Over the past several years there has been a rapid increase in the number of mobile devices with mobile malware and spyware installed on them. Who could be behind this? It could be a jealous partner suspecting their spouse of being unfaithful. It could be a business partner trying to catch their suspected associate red-handed. It could be hackers trying to steal money. Belkasoft Evidence Center has a feature that allows to quickly detect mobile malware or spyware installed on a smartphone. This article is focused on this very feature.
Signs indicating malware or spyware
There are a number of signs leading to suspicion that a phone has malware or spyware installed on it:
- Mobile malware and spyware may considerably reduce the performance of a mobile device: applications will be slow to open; you will have to click on a contact several times before the call comes through; you cannot immediately slide the icon to reply to an incoming call, etc.
- Strong echo is present during calls.
- The smartphone battery runs low faster than usual.
- Internet traffic usage increases.
- A new application appearing on the list: sometimes you may find an unknown application icon on the smartphone’s home screen.
- If the device has the data transfer icon that uses arrows to indicate data being transferred via the Internet, you may notice that this icon is activated during calls, while receiving SMSes and so on.
Detecting mobile malware and spyware with Belkasoft
There are several steps that help detection of malware and spyware with Belkasoft.
- Create a physical dump or a mobile backup of the mobile device.
- Analyze the data extracted from the physical dump or mobile backup of the mobile device.
- Perform an additional analysis for malware and spyware.
Creating a physical dump or a mobile backup
Belkasoft Evidence Center allows creating physical dumps or mobile backups of Android and iOS devices. The example below shows creation of a physical dump of an Android smartphone. After you have launched Belkasoft Evidence Center and created a new case, the program will prompt you to choose a data source. In order to create a physical dump of a mobile device, click on the Mobile button located on the left under the Acquire and analyze section of the Add data source window.
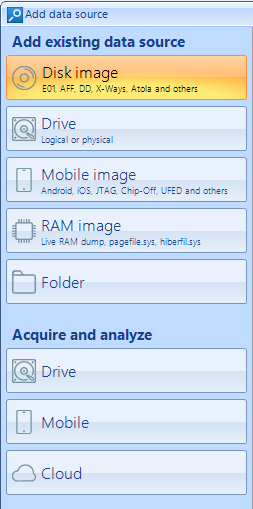
In the next window, set the switches Analyze data source for artifacts, Run hashset analysis, Run cross-case analysis in a position you require and click the Android button.
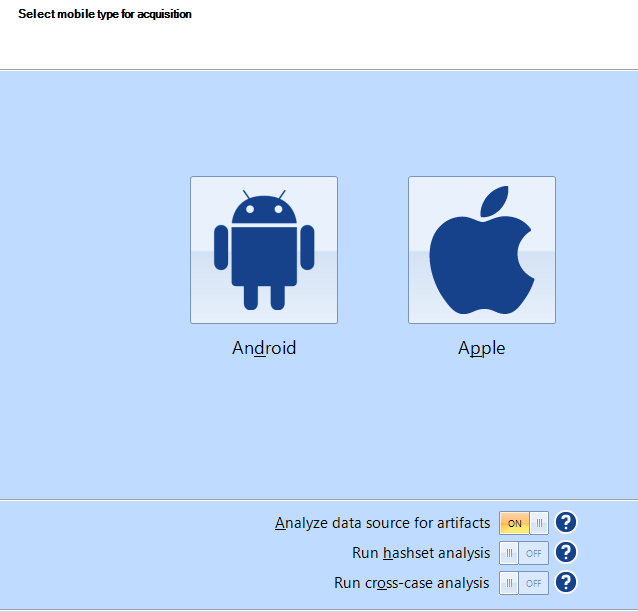
Next window will show the information about the connected device.

It will also show what acquisition methods are available.
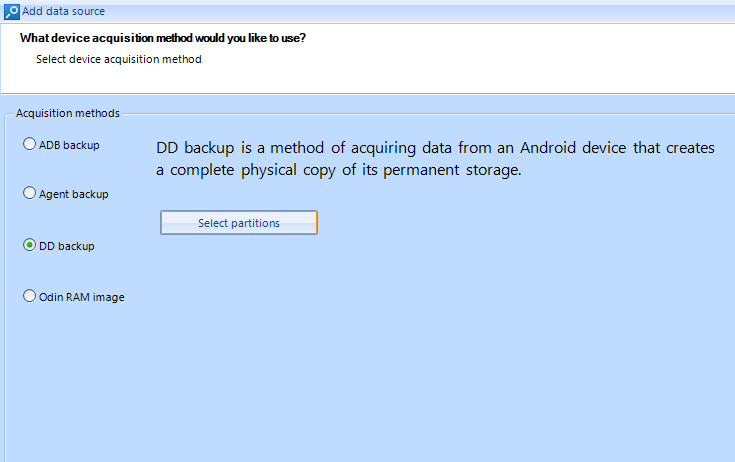
If you press the Select partitions button opposite to DD backup method, the window containing the list of partitions will appear. There you can select the exact partitions you want to copy from the mobile device. It is recommended to copy all of the partitions. You can also copy the contents of RAM (partition’s name: zram0). Copying RAM may be useful for a fileless malware investigation. This type of malware can only be found in mobile device’s RAM, it cannot be detected by copying the data from other partitions. User data is located on the partition called ‘Userdata’ (or ‘Data’). It might be best to copy this partition separately if the device is encrypted.
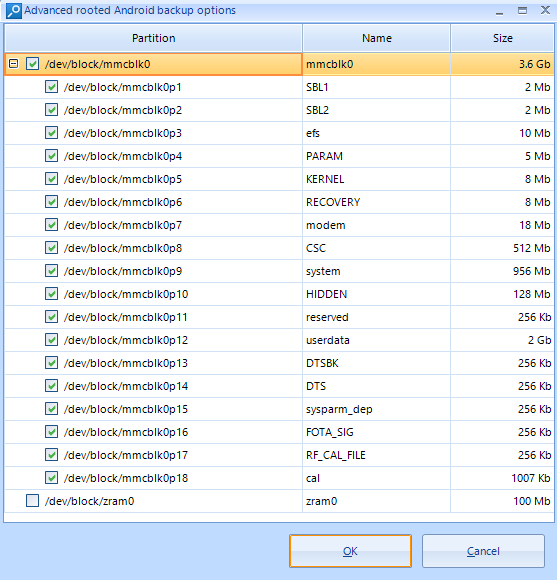
After you have selected the partitions, click OK and then Next. The software will start creating a physical dump of your mobile device.
Analyzing the data extracted from a physical dump or a mobile backup
After a physical dump has been created, you can proceed to analyze it. To do so choose the artifacts you would like to analyze in the Add data source window and click Finish.
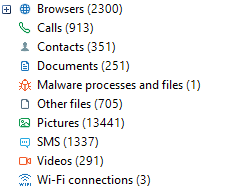
After the analysis is finished, all of the found artifact will be listed in the main window of the product.
Detecting malware and spyware
The executive files in the Android OS have the ‘.dex’ and ‘.jar’ extensions. Files with the extension ‘.apk’ are the installation files, which are quite familiar to the Windows OS users.
Belkasoft Evidence Center allows you to detect malware and spyware using two methods.
Method 1: Calculating hash values of the suspicious files and checking these hashes at Virustotal.com
To use this method, go to the File System window in Belkasoft Evidence Center. Choose the file of interest and right-click it. Choose the Run hashsets analysis… option in the menu.
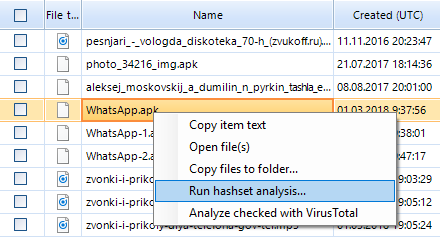
Choose the necessary analysis settings in the Hashset analysis options window.
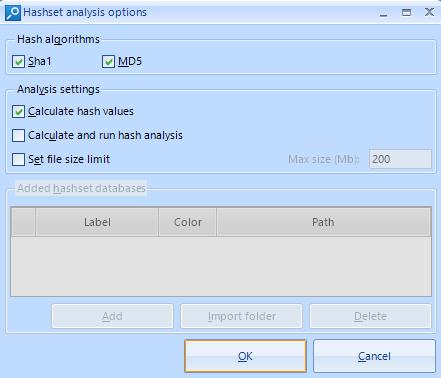
After the hashes are calculated, the results will be shown in the columns ‘Md5’ and ‘Sha1’ for the selected files. If you go to the Virustotal.com website and enter the hash value in the ‘SEARCH’ field there, you will see the results for a particular file.
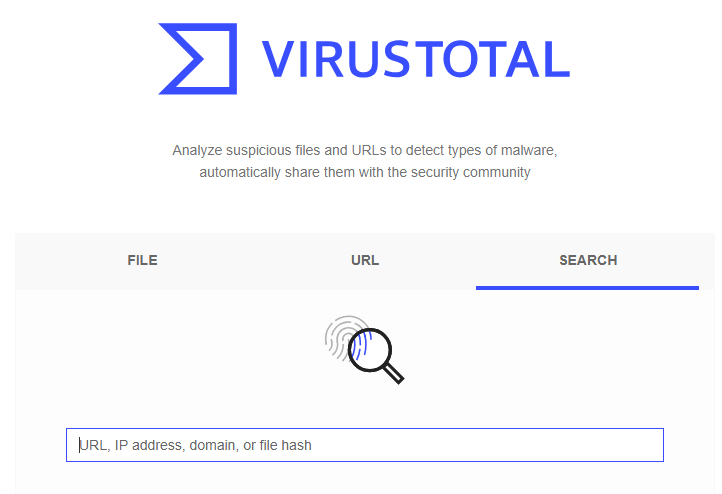
If a similar file has already been uploaded to this website, the result of its analysis will be shown. The following result was shown for ‘Whatsapp.apk’ file found in the ‘Download’ directory.

If we compare this information with other data extracted from this mobile device, it becomes obvious that the device’s owner entered the phrase ‘Whatsapp download’ in Google on the 3rd of January 2018. He then went to Google Drive and downloaded this file. The piece of malware was installed on the smartphone. You can get all this information using the Timeline window in Belkasoft Evidence Center.
Method 2: Belkasoft Evidence Center can automatically check any suspicious files at the Virustotal website
To use this method, first you need to register at the Virustotal website and get an API key (it is available in the user’s personal cabinet after the registration).
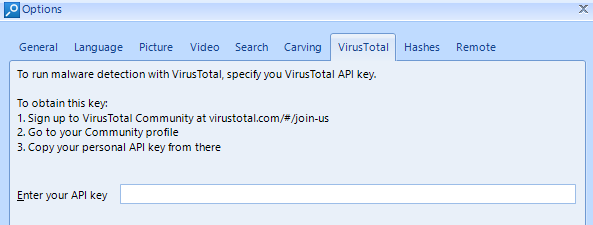
Then you need to customize Belkasoft Evidence Center. After launching the software, click on the Tools menu and choose Options. Enter the value of your API key in the VirusTotal tab and click OK.
To detect malware and spyware, choose the file you want to analyze and right-click it. Choose Analyze checked with VirusTotal option in the menu.
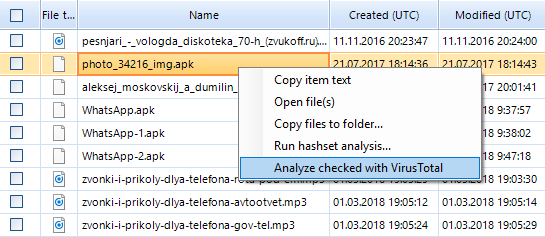
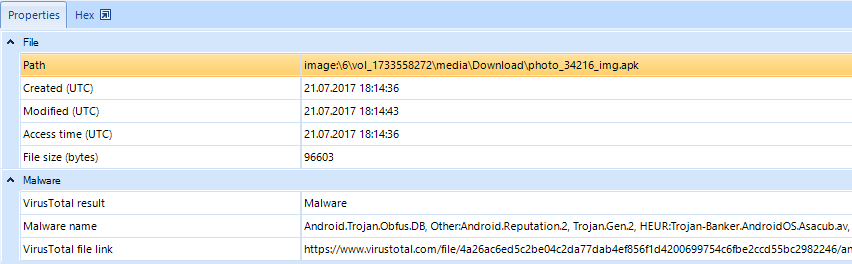
After the analysis has been completed, the information about the analysis result of the selected file from the Virustotal website will appear in the lower section of Belkasoft Evidence Center window along with the files properties.
Additional analysis of the detected malware or spyware
Malware or spyware detected on the analyzed mobile device can be additionally investigated in order to find out its functionality, to determine the command and control server that hackers used to control the software and so on. Unfortunately, this analysis has to be performed manually.
Developers of malware and spyware try to encumber the job of the reverse engineers by using such methods as obfuscation and encryption. Decrypted files of malware or spyware applications could only be found in the RAM of the device. That is why the Belkasoft Evidence Center's feature that allows to acquire the RAM image of the analyzed device makes the job of reverse engineers so much easier.
Let us review an example of data acquired during the analysis of a mobile bank Trojan, whose installation file ‘WhatsApp.apk’ was found on the investigated device.
Permissions:
<uses-permission android:name="android.permission.READ_CONTACTS" /> <uses-permission android:name="android.permission.WRITE_SMS" /> <uses-permission android:name="android.permission.GET_TASKS" /> <uses-permission android:name="android.permission.READ_SMS" /> <uses-permission android:name="android.permission.WAKE_LOCK" /> <uses-permission android:name="android.permission.USES_POLICY_FORCE_LOCK" /> <uses-permission android:name="com.android.browser.permission.READ_HISTORY_BOOKMARKS" /> <uses-permission android:name="android.permission.INTERNET" /> <uses-permission android:name="android.permission.RECEIVE_SMS" /> <uses-permission android:name="android.permission.READ_PHONE_STATE" /> <uses-permission android:name="android.permission.SYSTEM_ALERT_WINDOW" /> <uses-permission android:name="android.permission.CHANGE_NETWORK_STATE" /> <uses-permission android:name="android.permission.RECEIVE_BOOT_COMPLETED" /> <uses-permission android:name="android.permission.CHANGE_WIFI_STATE" /> <uses-permission android:name="android.permission.SEND_SMS" /> <uses-permission android:name="android.permission.CALL_PHONE" /> <uses-permission android:name="android.permission.ACCESS_WIFI_STATE" /> <uses-permission android:name="android.permission.VIBRATE" /> <uses-permission android:name="android.permission.ACCESS_NETWORK_STATE" /> <uses-permission android:name="android.permission.WRITE_EXTERNAL_STORAGE" /> <uses-permission android:name="android.permission.WRITE_SETTINGS" /> <uses-permission android:name="android.permission.READ_EXTERNAL_STORAGE" />
The commands that are executed by the application, which in turn gets the corresponding commands from the server:
if(arg2.equals(Dispatcher.decryptString(0, Dispatcher.decrTable[53]))) { // #conversations
return new ConversationsTask();
}
if(arg2.equals(Dispatcher.decryptString(5, 0))) { // #contacts
return new ContactsTask();
}
if(arg2.equals(Dispatcher.decryptString(8, -Dispatcher.decrTable[106]))) { // #calls
return new CallsTask();
}
if(arg2.equals(Dispatcher.decryptString(9, 0x77))) { // #apps
return new AppsInfoDataSender();
}
if(arg2.equals(Dispatcher.decryptString(8, 0x73))) { // #bhist
return new BhistTask();
}
if(arg2.equals(Dispatcher.decryptString(5, Dispatcher.decrTable[0x4F]))) { // #interval
return new IntervalTask();
}
if(arg2.equals(Dispatcher.decryptString(4, 0x84))) { // #intercept
return new InterceptTask();
}
if(arg2.equals(Dispatcher.decryptString(9, 0x7B))) { // #send
return new SendTask();
}
if(arg2.equals(Dispatcher.decryptString(9, 81))) { // #ussd
return new USSDTask();
}
if(arg2.equals(Dispatcher.decryptString(0, Dispatcher.decrTable[0]))) { // #send_contacts
return new SendContactsTask();
}
if(arg2.equals(Dispatcher.decryptString(7, 61))) { // #server
return new ChangeServerTask();
}
if(arg2.equals(Dispatcher.decryptString(3, Dispatcher.decrTable[39]))) { // #check_apps
return new CheckAppsTask();
}
if(arg2.equals(Dispatcher.decryptString(4, 110))) { // #send_mass
return new SendSMSTask();
}
if(arg2.equals(Dispatcher.decryptString(9, Dispatcher.decrTable[109]))) { // #lock
return new LockTask();
}
if(arg2.equals(Dispatcher.decryptString(7, 67))) { // #unlock /
return new UnlockTask();
}
if(arg2.equals(Dispatcher.decryptString(5, 55))) { // #makecall
return new MakecallTask();
}
if(arg2.equals(Dispatcher.decryptString(6, 101))) { // #openurl
return new OpenURLTask();
}
if(arg2.equals(Dispatcher.decryptString(6, Dispatcher.decrTable[19]))) { // #hooksms
return new HookSMSTask();
}
if(arg2.equals(Dispatcher.decryptString(3, 77))) { // #selfdelete
return new SelfDeleteTask();
}
Conclusion
Belkasoft Evidence Center helps you to detect mobile malware or spyware on an analyzed mobile device. Moreover, the data extracted from a mobile device helps the investigator to understand how the investigated device was infected.
More details on Belkasoft Evidence Center
- General info: https://belkasoft.com/x
- Free fully functional trial: https://belkasoft.com/trial
- Sign up to free online webinar: https://belkasoft.com/webinar (NEW: Webinars in Spanish and German are now available!)
- Quote request: https://belkasoft.com/quote
- Belkasoft articles on various forensic topics: https://belkasoft.com/articles. One of useful articles to read is "SQLite forensics" article, explaining some of concepts from this article
- Belkasoft customers: https://belkasoft.com/customers
- BEC tutorials: https://belkasoft.com/tutorials
- Academic relations: academic@belkasoft.com