Skype Forensics Postmortem: Why DFIR Specialists Should Still Care
Microsoft will officially retire Skype on May 5, 2025. Once a dominant platform in online communication, Skype is now being replaced by Microsoft Teams. While this reflects a broader shift in enterprise communication, it does not make Skype forensics any less relevant. Legacy data from Skype may still surface in investigations involving long-term employees, archived backups, or older devices. That is why forensic tools must remain compatible with legacy applications.
In this article, we will explore:
- Why Skype still matters for forensic investigations
- Where to find Skype forensic artifacts and how to extract them
- Challenges involved in analyzing legacy data
- How Belkasoft X helps you work with outdated applications like Skype
Deprecated and legacy software can still hold crucial evidence. Choosing the right tool ensures you do not miss it. Read on to explore how Belkasoft X can extract valuable evidence from Skype data, even after the platform is decommissioned.
Why Skype's legacy still matters
Launched in 2003, Skype became a cornerstone of internet-based communication. At its peak, it supported hundreds of millions of users and generated vast volumes of digital data—text messages, voice and video calls, shared files, and contact records.
Although Microsoft allows users to export their Skype data before shutdown, those exports will not include deleted records and may not provide reliable timestamps or other metadata essential for forensic timelines. When possible, investigators should rely on data remaining on dated systems.
Image by Unsplash
From a forensic perspective, legacy Skype artifacts continue to be valuable sources of evidence. They can help you:
- Reconstruct conversations
- Map user relationships
- Establish communication timelines
- Recover exchanged files or media
With billions of call minutes logged annually and hundreds of millions of users over two decades, the platform has left behind a large footprint. Many of these records are still available on older devices, and in many cases, they remain relevant.
Many organizations continue to rely on aging hardware due to budget constraints, software dependencies, or deferred upgrade cycles. As a result, DFIR specialists frequently encounter legacy systems where Skype is still installed and where evidence may still reside.
Furthermore, despite the individual users' shift towards newer messaging platforms like WhatsApp and Telegram, some devices may still contain long-forgotten Skype installations and conversations having evidential value.
Where to find Skype data
Although Microsoft offers data export tools before deprecation, exported files may not include deleted records, timestamps, or metadata critical to forensic timelines. Capturing data directly from its source on the target system, without using intermediate formats or tools that might alter it, remains highly important.
Skype predominantly saves its data in a central location called main.db or skype.db. It is an SQLite database found on both Windows and macOS computers, as well as mobile devices running Android or iOS. This file typically contains:
- Chat logs: The textual content of conversations.
- Call history: Details about incoming and outgoing calls, including timestamps, duration, and participants.
- File transfers: Records of files sent and received through Skype.
- Contact lists: Information about added contacts.
Depending on the configuration, Skype may also store voicemail, SMS data, geolocation metadata, and images shared through the interface.
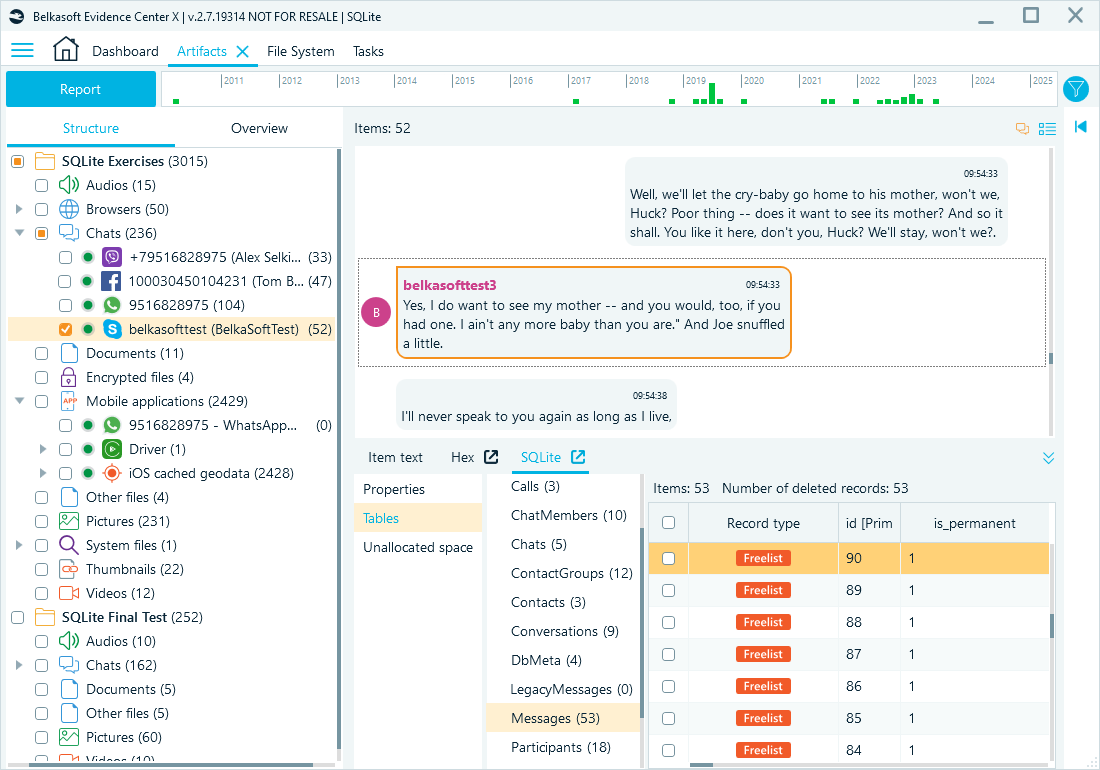
Skype chats extracted by Belkasoft X
Additional files and structures may contain recoverable data:
- main.db-journal: A journal file used by SQLite for transactional integrity.
- Freelists and unallocated space within the database: Areas within the SQLite file that may contain remnants of deleted data.
- User profile folders: Directories containing configuration files and potentially shared media
Below is a breakdown of common locations for different systems. Locations may vary by operating system, Skype version, and user preferences.
Windows
| Version | Path | Contents |
|---|---|---|
| Older Skype | %appdata%\Skype\<SkypeUsername>\ | main.db, config files |
| Newer Skype | %appdata%\Microsoft\Skype for Desktop\ | skype.db, config files |
| Skype UWP | %localappdata%\Packages\Microsoft.SkypeApp_*\LocalState\<SkypeUsername>\LocalCache\Roaming\Microsoft\Skype for Store\ | skype.db, config files, cacheLogs are mostly cloud-based |
| Skype for Business |
%LocalAppData%\Microsoft\Office\*\Lync\ Registry: HKCU\Software\Microsoft\Communicator, HKCU\Software\Microsoft\Office\*\Lync |
Chat history (Outlook), cache, logs, registry config |
macOS
| Version | Path | Contents |
|---|---|---|
| Older Skype |
~/Library/Application Support/Skype/<SkypeUsername>/ ~/Library/Preferences/com.skype.skype.plist ~/Library/Caches/com.skype.skype/ |
main.db, chatmsg256.dbb, config files, cache |
| Newer Skype | ~/Library/Application Support/Microsoft/Skype for Desktop/ | skype.db, cache |
| Skype for Business | ~/Library/Containers/com.microsoft.SkypeForBusiness/ |
Logs: Data/Library/Logs/… Database: Data/Library/Application Support/.../DataStore.sqlite |
Linux
| Version | Path | Contents |
|---|---|---|
| Older Skype | ~/.Skype/<SkypeUsername>/ | main.db, other artifacts |
Android
| Version | Path | Contents |
|---|---|---|
| Skype App |
/data/data/com.skype.raider/ /data/data/com.skype.insiders/ |
main.db, shared prefs, cache, files under files/, databases/, shared_prefs/ |
iOS
| Version | Path | Contents |
|---|---|---|
| Skype App | /var/mobile/Containers/Data/Application/<GUID>/Documents/.../Library/ | main.db, config files, logs, cache |
On iOS and Android devices, Skype data resides in the file system and is not saved in backups. Accessing it requires rooting or jailbreaking the device or using forensic acquisition tools.
You can also recover deleted Skype data by parsing SQLite internals, such as freelists and uncommitted journal records, or carving remnants from unallocated space. Tools with built-in support for SQLite structure recovery are essential for extracting these artifacts reliably.
The DFIR time warp: Challenges in analyzing deprecated software
Working with deprecated applications like Skype poses several challenges for DFIR professionals. Investigators must consider:
- Limited documentation: Once Microsoft deprecated Skype, official help will likely go to the archive, making it difficult to interpret artifacts created by older builds without community resources.
- Date interpretation difficulties: To interpret some data accurately, you may need to research how the application generates it under specific conditions. However, with Skype decommissioned, running live forensic tests is no longer possible, so you will have to rely solely on the evidence available or older research.
- Data format inconsistencies: Skype versions vary widely, and some older builds may use outdated database schemas, incompatible with modern tools.
To address these challenges, you need proper forensics software to recover Skype history, support outdated formats, parse SQLite thoroughly, carve deleted records, and maintain compatibility with legacy environments.
Belkasoft X: A legacy-aware DFIR solution
Belkasoft X is designed to support complex investigations involving legacy applications such as Skype. It provides advanced functionality for locating, parsing, and recovering artifacts, even from outdated or partially damaged sources. Belkasoft X supports:
- Direct parsing of the main.db file, including freelists, journal files, and unallocated space within the SQLite database. This enables recovery of deleted records that may still reside in slack areas.
- Carving of records from SQLite databases.
- Full extraction of chat content, contacts, call logs, geolocation data, and file transfers.
For mobile artifacts, Belkasoft X supports the Android APK downgrade method, which enables data acquisition from older app versions that may otherwise be inaccessible on modern Android systems. Additionally, it employs methods such as checkm8 and agent-based acquisition for obtaining Skype app data from iOS devices. Additional features include:
- Built-in SQLite, Hex, Plist, and Registry viewers
- Support for common disk image formats, including E01, Ex01, Lx01, and RAW
- A variety of mobile device acquisition options for Android and iOS devices
- Advanced carving and RAM analysis for volatile or deleted artifacts
Even years from now, Skype data may prove valuable in reopened cases, long-term audits, or criminal investigations. "Decommissioned" should not mean "lost." Belkasoft X's strong focus on historical compatibility ensures that legacy artifacts, including those from Skype, remain accessible and analyzable.
Its effectiveness in parsing cleared Skype databases, recovering deleted records, and carving SQLite data often exceeds that of more narrowly focused or general-purpose forensic tools.
Conclusion
Skype's retirement does not render its artifacts obsolete overnight. Digital forensics investigators, incident responders, and compliance teams will continue to encounter these sources, along with exported Skype data on devices and external storage.
Tools like Belkasoft X enable professionals to recover and analyze Skype artifacts from older and damaged data sources. Belkasoft's robust support for artifact extraction and analysis, advanced SQLite forensics features, and recovery of deleted records ensures that legacy data remains accessible.

