Belkasoft CTF July 2022: Write-up
The fifth BelkaCTF was conducted on July 29 and 30, 2022. The CTF started at 11:00 AM UTC on the 29th and lasted for 24 hours. The CTF page was https://belkasoft.com/ctf_july_2022/ and the tasks were prepared for you by Belkasoft and ExtremeRoot teams.
This is an official write-up on how the tasks were supposed to be solved. There are naturally more ways to solve these tasks, and we encourage you to read contestants' own write-ups.
Note that every task could be solved without the Belkasoft X product, so even if one missed our trial or had any issues with it, it should not have stopped them from giving correct answers.
Did you like this CTF? Share your feedback on your social networks using the tag #BelkaCTF.
The CTF plot developed around a girl who disappeared after leaving for a party. She did not return for two days, and there were serious fears for her life. You had to figure out if the girl was alive, and if so, why she didn't get in touch for so long. This is her, by the way:

Let's begin taking flags!
1. User (Baby)
Question
Who is the laptop user? Format: Windows' user SID
Solution with Belkasoft X
- Create a new case and add the CTF .E01 file as a data source
- Analyze the image, selecting all artifacts to be extracted
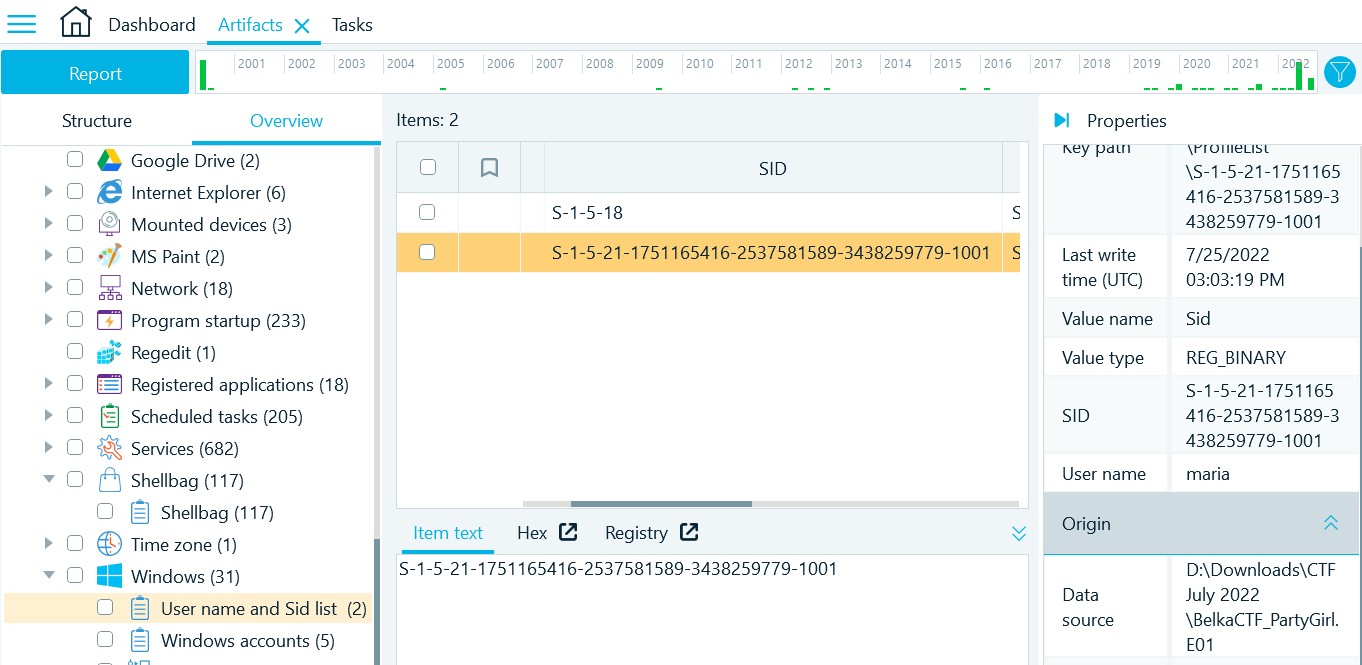
- Navigate to Artifacts → Overview → System files → Windows → User name and Sid list
Solution without Belkasoft X
- Open the CTF .E01 file in Autopsy, an open-source digital forensics tool
- Navigate to the OS Accounts node
- The only non-system user is 'maria', the SID is listed in the list of accounts
Flag
S-1-5-21-1751165416-2537581589-3438259779-1001 (the task was solved 140 times)
2. Missing stuff (Baby)
Question
What phone model did the girl use? Flag format: Commercial model name (not a model ID)
Solution with Belkasoft X
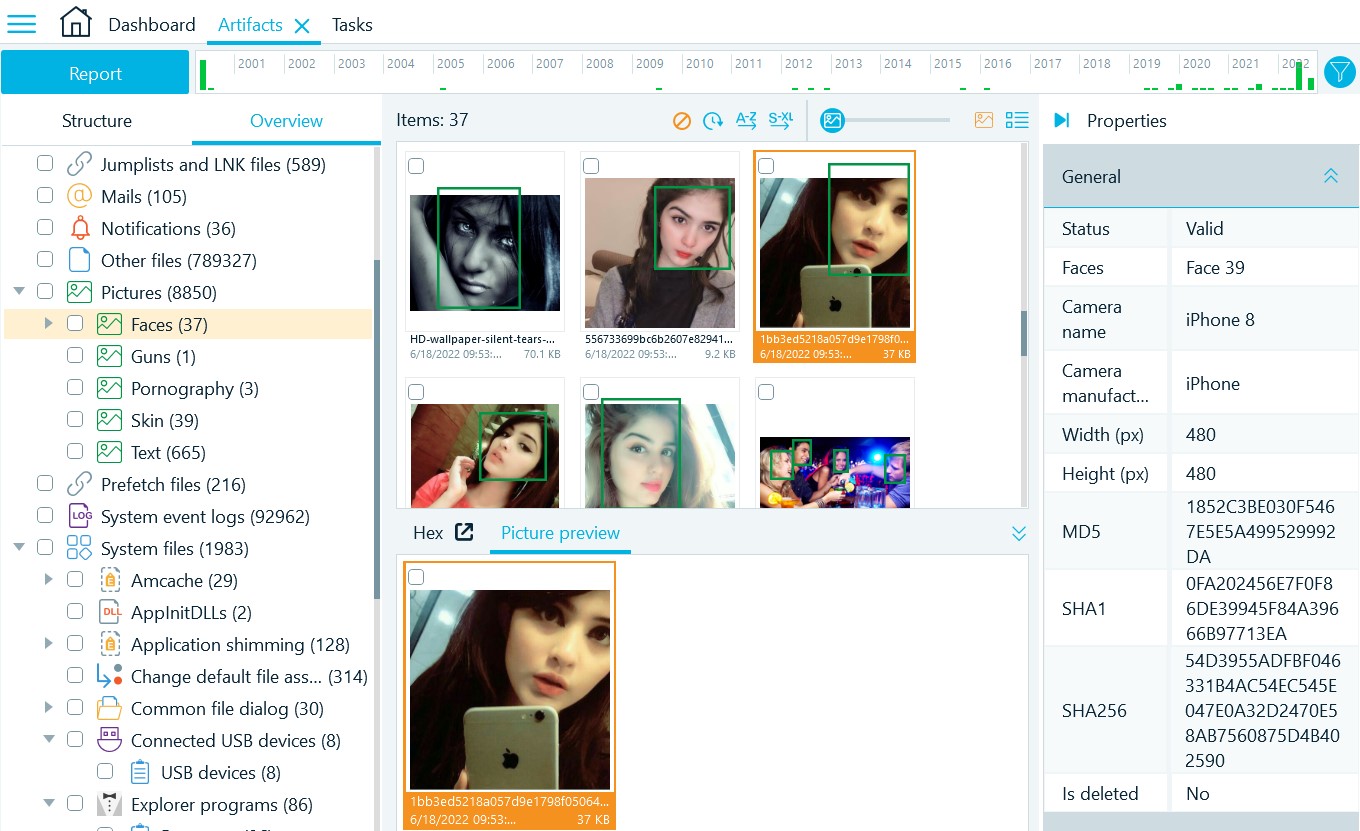
- Navigate to Artifacts → Overview → Pictures → Faces
-
Under this node you will find a number of selfie photos with a girl. By inspecting the photos' properties, you will find that they are stored under Maria's user folder ('Users\maria\OneDrive_\Pictures\Meh'). Photos properties include the phone model:
Solution without Belkasoft X
- Review pictures found inside the image in Autopsy, you will find a number of selfie photos with a girl
- Navigate to 'Users\maria\OneDrive_\Pictures\Meh'
- Select any selfie where an iPhone is visible. The 'Text' tab on the bottom will list the photo properties including the phone model
Flag
iPhone 8 (the engine would have also accepted iPhone8, iphone 8, IPHONE 8 etc.; the task was solved 119 times)
3. Going further (Warmup)
Question
What is the version number of the girl's email software? Flag format: xx.xx.xx.xx (numbers delimited by dots)
Solution with Belkasoft X
- Navigate to the Dashboard → Application Types. You will see Thunderbird listed there, a well-known email software
- To figure out the Thunderbird version:
- Navigate to the File System window
- Browse for Program files → Mozilla Thunderbird folder
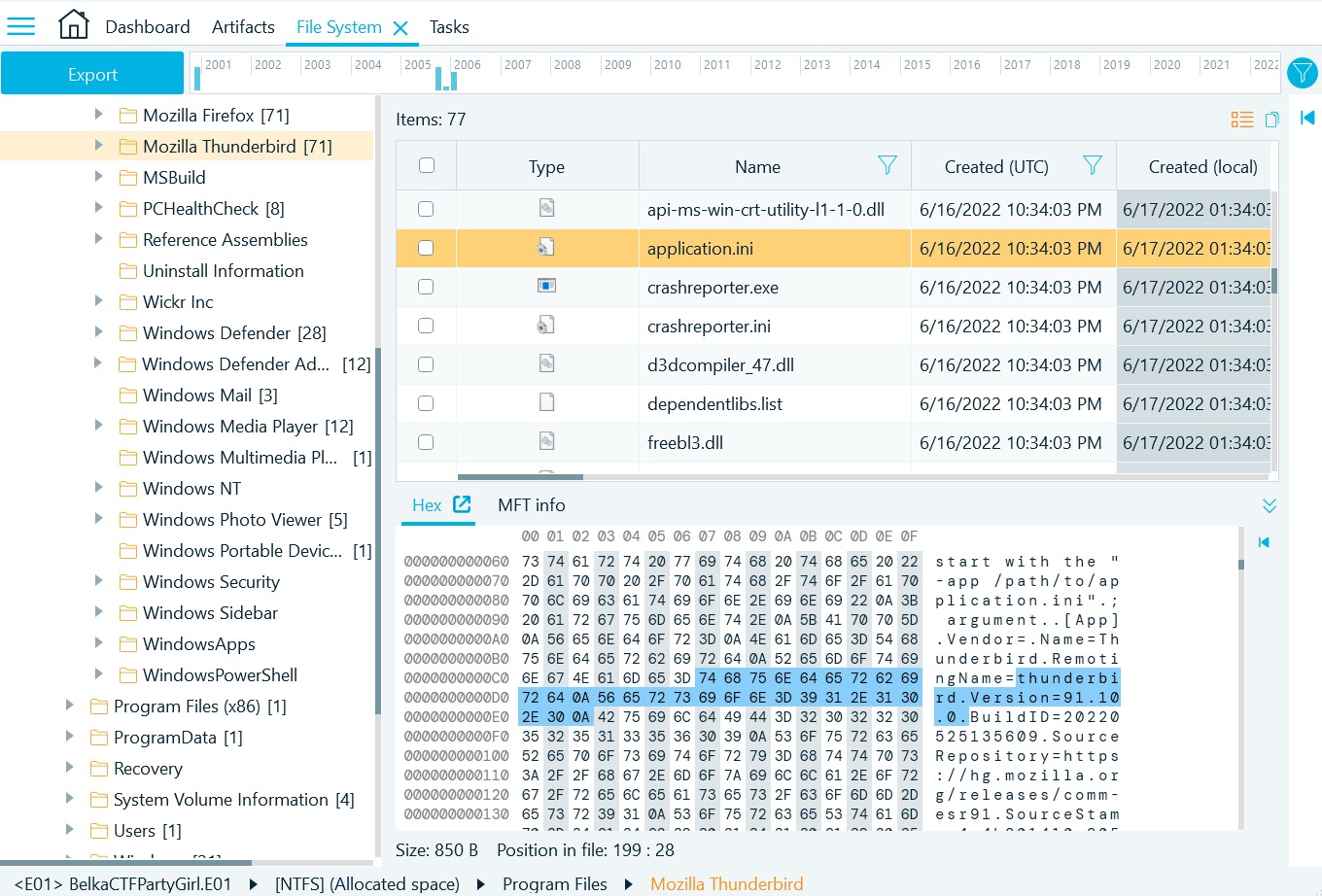
- On the File list, select the 'application.ini' file
- On the bottom, select the Hex tab. The product version is easily readable:
Solution without Belkasoft X
- In Autopsy, navigate to Data Artifacts → Installed Programs
- Find Thunderbird on the right pane. The software name includes its version
The flag format was deliberately misleading (contained one extra group of digits). Most players, however, figured out this little trick.
Flag
91.10.0 (this task was solved 110 times)
4. Boyfriend? (Baby)
Question
Who has recently invited the girl to meet up? Flag format: email address
Solution with Belkasoft X
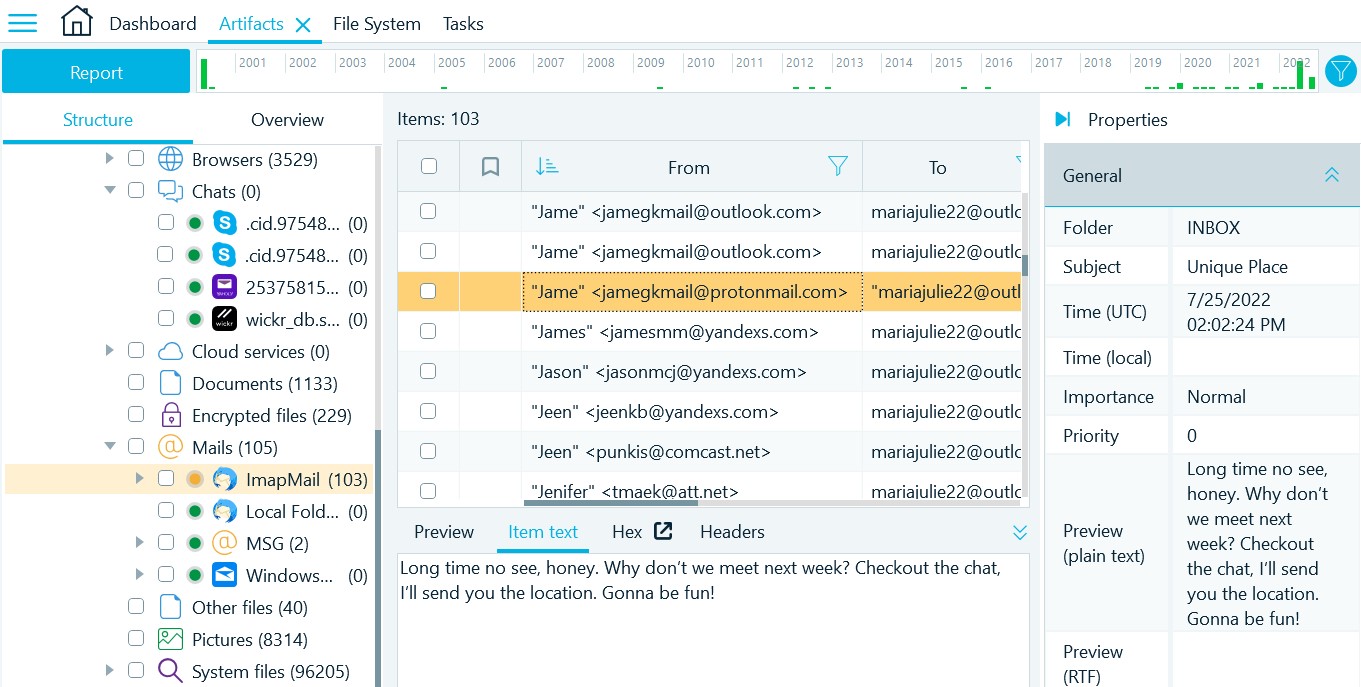
- Navigate to Artifacts → Structure → Mails → ImapMail
- One of the senders suggested Maria to meet and called her 'honey'. A hint in the task name is your extra support to decide this is a correct flag:
Solution without Belkasoft X
- Navigate to Data Artifacts → Email Messages → Default
- One of the senders suggested Maria to meet and called her 'honey'. A hint in the task name is your extra support to decide this is a correct flag
Flag
jamegkmail@protonmail.com (this task was solved 108 times)
5. Final! (Hard)
Question
What is the chat password?
Following the plot, the protagonist was excited to complete the investigation, because he suspected that the chat, referenced in the email found in Task 4, will contain the location where Maria could be found (or, at least, where she was last seen). This is why the task is called 'Final!'. There were no other clues hidden in the task name.
Solution with Belkasoft X
- Navigate to the Tasks window of the product. You will find that there is a task pending your input. This is a Wickr Me analysis task, which prompts for a password. Belkasoft X always shows such prompts for pieces of encrypted data, so this is your first candidate to be the chat app mentioned in the question:
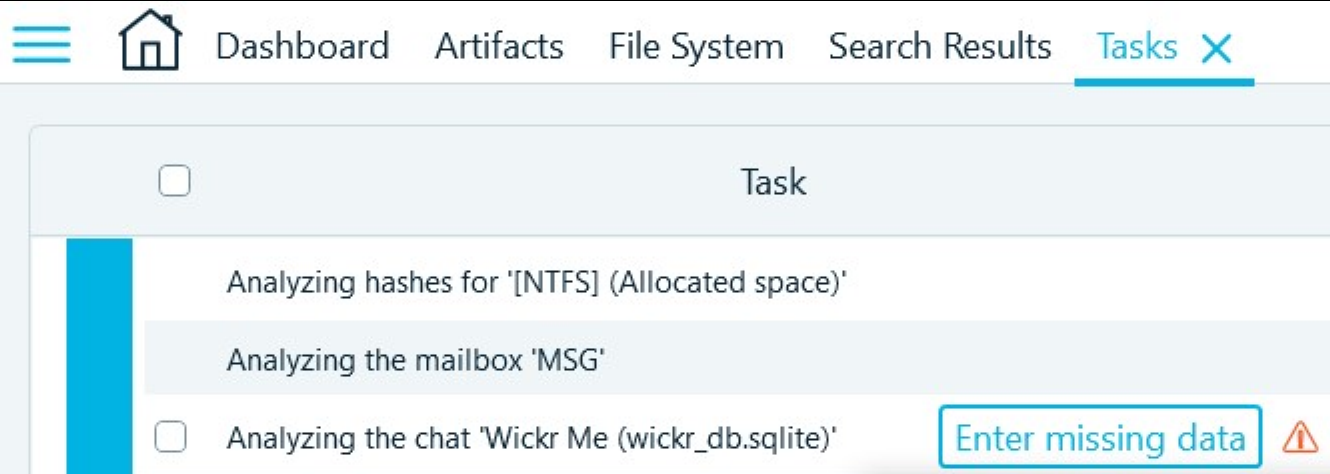
- Return to the Artifacts window and search by 'Wickr*' (you can do this using Ctrl-F; do not forget to tick 'Treat as regex' check box)
- Navigate to the Search Results window. There are some 250+ results
- With Belkasoft X, you can try to filter out results, for example by looking for 'pwd' or 'password':
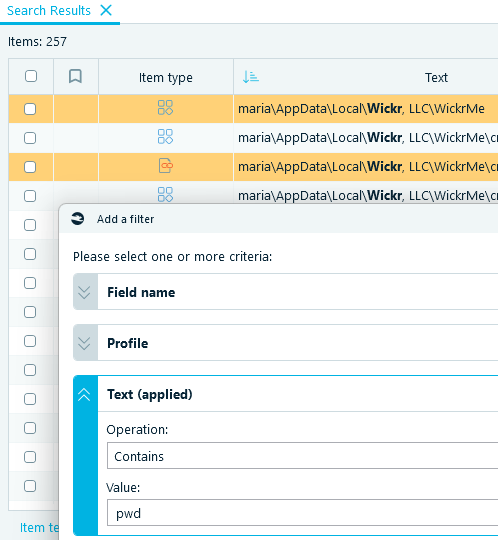
- The first string will give you a file called 'WickrMePwd.lnk'. Inspect this file binary contents right in the Hex tab of the Search Results:
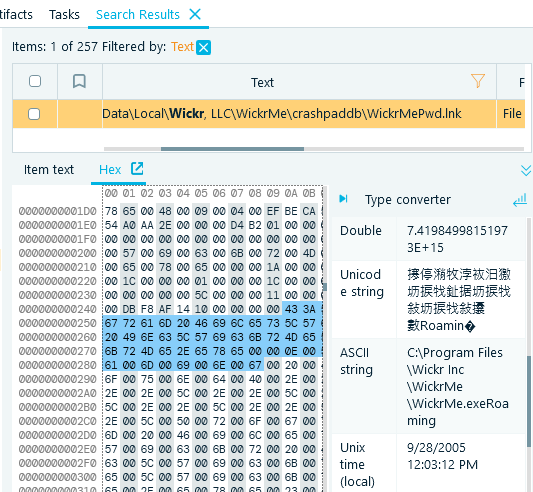
This value gives you a hint to look into the Roaming folder for the user, which as we know is 'maria'.
- In the File System, navigate to 'NTFS (Allocated space)' → Users → maria → AppData → Roaming → Wickr, LLC. This folder contains a single file named Wakemeup.txt (you actually could have seen it already under the Search Results). The file name would look suspicious even to an inexperienced CTF player. Let's look at its contents:
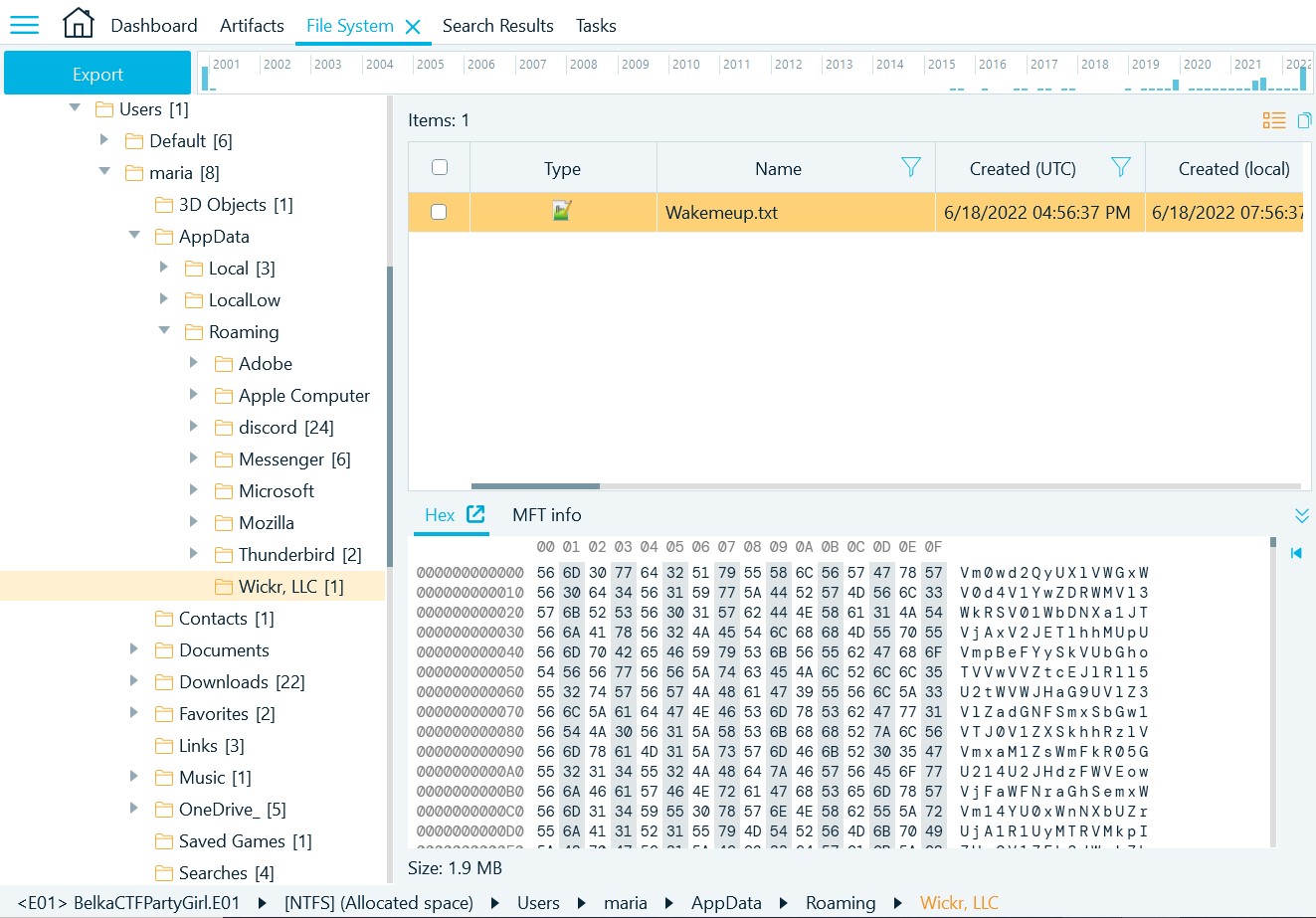
- The content of the file does not seem readable but it's quite
obvious that this is most possibly just a Base64-encoded text. Let's copy it:
- Click on the 'Open full screen' icon of Hex tab for the 'Wakemeup.txt' file
- The full-screen Hex Viewer will open
- Select the entire contents by pressing Ctrl-A
- Right click and select 'Copy as text' (not as hex!)
- Now let's open CyberChef and paste the data into the Input field
- Drag 'From Base64' to the 'Recipe' field. Applying this once may frustrate you since the string does not seem to change, however you can notice that the length of the string decreases. Having a bit of stubbornness (we mean, purposefulness), you can find the flag, when you reach the magic number '42' of the decoding repetitions:
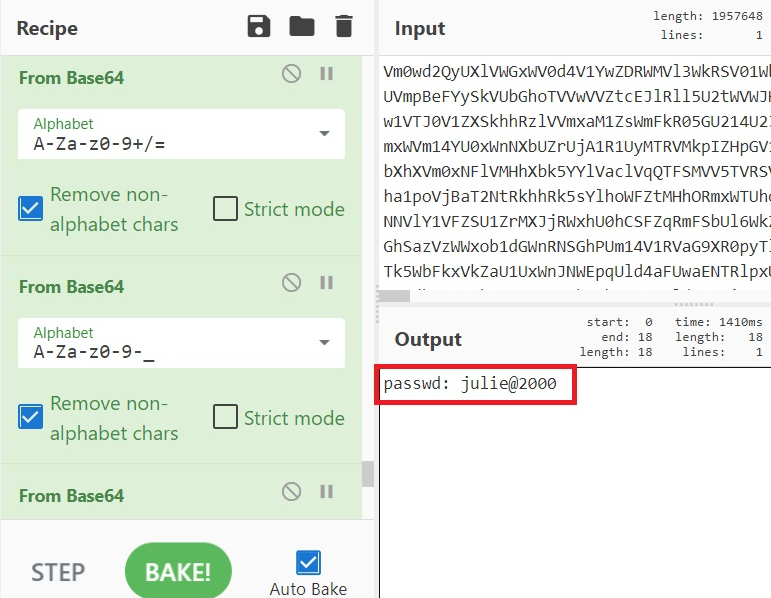
Solution without Belkasoft X
- Installed applications show chat apps used by Maria. Particularly, you can find WickrMe
- Search for 'pwd' or 'password' or look into the application AppData folders
- Roaming folder contains a file named 'wakemeup.txt', which seems to be encrypted or encoded
- Looks like its content is just a Base64-encoded string. Copy it and paste to CyberChef
- Drag 'From Base64' to the 'Recipe' field. Applying this once may frustrate you since the string does not seem to change; however, you can notice that the length of the string decreases. Having a bit of stubbornness (we mean, purposefulness), you can find the flag, when you reach the magic number '42' of the decoding repetitions
Flag
julie@2000 (this task was solved 44 times—not 42!)
6. Not final (Hard)
Question
What software was mentioned in the invitation?
OK, at this point the protagonist found that this is not as easy to solve his case, as to just read one single chat message. Looks like the story is a bit more complicated...
Solution with Belkasoft X
-
Use the password found in Task 5 as an input for the pending Wickr task:
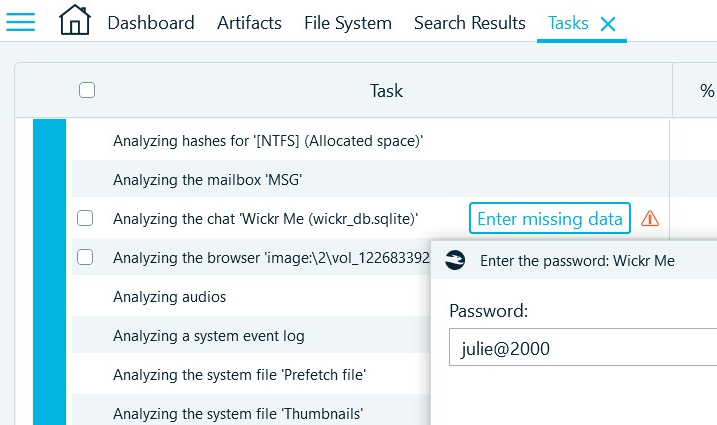
- Looks like this is the correct password! Belkasoft X successfully completes the analysis and shows you a brief conversation of just 20 items. HINT: If you canceled that task before, you can re-run it by selecting 'Analyze' context menu item right clicking on the WickrMe profile in Artifacts → Structure → NTFS (allocated space) → Chats
- An invitation.ics file was sent by user jammy6265:
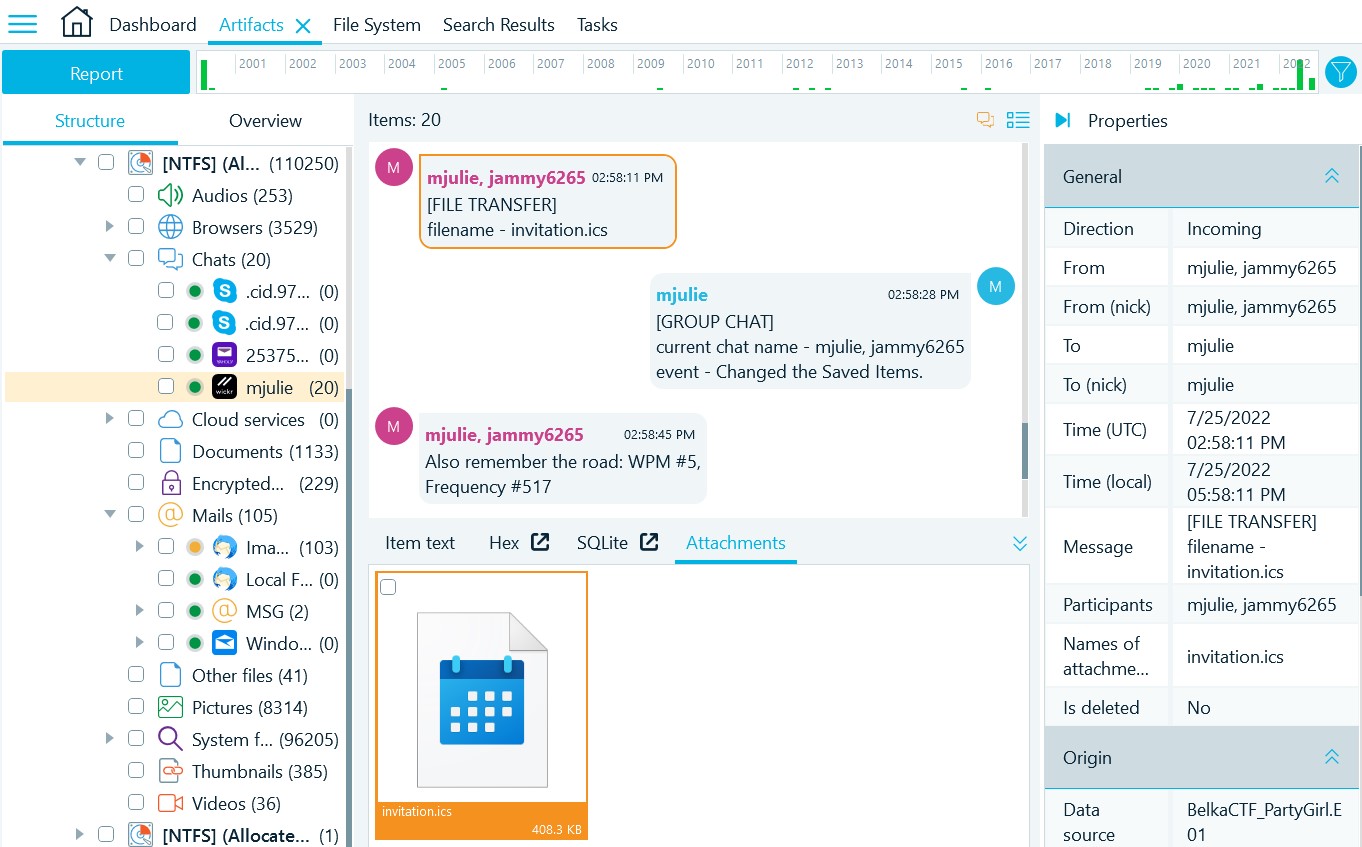
- However, opening it in an email app does not work. Save the file to a folder by navigating the the Attachments tab and right clicking on the file:
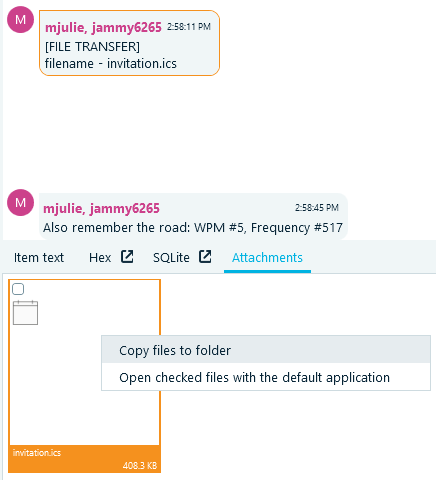
- Look into the file contents in the Hex Viewer of Belkasoft X or any viewer of your preference. You will find that its signature seems the file is not an ics file but a zip file
- Rename the file extension to '.zip' and extract its contents. Two files will be extracted:
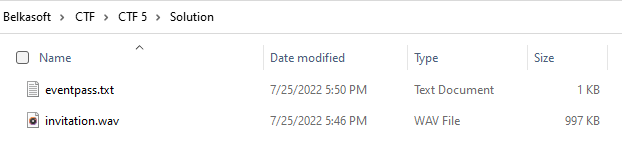
- The 'eventpass.txt' file contains just a string 'secretevent', which might be a password or something else. Let's remember it for the future
- Let's look at the other file. There does not seem to be any tricks with it, it can be played perfectly. It is not hard to recognize the Morse code. The task's picture, which shows the 'party girl' on a yacht gives you an additional hint for that guess
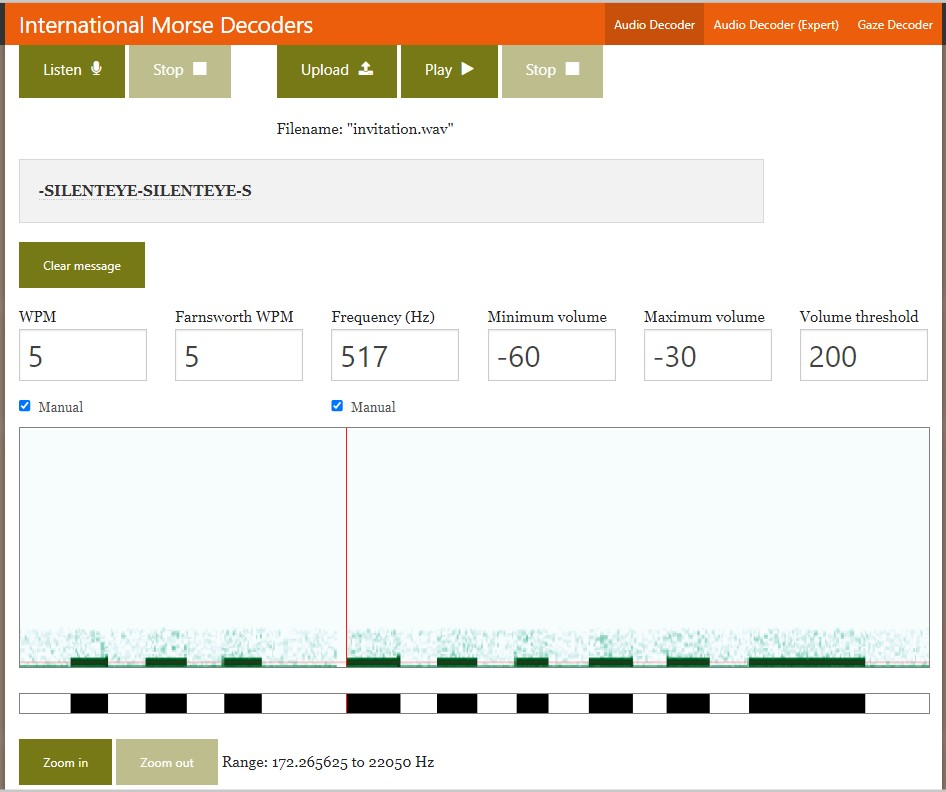
- Find a Morse audio decoder online (e.g. this one) on Google and upload the invitation.wav file
- Remember the cryptic message about the WPM and Frequency in the Wickr chat? You can use them to specify these values to the chosen decoder (though the one we used was able to decode the message out of the box):
Solution without Belkasoft X
- We found the WickrMe password, however, there are unfortunately no non-commercial tool capable to decrypt WickrMe chat database. That's a dead end
- Let's look closer to the Wickr folders. Particularly, AppData → Local → Wickr, LLC → WickrMe. Particularly, we may find the 'temp' subfolder with another interesting subfolder called 'attachments'.
- In this subfolder you may spot the 'invitation.ics'. Suspiciously enough, this file is recognized as a zip file, not an invitation file, what may attract your attention
- The rest of the solution is the same as the solution with Belkasoft X, pp. 7-10
Flag
silenteye (this task was solved 37 times)
7. BelkaRestaurant (Tricky)
Question
Where was Maria invited to? Flag format: location name (case insensitive)
Solution without Belkasoft X
Actually, only p.9 and 10 from the 'Solution with Belkasoft X' relate to the product but they are there just to illustrate the way a player may have been thinking.
Solution with Belkasoft X
- Google for silenteye. Even if you haven't heard of this name before, you quickly find this is a steganography software. Let's download and install it
- What should we feed it? The task picture can give you a slight hint: the girl is looking at the endless series of reflections created by two mirrors. The same reflection repeated multiple times... OK... well... might be not the best hint, but it was supposed to prompt you that you should use the same file as in the previous task
- Open SilentEye software. You will find it works with pretty limited types of files, which looks like a better hint than we did with the pic. Open the invitation.wav file:
- Click on 'Decode' and then 'Decode message'
- An image file is found, which is hidden in the audio file:
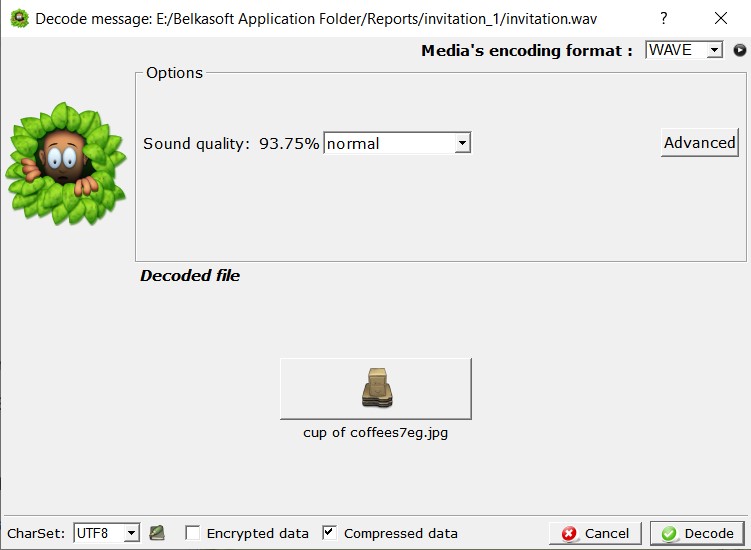
- Opening the file shows a cup of coffee set on a rooftop:

An experienced traveler immediately recognizes the city, by the way
- Digging into Exif info of the image shows nothing interesting. At this point many players run out of ideas, however, there are all details needed to find the answer
- The picture of the task makes even more sense at this point. Reflection inside reflection inside reflection... A perfect hint to keep searching for an image steganography tool
- Review the search history for Maria in Belkasoft X's Search Results window. The product shows you Automatic Searches, and one of such searches is 'Search engine results'. Out of 119 results you will see a few dozens of 'future boy' entries:
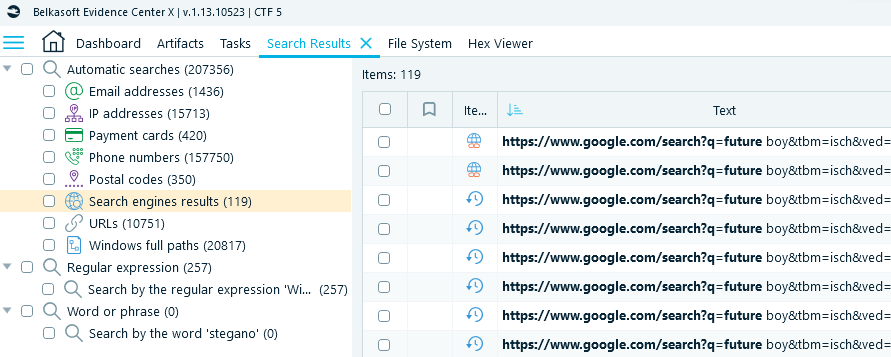
- Besides, inspecting Artifacts → Overview → Browsers → URLs will give you a couple of hits for 'futureboy.us'
- Browse this site, go to 'Steganography tools' → 'Decode an image'. Upload the coffee-cup image and try to decode. The file unfortunately does not decode with the blank password
- Now let's remember that we have the 'eventpass.txt' knowledge not yet used. Let's try entering the 'specialevent' string from there. Voilà! Your flag is here!
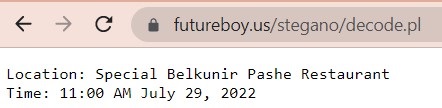
The task name gives you an additional hint that this is indeed a correct answer.
Flag
Special Belkunir Pashe Restaurant (this task was solved 22 times)
8. Open to call (Baby)
Question
What is the restaurant phone number I should call? Flag format: phone number +XXXXXXXXX (no spaces, dots, hyphens)
Solution with Belkasoft X
This task is not supposed to be solved with Belkasoft's product.
Solution without Belkasoft X
- Searching on Google Maps for 'Special Belkunir Pashe Restaurant' does not give any meaningful results
- Does the task name give any clues? The 'Open to call' seems to! Let's try OpenStreetMap instead and indeed, the search for the restaurant name gives your flag:
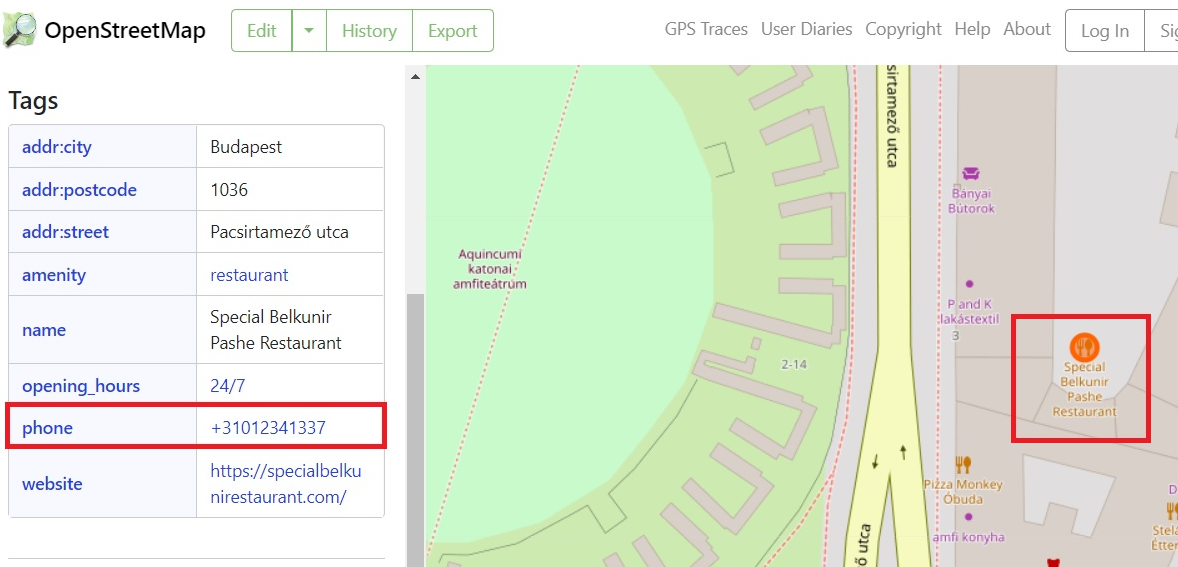
Flag
+31012341337 (this task was solved 22 times)
9. Backup (Warmup)
Question
What kind of second factor can I use to download the girl’s iCloud backup? Flag format: x, y, z, where x, y and z are one of the following options—
1. Maria's iPad, which is set as trusted. It is locked, but shows notifications
with text
2. Maria's iPhone
3. James' iPhone, which is set as trusted
4. James' iPad, which is logged as a family member for Maria
This task had a limitation of three attempts only. If a player gave three incorrect replies, this was a 'game over' and the only chance to score was to complete task 11, which became open close to the end of the CTF.
The task complexity was originally set to 'Warmup', however it looked like the task confused many players. Let us explain the easiest way to get the correct reply.
The question contained a link to 'one useful article'. The article was devoted exactly to the iCloud downloading, and at the bottom, all two-factor authentication options were mentioned. Let us first try to eliminate obviously wrong answers.
Option 4. James' iPad which is logged as a family member for Maria. Family settings allow to share Apple TV, Music, purchases and other things; however, iCloud two-factor authorization is not shared. Wrong
Option 2. Maria's iPhone. Obviously, this is the best option to complete the two-factor authorization. However, the iPhone is with Maria, as the story informs. In the CTF support chat, we gave a hint on that option: players must consider practically available options, not options useful theoretically. It was a hint to eliminate this option. Wrong
Now, if a player did not rush entering flags and if they still have three unspent attempts, the correct reply could have been just guessed. Your options left were '1', '3', and '1, 3', that's it! (to be exactly accurate, an empty reply was also an option, but we explicitly confirmed to the CTF chat that this is not a correct answer).
Let us, however, explain the other answers.
Option 1. Maria's iPad, which is set as trusted. It is locked, but shows notifications with text. There are many leads that this option is incorrect.
- First, to show two-factor code, the device must be unlocked. You will see the notification about the iCloud authentication even in the locked mode, but will not be able to see the code itself
- OK, there is the second way, to get an SMS. Obviously, Maria's SIM-card is inside her iPhone; but even if it was inside the iPad, these devices cannot receive SMSes. Some players researched the question enough in-depth to find out that SMS sharing can be set up enabling an iPad to receive SMSes received by an iPhone. However, the provided option says nothing about this important detail, we reinforced that to the chat by explicitly confirming that no significant details were omitted in provided options
So, this option is also Wrong.
Now we stay with option number 3: James' iPhone, which is set as trusted. That's the correct answer, a trusted device can receive the code. We gave an additional hint to the CTF chat, that James is collaborative (which means that there won't be difficulties to unlock his phone and see the notification text). Correct
Flag
3 (this task was solved 7 times)
Some players complained that they messed up the flag format in this task. However, given that the reply was just one digit, this was hardly the case.
10. Mystery unveiled (Baby)
Question
Can you figure out where the girl is? Flag format: Place name (case insensitive; not coordinates)
As per the story, based on the notification from James' iPhone, the protagonist was able to download the entire iPhone backup stored in the iCloud. That backup contained a file called consolidated.db. A link to this file was provided to players.
Solution with Belkasoft X
- The easiest way is to download the 'consolidated.db' into an empty folder and analyze that folder with Belkasoft X (must be v.1.14)
- Upon analysis completion, navigate to Artifacts → Structure → [Data source name] → Mobile application → Geolocation data
- There are just two artifacts found:
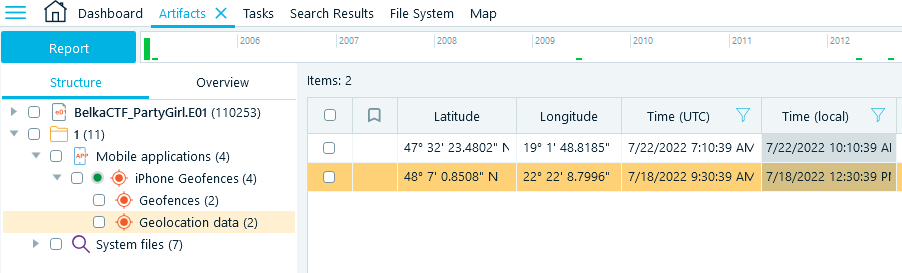
- Select the one, which has a later date (Jul 22). Right click on it and select the 'Show checked items on Map' menu item. Now, zoom in until you can read the place name, which is your flag:
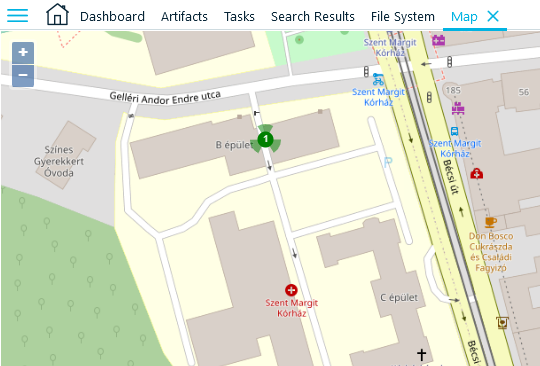
If you do not have v.1.14, there is another way to solve the task with Belkasoft X:
- Open the database in the SQLite Viewer of the tool and navigate to the GeoFences table:
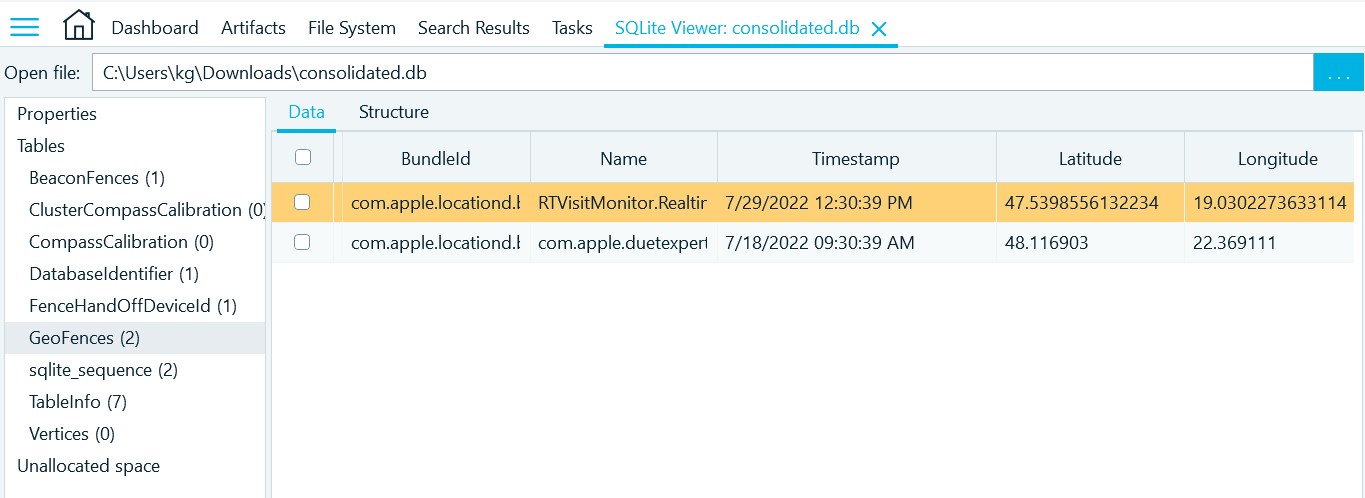
- Apply Apple Cocoa time to the 'Timestamp' column:
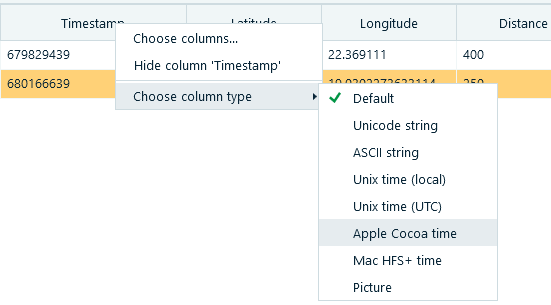
- This will help you to figure out dates to make sure these geolocations relate to the plot. Copy the item with the date of Jul 22, remove extra column values and paste just coordinates to the Google Maps. You will read the location name, which is your flag
Solution without Belkasoft X
- Open consolidated.db file in any SQLite browser, for example DB Browser for SQLite or a Chrome SQLite extension
- Open GeoFences table and copy timestamps to any tool, which can convert Apple Cocoa time to a human-readable time
- Make sure both timestamps relate to the plot dates and select the proper record:
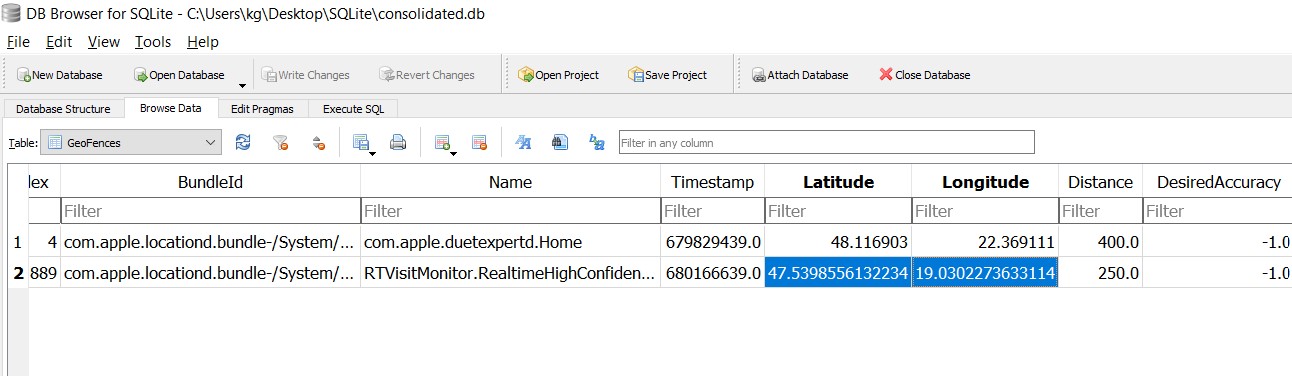
- Copy the latitude and longitude of the latest record and check on the Google Maps:
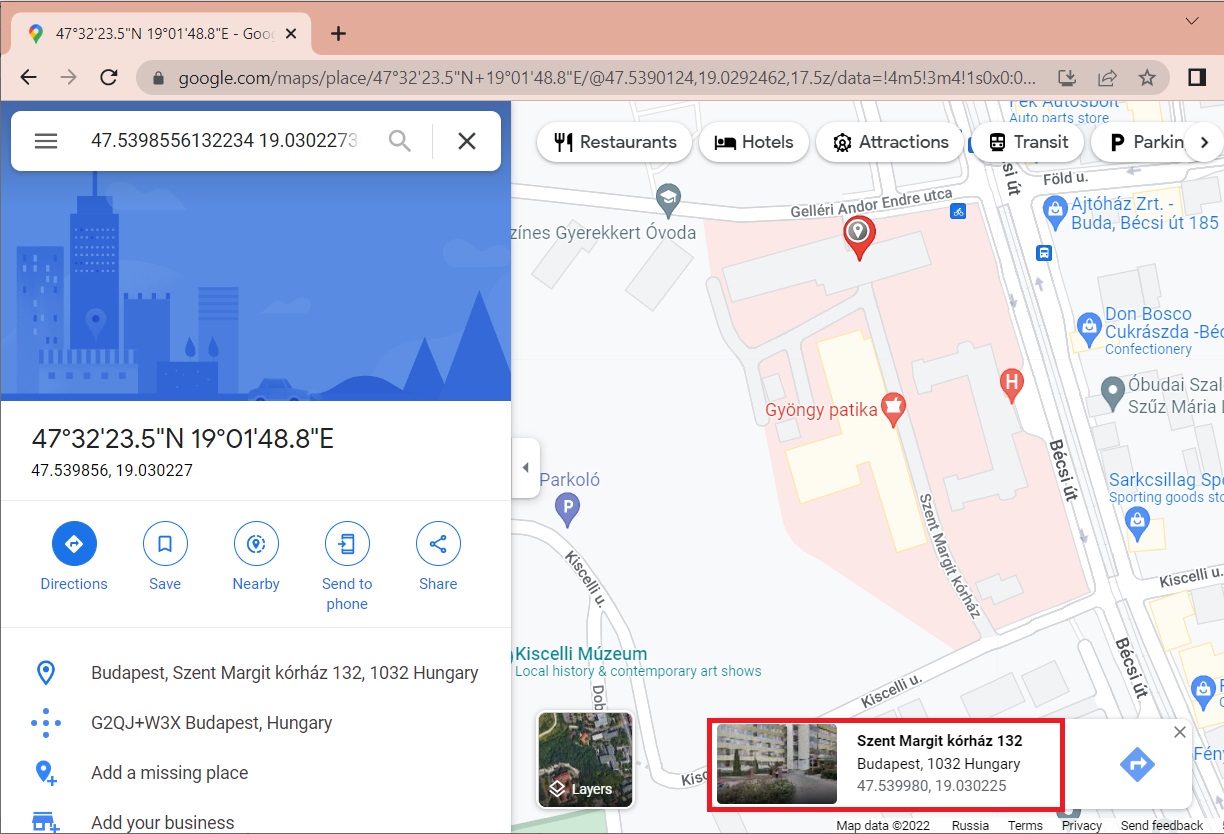
Flag
Saint Margaret Hospital or Szent Margit Kórház (both names accepted, casing does not matter; this task was solved 7 times)
11. Pride (Final)
This was a bonus task, which allowed players to earn 150 points more by publishing anything about the CTF. Any link was being accepted, automatically adding the score, however bogus links, non-working links and links, which were removed at the time of checking, led to the subtraction of the bonus points back. Players would want to consider this for the future CTFs!
If you were curious about what happened to the girl and why she did not reply to the parents' calls, the beginning of this bonus task contained a full explanation of details (though, of course, not very realistic, but theoretically possible). Are you excited with this end of story? Please let us know!
A couple of nice examples of correct flags were:
- A post by the winner, Weihan Goh. He shares one amazing fact in his small review—make sure to check it out!
- A post by Susie R
- A post by Ubaidullah Malik
We hope you enjoyed the CTF 'Party Girl—Missing'. If so, please share your feedback in your social accounts using #BelkaCTF tag. See you next time!
See also
- Belkasoft CTF page
- Learn more on the Belkasoft X product used for the CTF
- See Belkasoft's webinars on digital forensics and incident response
- Enjoy BelkaTalk series of short videos, devoted to one particular DFIR question each