- Add a new data source to the case
- Acquire a data source from a hard drive or through a Tableau TX1 device
- Analyze the data source using a predefined analysis profile, which can include:
- All or selected artifact analysis—computer, mobile, cloud, memory etc.
- File and data carving
- Hash calculation
- Hashset match searching
- YARA rule and Sigma rule searching
- AI (Artificial Intelligence)-based detection of guns, explicit images, skin, faces, and texts in media files
- Text extraction from pictures using OCR (optical character recognition)
- Video keyframe extraction and analysis
- Create a report in one or multiple formats at once, including PDF, HTML, CSV, Excel, Word and others
- Export data to numerous formats such as Semantics 21, RSMF (Relativity Short Message Format), and Project VIC
- And perform additional types of processing, which Belkasoft X also allows to perform within its User Interface
Command line configurator
The number of options available for editing the configuration JSON file, makes it a bit complicated to traditionally complete this task manually. This is why the Belkasoft team has developed a special configurator tool, which allows a user to generate options with just a few clicks of a mouse:
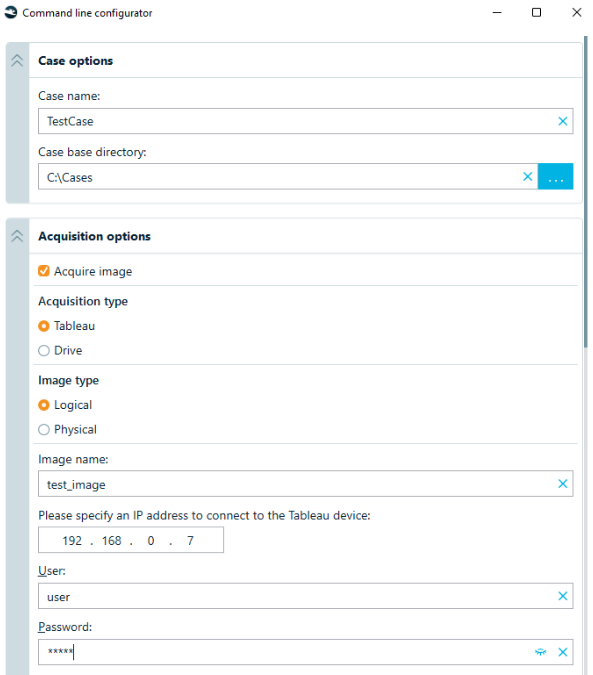
The command line configurator interface (partial)
As a result, you can generate a configuration file which you can then feed to Belkasoft X to run completely autonomously.
All that must be completed is simply running a special batch file that is included with your Belkasoft X package as shown below:
Belkasoft.Cli.bat -optionsPath="config.json"
The config.json file is your options file that is generated by the configurator tool.
Performance gain and integrations
The possibility to run the product unattended from the acquisition to reporting opens a wide variety of improvements in both analysis and performance:
- An investigator may work with another case on another machine, while the first computer analyzes a case
- It is made easier to start such analysis without touching the computer by sending a command line execution via Windows remote execution. You can spread the workload across all of your computers without leaving your main one!
- As a natural improvement of the previous point, you can employ the power of the cloud, whether public or private. Given that Belkasoft can both run in a cloud instance and analyze images stored in and Amazon S3-compatible cloud, your capabilities are endless
- Since Belkasoft allows for the export of data in common formats, you can orchestrate numerous tools to work as one workflow. One of our customers analyzes data sources with Belkasoft X, exports media files into JSON, and then continues analysis in the Griffeye tool
Side effects
Naturally, when using an unattended execution, one loses the possibility of interaction with the software. In particular, if a partition is detected as encrypted, while in the Belkasoft X user interface, it will provide a hint as to what decryption file or password to use. Similarly, if a database or an artifact is encrypted, the user interface can show a hint and allow the examiner to see more details. The command line tool does not have such an option (it could, but the whole idea is not to ask any questions). This means that all such tasks are automatically canceled by the product and you will have to process them, if needed, manually afterwards, which is still a very simple process.
Other automation in Belkasoft X
Apart from the command line interface, Belkasoft X has an API (application programming interface). This interface, however, is aimed to be used by customers with a knowledge of C# or C++ programming languages and thus is more complicated than the automation via the command line. Having said so, the API is much more flexible and allows for many more scenarios than the command line, which has a fixed set of options.
The best thing in Belkasoft X Automation
What makes our automation special? Unlike the competition, our automation is not being sold as a separate product. If you already have Belkasoft X license, you get the automation completely free! This is the same tool, which can be run both with and without Graphical User Interface (GUI) and there is no need to pay us twice!
Conclusions
Automation and, particularly, unattended execution provides a DFIR examiner with multiple benefits, including parallel work on multiple machines, interfering only at the moment when the preliminary processing is complete, employing cloud capacities, and orchestrating complex cross-tool workflows.
Starting with the X Forensic edition, Belkasoft X comes with the built-in automation, which again does not imply any extra costs. You can easily configure multi-step workflows with a simple configurator tool included within the product package.
Did you like the article?
See also
- Automation with Belkasoft X: Orchestrating Belkasoft X and Griffeye DI Pro
- Automation with Belkasoft X: Export for Amped FIVE
- Automation with Belkasoft X: Installation and licensing
- Automation with Belkasoft X: Putting pieces together
- NIST tested Belkasoft support for SQLite data recovery
- Why Belkasoft should be your tool of choice for Mobile Forensics
- 5 bloopers of a digital forensic investigator