Abstract
Kik Messenger is a popular free messaging app for all major mobile platforms. Available for Android, iOS and Windows phone, Kik Messenger had a user base of more than 130 million users just a year ago. Today, the company claims over 200 million registered accounts, with another 250,000 users added each day. The messenger’s user base consists of teenagers and young adults. It is estimated that approximately 40 per cent of 13- to 25-year-olds in the United States are using Kik.
As a result, Kik Messenger becomes one of the forensically important messenger apps. With hundreds of millions of users communicating with Kik on daily basis, ignoring this popular messenger during an investigation may lead to missing important evidence. With Kik’s user base mostly consisting of teenagers and young adults, Kik messages can come especially handy when investigating cases of molesting.
Discovering Kik Messenger Evidence
Unlike many cloud-based messengers, Kik Messenger stores evidence in the phones in unencrypted offline databases, which makes it possible to access this information without knowing the user’s account authentication details. Both Android and iOS versions of Kik Messenger store information in SQLite format. These databases are located in the following folders:
Kik Messenger Android:
/data/data/kik.android/databases/kikdatabase.db
Kik Messenger iOS:
/root/var/mobile/Applications/com.kik.chat/Documents/kik.sqlite
While these databases store essentially the same information including contacts, text messages and attachments, the two databases have different internal structures.
What exactly is available to an investigator, and how can we get to that data? We will be using Belkasoft Evidence Center to automatically locate Kik Messenger databases stored in iOS and Android backups, process the binary format and extract available evidence.
Step 1: Locating Kik Messenger Databases
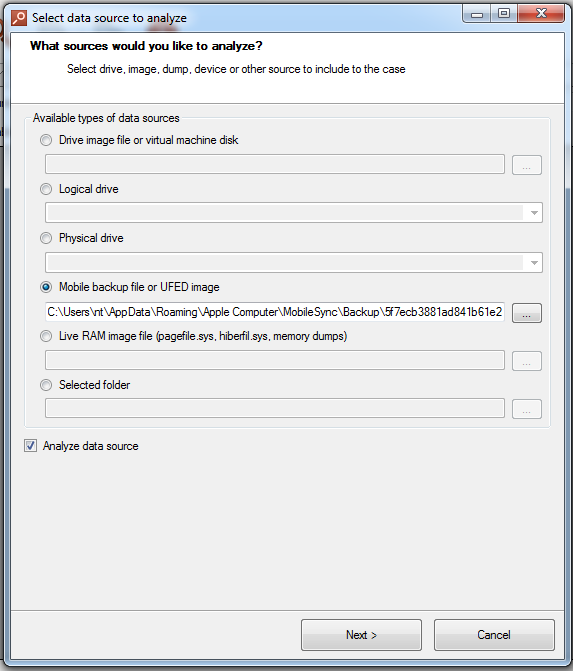
To locate Kik Messenger databases stored in iOS or Android backups (or UFED/chip-off dumps), we will extract them using Belkasoft Evidence Center. First, add the corresponding backup or image file as a source:
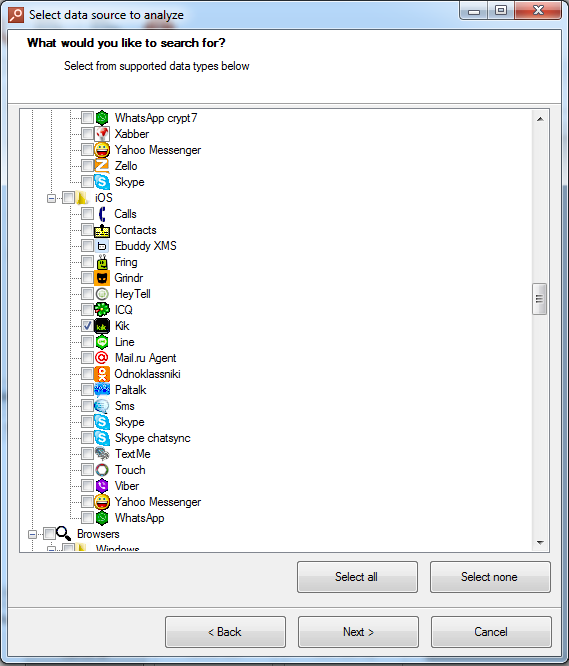
Next, make sure that Kik Messenger is selected in the list of available messengers. You can scan for all artifacts or just look for Kik Messenger evidence. For illustration purposes, we will uncheck everything except Kik:
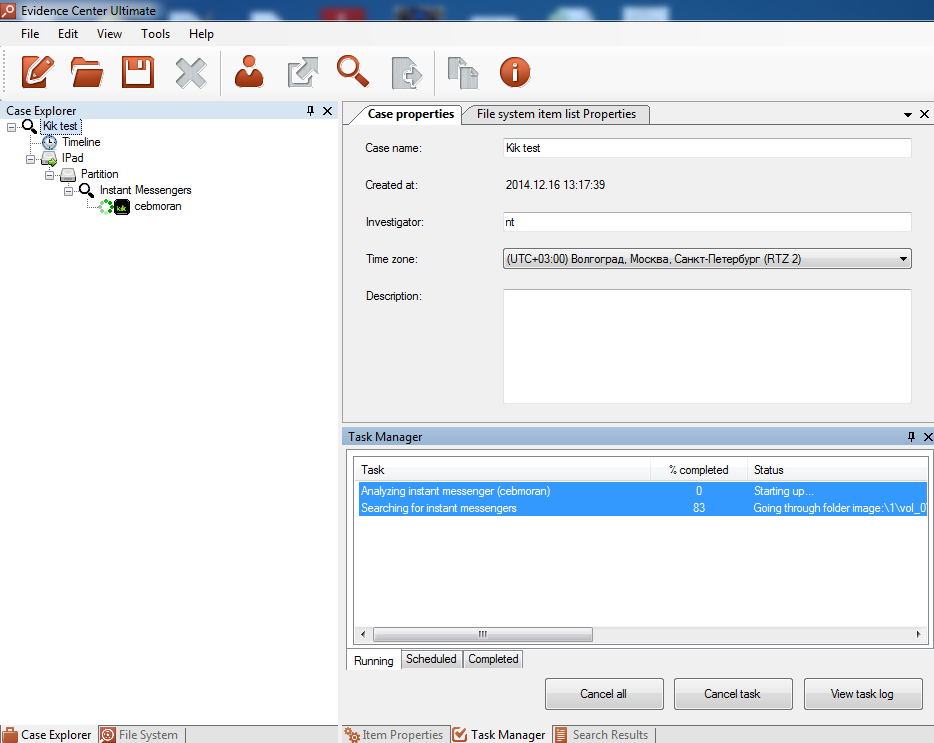
Start data extraction. After a few moments, you should see the number of discovered artefacts growing:
Locating and parsing Kik Messenger databases is extremely fast with Evidence Center, so you will be able to access all collected evidence in a matter of seconds.
Step 2: Analyzing Kik Message History
Kik Messenger stores several types of data: text messages, attachments (can be pictures or files in any format) and contacts. It is most likely that you will discover the most valuable evidence in the Messages section:
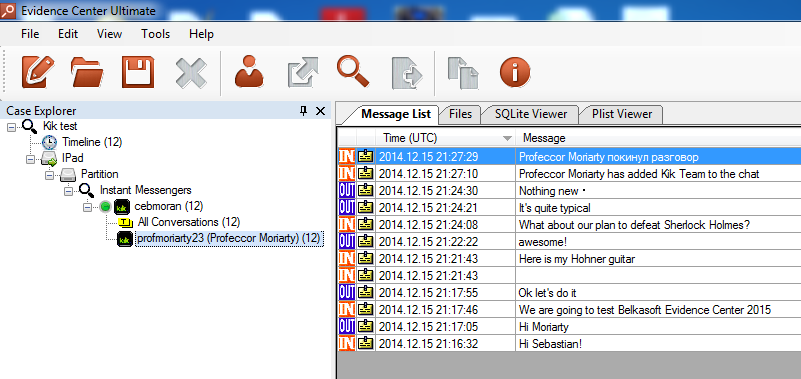
As Kik stores all of its data in SQLite format, unencrypted, there is a good chance that the entire messaging history will be recovered. By analyzing messages, you will automatically see all messages sent and received, attachments, date and time, as well as the user name of the remote party.
If you are interested specifically in attachments or contacts, you may access these by clicking on a corresponding control. You can also extract and save the attachments to your computer to have easier access to them in the future.
Step 3: Recovering Deleted Kik Messages
Kik Messenger makes extensive use of SQLite, just like most other Android and iOS messengers. While the SQLite format is well documented, there are certain things that only few forensic tools – one of them is Belkasoft Evidence Center – can do to SQLite databases in order to retrieve all available (and some unavailable) evidence.
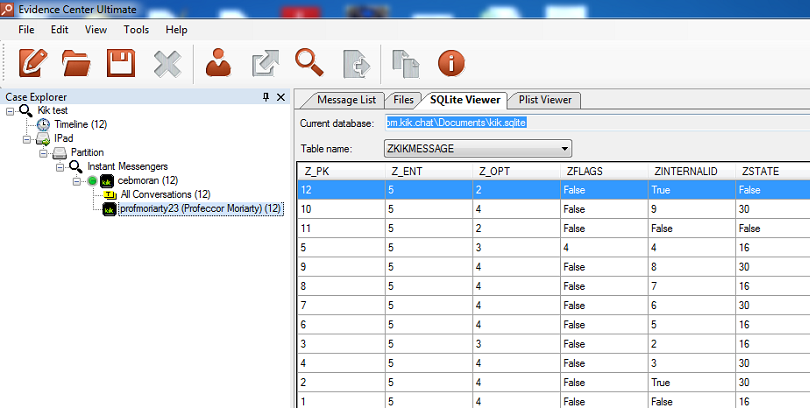
SQLite Freelists
When analyzing Kik Messenger databases acquired from Android or iOS devices, you may have a database containing a number of deleted records (e.g. as a result of the user's attempt to destroy evidence) without even knowing.
Traditional SQLite analysis tools do not show such data. Moreover, many forensic tools are not capable to do it either. However, the deleted records may contain information that is crucial for an investigation.
Why does SQLite keep deleted records? Due to performance considerations, the SQLite database engine does not immediately erase records deleted from the database (unless the specific instruction is given to purge the database). Instead, these records are kept temporarily in so-called “freelists”. As a result, some forensic tools such as Belkasoft Evidence Center can access freelist data, retrieving and analyzing evidence contained in deleted SQLite records. Freelist support is fully automatic in Belkasoft Evidence Center.
Suspects routinely delete their conversation histories by clearing Kik Messenger logs. Because SQLite does not wipe or erase records immediately, the deleted records end up in freelists. The deleted records may be kept in freelists for a very long time, until the database reclaims their space to store a new record. Thus, analyzing freelists gives investigators another chance to recover essential evidence.
SQLite Write-Ahead Log
SQLite was originally designed as a multi-threaded capable database. This means that it can, by its very design, handle multiple read and write operations occurring simultaneously without performance hit.
This also means that in order to deliver this multi-threaded performance, SQLite manages a temporary log file where all the concurrent write operations land. This file is called “write-ahead log”, and is usually (but not necessarily) named main.db-journal. If you have Skype, you can check this file out on your own computer. If you do so, you will discover that there is a significant difference in the sizes of the database and of the journal file. This implies that skipping write-ahead log analysis will cause losing potential evidence. Now, let us try to recover messages from Kik’s write-ahead log.
With Belkasoft Evidence Center, Kik write-ahead log is automatically accessible. Simply search for Kik artefacts, and the product will automatically identify, locate and process all available sources of information including Kik’s main SQLite database as well as its write-ahead journal.
Step 4: Carving Deleted Kik Messenger Databases
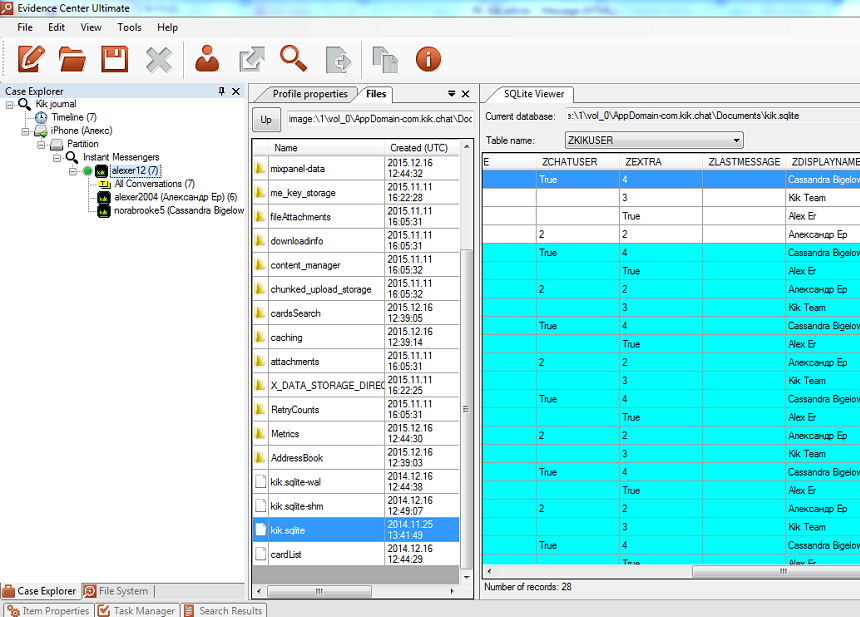
Sometimes, the suspect will attempt to destroy evidence by deleting the database file completely. While there is nothing you can do about it in iOS (the system does not let you recover anything that has been deleted), carving Android chip-off dumps may return an amazingly high amount of deleted evidence.
Belkasoft Evidence Center is equipped with a powerful carving tool. If you use it, you are guaranteed to recover some deleted and hidden data.
Once a deleted database is discovered, you can examine it using built-in SQLite viewer. Note that more often than not, deleted (and recovered) database files are partially corrupted, overwritten or incomplete, but this is not a problem for Evidence Center. Using BelkaCarving, you will be able to recover and view even badly damaged data.
Conclusion
To summarize, Kik is a popular messenger, which makes it relevant for digital investigations. It stores data in the format of SQLite databases, allowing in-depth analysis with ability to recover deleted and damaged data.
That is, in short, everything you need to know about Kik Messenger analysis to be able to discover evidence with digital forensic tools like Belkasoft Evidence Center.
You can learn more by reading our article on SQLite Analysis.
Try it yourself
Request a free trial version of Belkasoft Evidence Center at https://belkasoft.com/trial to test all the powerful Instant Messenger and other Internet artifacts analysis capabilities provided by the product.


