Introduction
Viber is a cross-platform VoIP and instant messaging application distributed across multiple mobile and PC platforms, including Android, iOS, Microsoft Windows, macOS, and Linux. There are over 1.1 billion Viber users worldwide and more than 820 million monthly active users.
Viber provides users with instant messaging functionality, and allows users to exchange media such as images and video records.
An important factor that separates Viber from other popular services requiring only the Internet connection for communication, is their Viber Out subscription plan. It allows calls to all mobiles and landlines in 50 countries around the world. Viber is also considered to be a secure messenger app, since it provides end-to-end encryption based on Open Whisper Signal security architecture.
In this article, we will focus mainly on the Viber app installed on Android devices. We will cover the following topics:
- Viber security features and limitations
- Location of Viber artifacts on Android-based devices
- Older and newer formats of a Viber database and differences between them
- The most important evidence to analyze during a digital forensic or an incident response investigation
We will also examine the techniques and tools which can be used to analyze Viber artifacts. Along with it, we will describe how artifacts can be extracted and displayed in Belkasoft X, a DFIR tool by Belkasoft.
Viber security features and limitations
One of the most notable features in Viber is end-to-end encryption.
Viber does not store any chat information on its servers once it is delivered to a recipient. If there is a problem delivering a message, it will remain encrypted until the receiver gets it, and will disappear from the server once it has been delivered.
However, messages sent to and from chatbots and the Chat Extensions feature are not protected by end-to-end encryption. Messages from bots are identified with a bot icon.
Public chats on Viber are not encrypted at all, however, Viber offers secret chats. Thanks to this feature users can communicate in an encrypted channel and their communication history will not be synchronized with the cloud service or with Viber Desktop. In secret chats there is a feature of the self-destructing messages as well as screenshot notifications. It is also a wide practice in chat apps including Viber to allow users to delete a chat for everyone.
A really unique Viber feature is the ability to hide any chat by setting a PIN code for it in the Viber settings. Once the chat is hidden you need to enter the PIN code in the messenger search field to unhide it.
Where Viber leaves digital traces on Android-based devices
The target artifacts which are mostly wanted by digital investigators in chat apps are:
- Content data, or the actual content of a communication, which can be text, audio, video, or any other format of data
- User profile data that commonly includes the chat app user name, surname, birthdate, gender, picture, address, phone number and email
- User authentication data—a password, session key, etc.
- Contact database, or the list of contacts associated to the chat app user
- Attachments and files exchanged, or any kind of data that were exchanged via a file transfer functionality
- Location data, or geographical position of the device
Most of the data from the Viber app can be obtained through a file system acquisition, it is also possible to manually download a specific folder containing Viber data by means of ADB backup extraction method.
Viber data is stored in the directory /data/data/com.viber.voip/
One of the folders inside this directory (‘f/.Fabric/preferences/’) contains the 'reg_viber_phone_num' and 'reg_viber_phone_num_canonized' files, which contain the unique identifier of the chat app user—the phone number the entry is linked to.
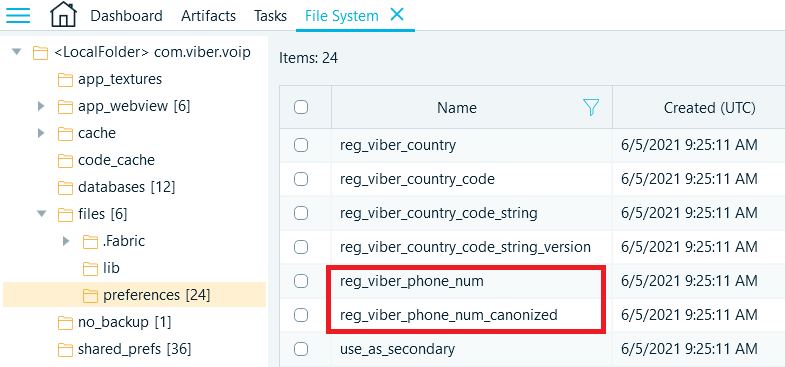
Figure 1: 'reg_viber_phone_num' and 'reg_viber_phone_num_canonized' files
The number occupies last bytes of files. There is a 7-byte header in front of it. The number in the canonical form includes the country code and the actual phone number without spaces, hyphens, brackets, and other symbols. The non-canonical number is commonly stored by a Viber user in a free form.
The files in '/files/preferences' also contain the name the user displays in the app (Display_name) and the SIM card's ICCID (Activated_sim_serial).
The files in the '/sdcard/viber/media' path are the profile photos (/User Photos/) of people in the user's contact list who use Viber, regardless of whether they have been added as friends in the app. Under the path images (/Viber Images/) and videos (/Viber Videos/) sent through the app are stored as well.
The database containing a meaningful part of communications is located in the 'viber_messages' file, which is located in a subdirectory named 'databases' or 'db' (the subdirectory's name depends on the Viber version).
Information about calls and contacts is stored in a separate database—the 'viber_data' file.
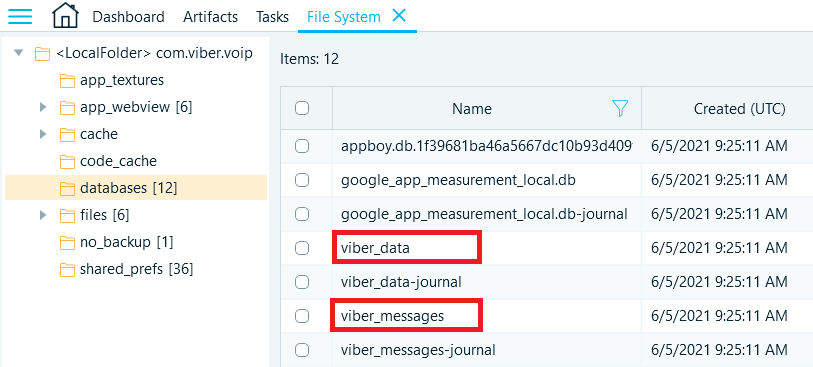
Figure 2: 'viber_data' and 'viber_messages' directories
'viber_messages' database structure
As it has already been mentioned, 'viber_messages' stores the most meaningful part of the data related to the Viber app on Android.
This database stores contacts, all the sent or received messages and geographical location information.
There are two possible versions of 'viber_messages' database—the old one and the new one. The structure of the older Viber versions differed a bit from the structure of the new one.
First, we will describe the older version of the database structure.
There is a table 'participants', where active contacts are kept. This table includes:
- 'thread_id' column, which contains an identifier of a chat between an account owner and this contact
- 'number' column, where a phone number of a contact (used as the unique identifier) is kept. This column can also contain predefined string values—'viber' (system contact) and 'owner' (account owner contact)
- 'display_name' for the contact display name
The next table 'messages' will help an investigator to get the required data about the communications of the account owner with their contacts. The main columns here are:
- 'address', the identifier of the interlocutor
- 'body', the text of the message
- 'date', the date and time in milliseconds of the Unix epoch
- 'type', the direction of the message (1—for outgoing)
- 'unread', if the message was read by the recipient (1—for unread messages)
Using the 'thread_id' from the 'participants' table and 'address' field from the 'messages' table, you can find the interlocutor in the table 'participants' and retrieve their ID and display name from this table.
However, not only text messages can be of interest for an investigator. There are non-text messages, which can be either the data about the calls through the service or the geolocation data.
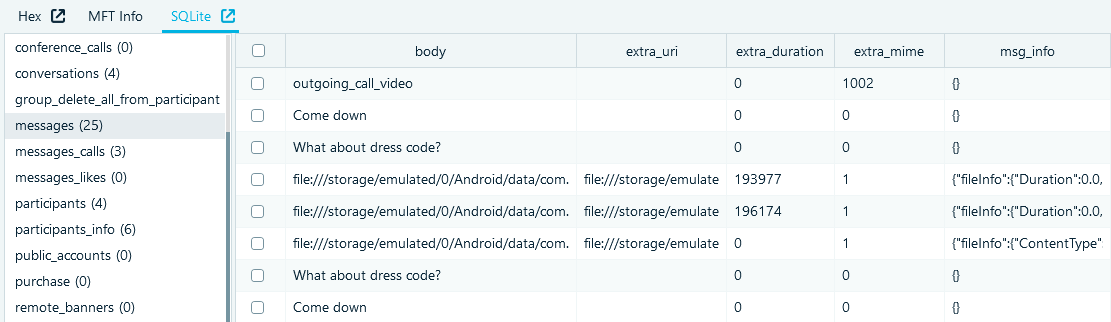
Figure 3: 'messages' table
For non-text messages information is stored in additional fields:
- Text in the 'msg_info' field stores system messages
- Fields 'location_lat' and 'location_lng' or data in JSON format in the field 'msg_info' store geolocation data
- Fields 'extra_mime' and 'extra_duration' are used for calls
- A link to a file in the 'extra_uri' field and additional data in JSON format in the 'msg_info' field is used for file transfer
The key difference between the older version of the database structure and the new one is that the database in the older format does not contain tables 'stickers' and 'conversations'.
Active contacts are stored in the new 'participants_info' table. The account owner's contact is stored there as well and is marked with the value 0 in the 'participant_type' column.
The main fields of the 'participants_info' table are:
- 'contact_name', 'display_name' and 'viber_name', each column can contain a display name
- 'number', which stores a telephone number
- 'contact_id', a link to the 'phonebookcontact' table, which contains additional data
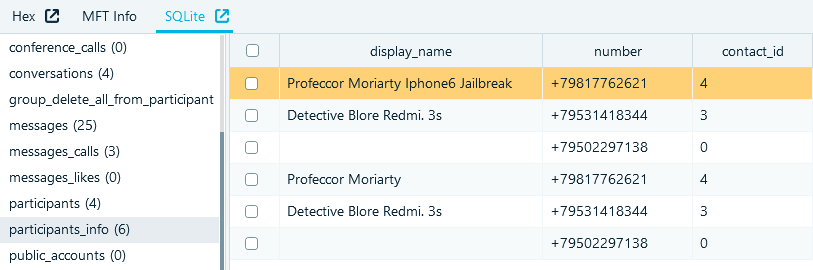
Figure 4: 'participants_info' table
The 'messages' table in general has the same structure as the corresponding table in the old format. However, there are some differences:
- The 'type' field is replaced by the field 'send_type' (1 stands for outgoing messages, and messages with any other value is interpreted as incoming), and the 'date' field is replaced by the 'msg_date' field
- The 'conversation_id' field has a link to the 'conversations' table, which contains information about individual chats
The new 'conversations' table has the following fields:
- 'recipient_number' is a telephone number or predefined chat identifier
- 'participant_id_1', 'participant_id_2', <...>, 'participant_id_8' are identifiers of the participants chat in the 'participants_info' table
Information about calls now can be stored in the 'messages_calls' table. The main fields of the table are:
- 'canonized_number' is a phone number of an interlocutor
- 'date' is a call start time
- 'duration' is a call duration
- 'type' is the direction of a call (zero first bit means outgoing calls)
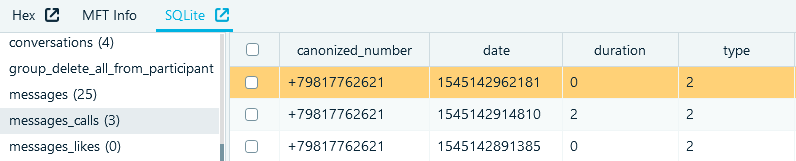
Figure 5: 'messages_calls' table
'viber_data' database structure
There is a table 'phonebookdata', where additional phone numbers are stored. The most useful columns are:
- 'contact_id' column, which contains the unique identifier of the corresponding contact from the abovementioned 'phonebookcontact' table
- 'data1', 'data2', 'data3' and 'data5' columns containing the phone numbers
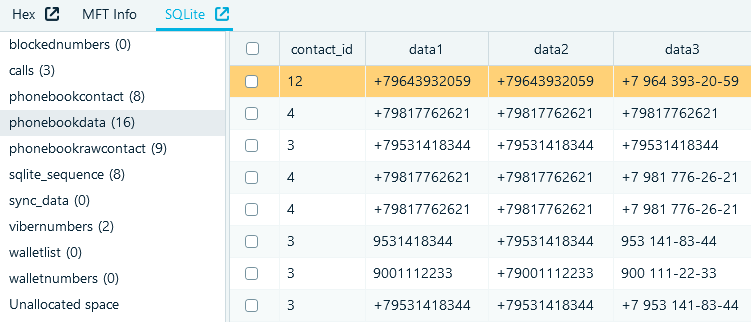
Figure 6: 'phonebookdata' table
The contact list is kept in the table 'phonebookcontact'. Every contact inside has a unique identifier '_id' and 'display_name' for the contact display name.
The next table of interest is the 'calls' table. The main fields inside are:
- 'number', the identifier of an interlocutor
- 'date', the start time of a call
- 'duration', the duration of a call in seconds
- 'type', the direction of a call (the first bit is zero for outgoing calls)
- 'viber_call_type', the call type (4—for video calls, any other value stands for audiocalls)
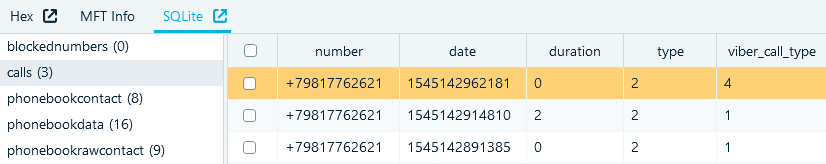
Figure 7: 'calls' table
Carving as a method to search for deleted or destroyed data
We suggest using carving to recover deleted Viber data. Carving is an indispensable technique while searching for deleted data and looking for destroyed evidence.
Carving of Viber data in the physical image of an Android device is carried out using three-byte signatures of the following type. For the old format '00 0X 2Y' is used, where X can be 1, 2, and 9, and Y is 3 for 11-digit phone numbers, 5 for 12-digit phone numbers, and 7 for 13-digit phone numbers. For the new format '00 2Y 05' is used, where Y takes values according to the same rule as in the old format.
Each found signature is an entry from the 'messages' table of the messages database. Record fields are stored sequentially and can be read one by one. The length of a field is determined by the value of its first byte. You can extract the ID of an interlocutor, direction and text of the message, but it is quite possible to extract the date as well.
Analyzing Viber data in Belkasoft X
In this section we will demonstrate how an investigator can analyze Viber data in Belkasoft X.
Belkasoft X supports both older and newer Viber database formats. All the data mentioned below is extracted and presented by Belkasoft X. On the screenshot below you may see how the evidence (in this case there are text and non-text messages) appears within Belkasoft X.
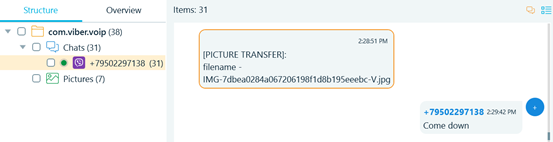
Figure 8: Viber messages in Bubble view
In Belkasoft X non-text messages are marked by one of special markers:
- [PICTURE TRANSFER]
- [CALL]
- [VIDEO CALL]
- [LOCATION]
- [SYSTEM INFO]
Apart from bubble chat view messages are presented in a grid view. This view allows to fit more data columns, and the messages can be sorted and filtered by various columns.
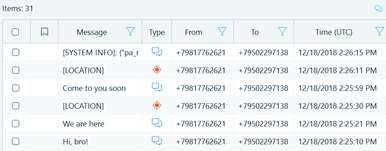
Figure 9: Viber messages in Grid view
On the right pane in Belkasoft X user interface it is possible to review properties of the selected message. Both participants’ phone numbers and display names are shown. One could also see the Delivery status of the message.
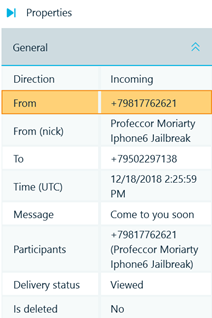
Figure 10: Viber message general properties
Origin properties of the selected message are shown in the right bottom column. Among them one could see the profile name and path, and define if the data is available in the file system or was extracted by carving.
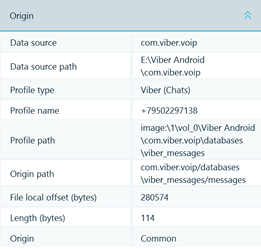
Figure 11: Viber message origin properties
If a message has a linked geolocation information (e.g. location sent), geolocation data could be found under the Origin properties. One could also opt to see all Viber geolocation information on a map.
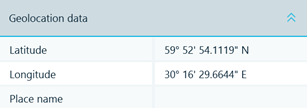
Figure 12: Viber geolocation data
Every Viber database file could be reviewed in the SQLite Viewer built in Belkasoft X. Journal and freelist records would be marked correspondingly.
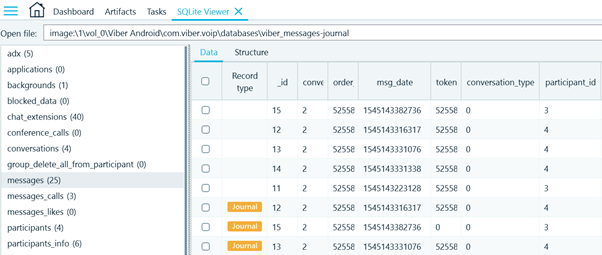
Figure 13: Viber data in SQLite Viewer
Conclusion
Viber is a truly secure messenger with such security features like end-to-end encryption of 1-to-1 and group chats. It also has such features like secret chats, self-destructing messages and the ability to hide any chat by setting a PIN code for it.
The most meaningful part of the data related to the Viber app on Android is stored in the database 'viber_messages', in which you can find contacts, all the sent or received messages and geographical location information. This database can be stored in two possible version—the old one and the new one, depending on the Viber app version.
Belkasoft X allows an extraction of important artifacts from the databases, which were described in the article, as well as helps an examiner to deal with the situations when there are deleted or self-destructing messages in the case.
See also:
- Whitepaper: WhatsApp Forensics on Smartphones
- Whitepaper: Six Steps to Successful Mobile Validation
- Article: How to analyze different types of devices and find connections between them
- Article: How to acquire data from an android device using APK downgrade method
- Article: Forensic Analysis of SQLite Databases: Free Lists, Write Ahead Log, Unallocated Space and Carving
- Webinar: Android acquisition methods with Belkasoft X
To try Belkasoft X, download the trial version of the product.
