Belkasoft CTF June 2021: Write-up
The third BelkaCTF was conducted on June 18th & 19th, 2021. The CTF started at 7:00 AM EDT on the 18th and lasted for 24 hours. The CTF page was https://belkasoft.com/ctf_june/ and the tasks were prepared for you by Belkasoft and SPbCTF teams.
This is an official write-up on how the tasks were supposed to be solved. There are naturally more ways to solve these tasks, and we encourage you to read contestants' own write-ups.
Note that every task could be solved without the Belkasoft X product, so even if one missed our trial or had any issues with it, it should not have stopped them from giving correct answers.
Did you like this CTF?
The plot of this CTF was a continuation of the BelkaCTF #2 ('Drugdealer case') but this time you had to fight against 'The Boss', the main guy behind a drugdealing syndicate, who was uncaught for last three years. This is him, by the way:

Let's begin taking flags!
1. Username (Baby)
Question
What is the username used on the imaged laptop?
Solution without Belkasoft X
- Launch the provided image into any virtual machine. You may need to mount the image as a local drive or to convert E01 provided to a DD because most of VMs do not support E01. See task #7 for more detail if you have difficulties with that
- The username of the machine will be presented upon login
Solution with Belkasoft X
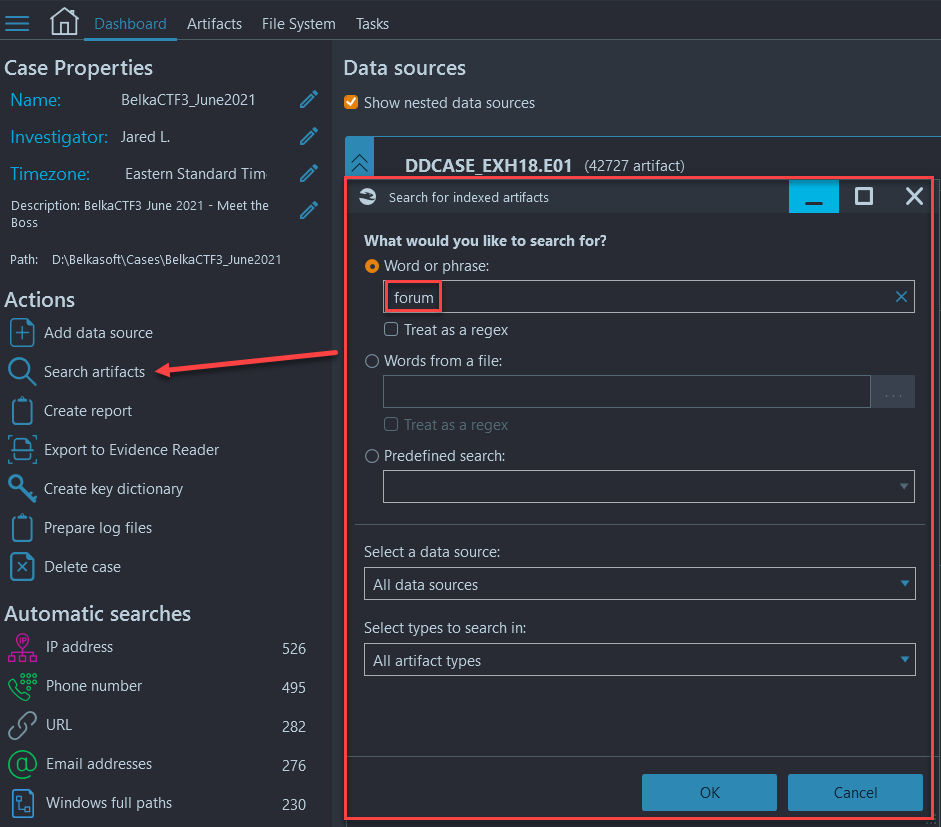
- Create a new case and add the .E01 file as an image data source
- Analyze the image, selecting all artifacts to be extracted
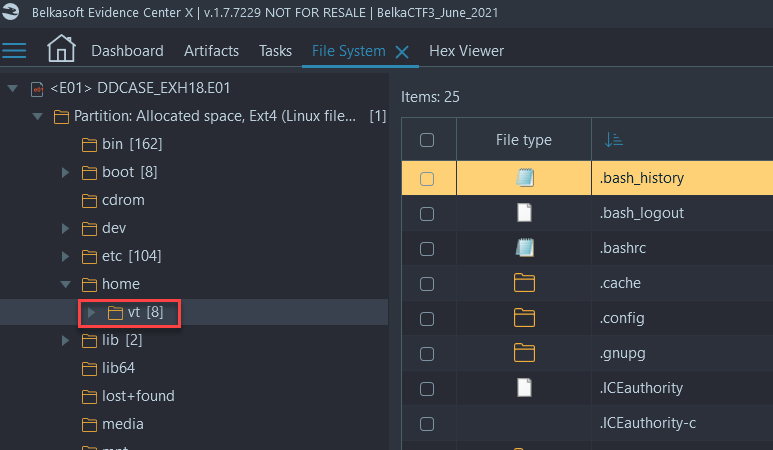
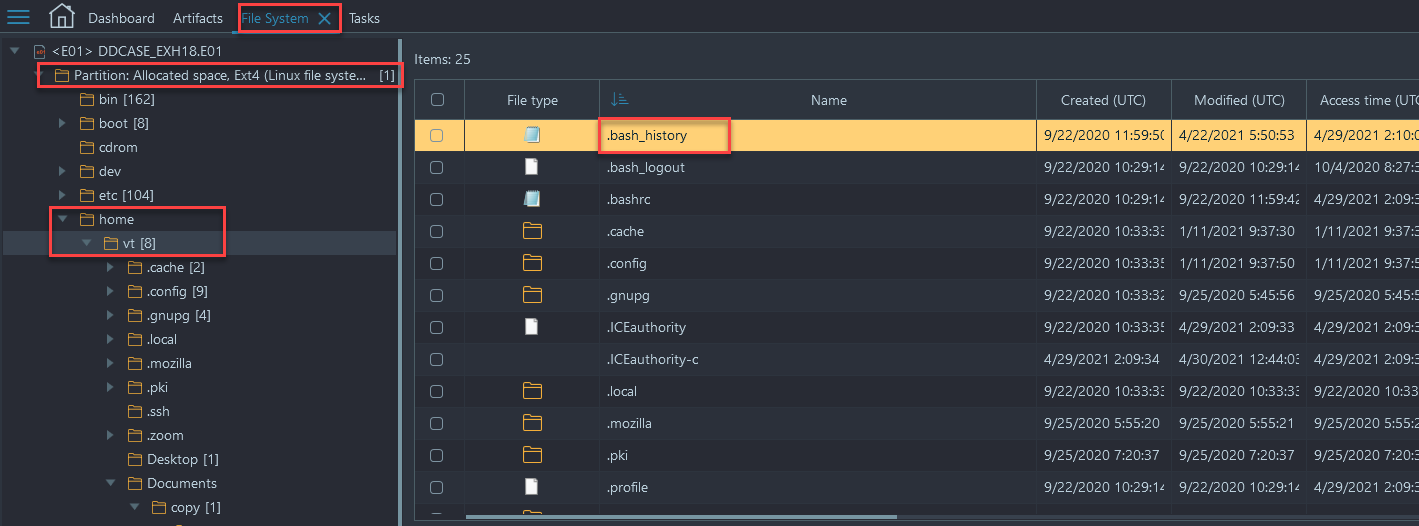
- Navigate to File System → Partition Allocated space, Ext4 → /home. There is a single folder of the only user in the home directory... OR
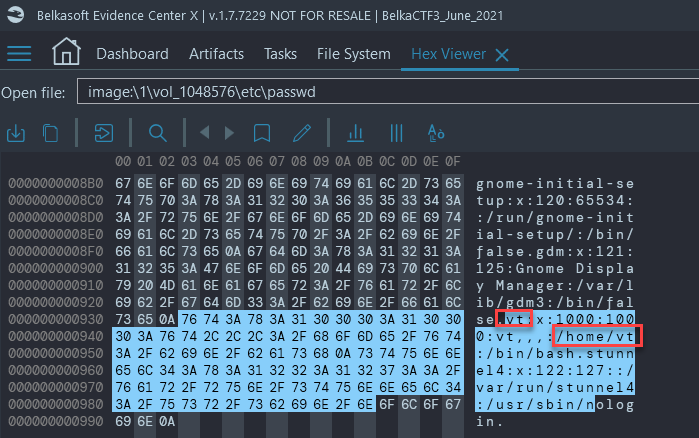
- Navigate to File System → Partition Allocated space, Ext4 → /etc/passwd → open passwd file in Hex Viewer and scroll to bottom to see the added user:
Flag
vt (this task was solved 114 times)
2. Forums (Warmup)
Question
What two thematical forums does the boss have accounts on? Format: answer, answer
Solution without Belkasoft X
- Extract with any tool, the 'Login Data' SQLite database that is located within
the following folder:
/home/vt/.config/BraveSoftware/Brave-Browser/Default - Once extracted, review the 'Login Data' file with a SQLite viewer of your choosing and examine the 'Logins' table for any mention of 'forum'
Solution with Belkasoft X
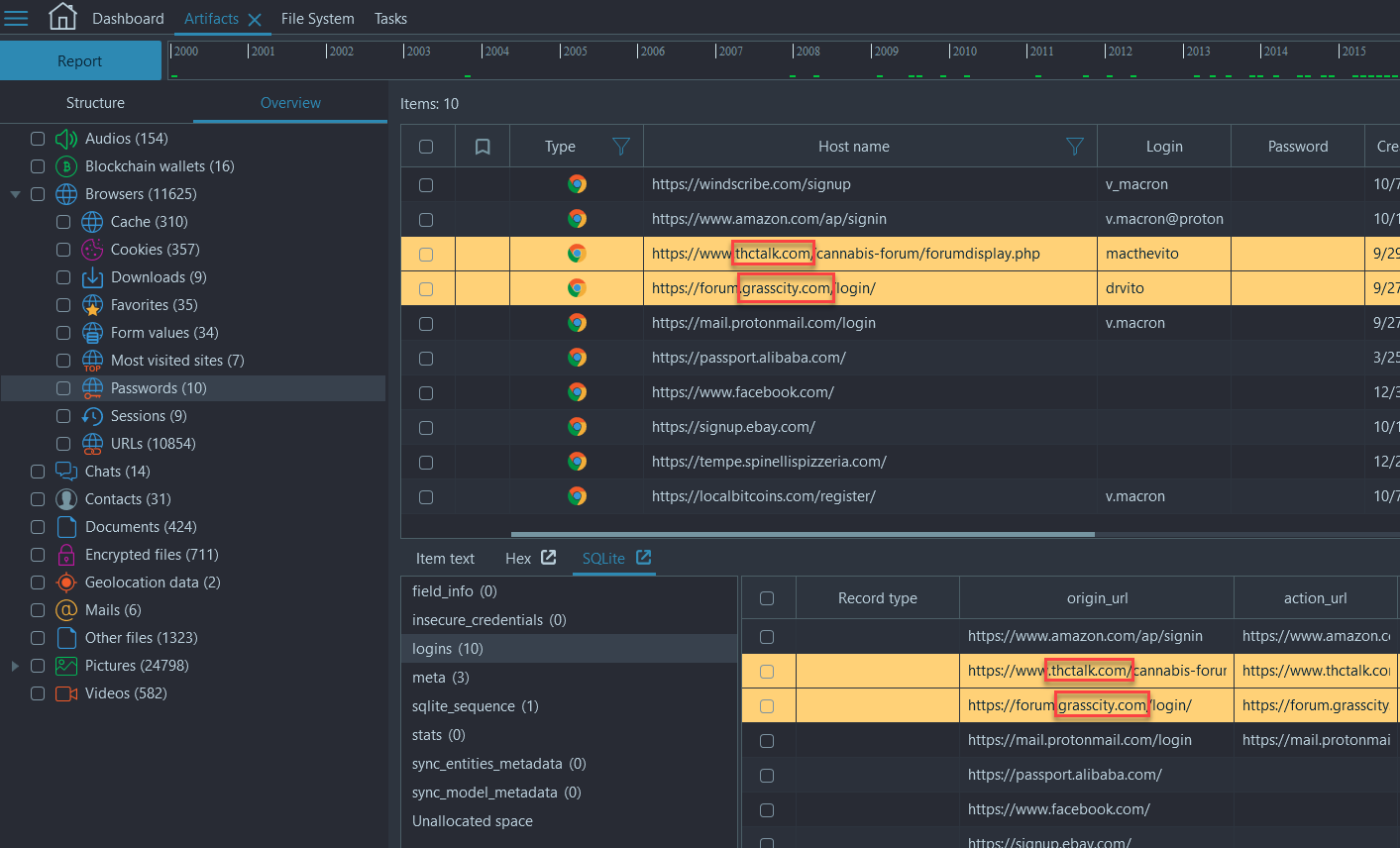
- Navigate to Artifacts → Overview → Browsers → Passwords. Use the column filter on 'Host name' and filter by 'forum'... OR
- Navigate to Dashboard → 'Search artifacts' and search for the term 'forum' across the entire image, then search through the search results for websites that mention forums:
Flag
thctalk.com, grasscity.com (this task was solved 94 times)
3. Delivery (Warmup)
Question
What is the address where the boss has ordered delivery October 19th 2020?
Solution without Belkasoft X
- Extract with any tool, the 'Web Data' SQLite database that is located within
the following folder:
/home/vt/.config/BraveSoftware/Brave-Browser/Default - Once extracted, review the 'Web Data' file with a SQLite viewer of your choosing
and examine the 'autofill' table for an address
Solution with Belkasoft X
- Navigate to Artifacts → Overview → Browsers → 'Form values' and you will see a 'Field name' column. Sort by 'Creation time' and look for '10/19/2020' or simply scroll down until you see the 'address' or 'addressSugg' Field name:
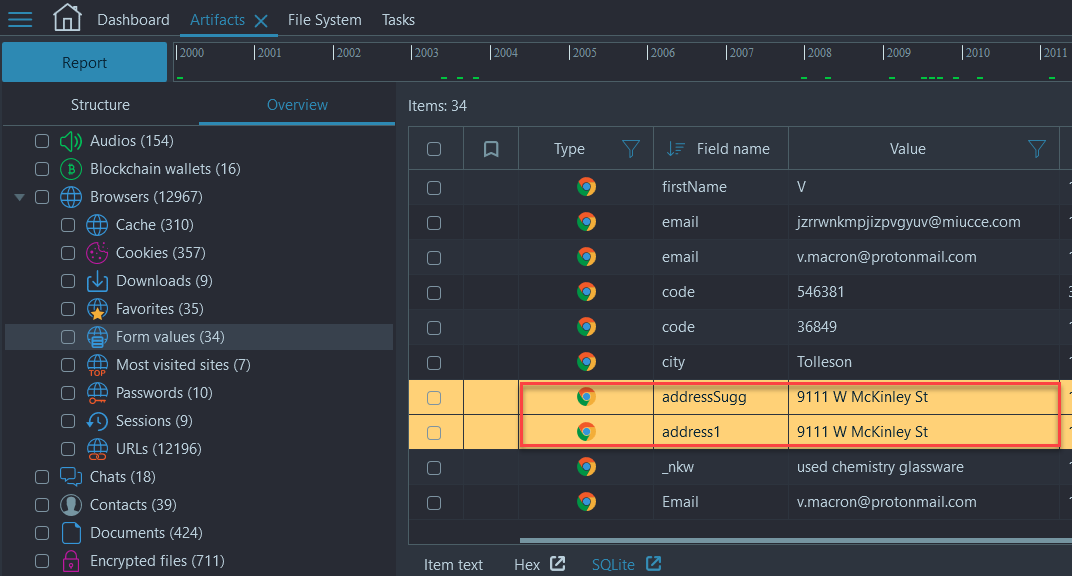
Flag
9111 W McKinley St (This task was solved 83 times)
4. Product (Hard)
Question
What equipment has the boss ordered? Provide the product name as specified by the seller
Solution without Belkasoft X
- Load the image into the tool of your choosing, locate the browser Cookie timestamps that match the timestamps assigned to address1 (10/19/2020) from the previous question, we see that the only cookies that match that time frame come from eBay
- Utilizing the 'strings' command in a linux VM against the entire image and exercising the 'grep' feature for 'ebay.com/' we find the following three URLs:
- https://www.ebay.com/itm/313460105738?hash=item48fbada20a:g:9o4AAOSwcMNgU6NA
- https://www.ebay.com/itm/283602462421?hash=item42080626d5:g:oNkAAOSw5nZdZXlN
- https://www.ebay.com/itm/273997170926?hash=item3fcb8108ee:g:OaAAAOSwee5dcUNS
- Open the above URLs with a browser of your choice to see what the products
are, one of the products is your flag.
Solution with Belkasoft X
- Navigate to Artifacts → Structure → Browsers → Chrome (Carved) → URLs
- Filter by 'Last Visit Time (UTC)' and look for '10/19/2020'
- You will see a lot of eBay activity and a few different products that are presented in the 'Page name' column (the three URLs above):
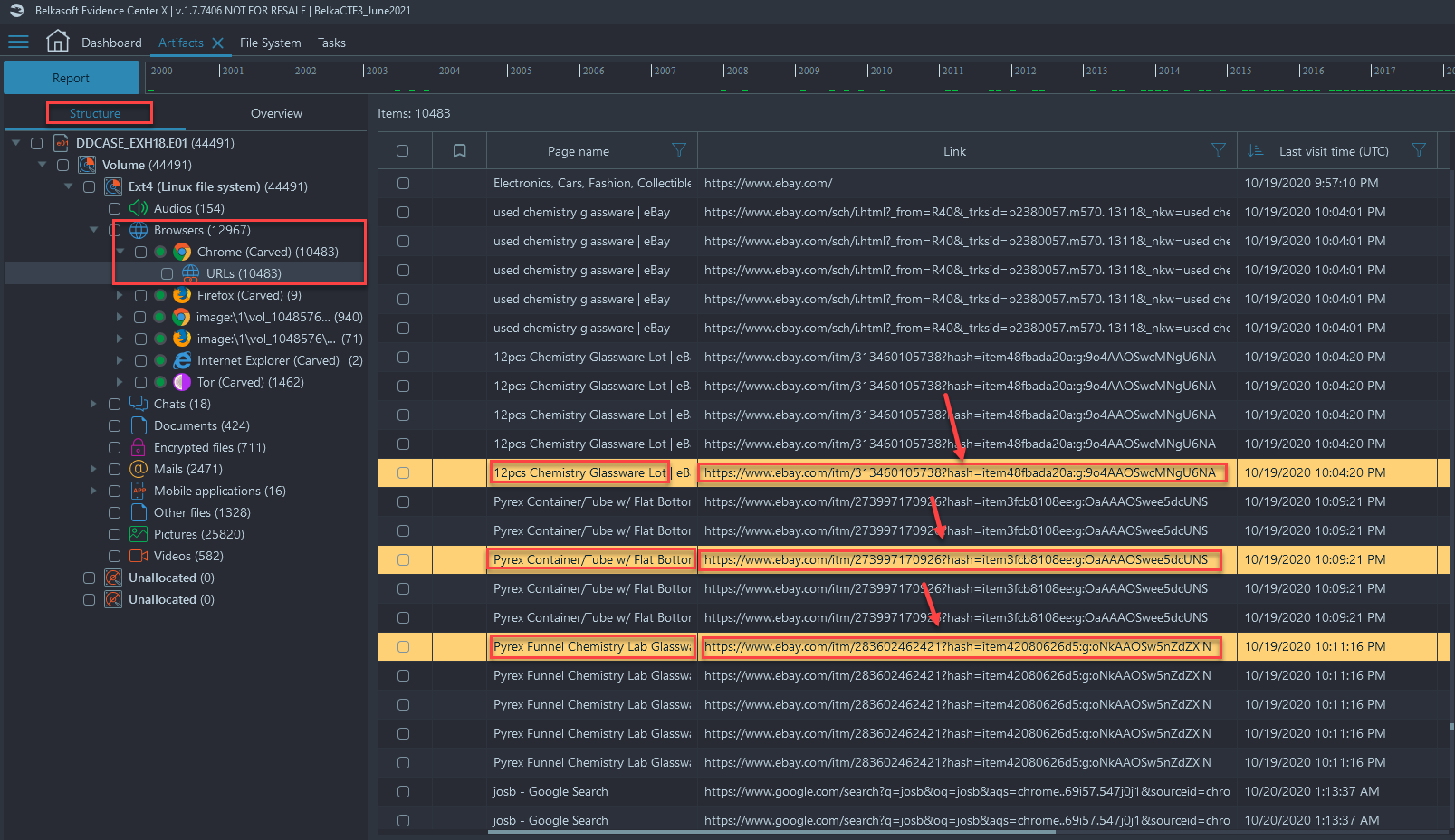
- Navigating to those addresses (three URLs mentioned above) through a browser of your choosing, you should see that only one of the items has been sold:
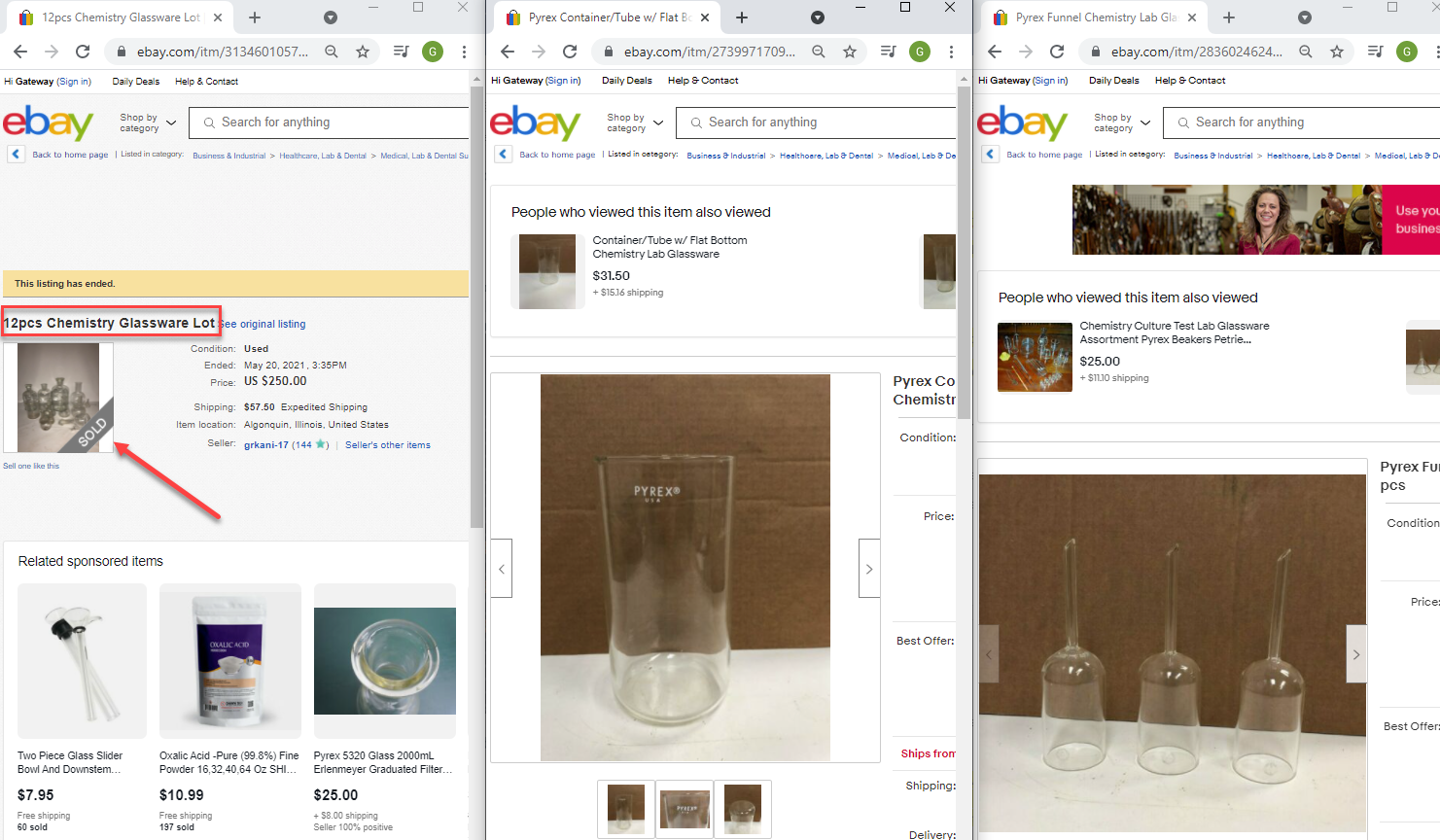
Flag
12pcs Chemistry Glassware Lot (this task was solved 33 times)
5. Thumb Drive (Tricky)
Question
It looks like the boss actively used a USB flash drive. Which one should we look for during a search? Format: 'maker, model, color' e.g. Maker: Lexar, Model: JumpDrive TwistTurn2, Color: purple+white
Solution without Belkasoft X
- In an image viewer of your choice, load the provided image, and navigate to '/home/vt' and view the '.bash_history' file with a text viewer such as notepad or notepad++
- Inside the .bash_history file, you will see reference to a /media/Kingston_3C62-88A1/ USB device multiple times, where he keeps his Bitcoin wallet files
- Above each log in the .bash_history file there is a Unix time stamp, convert these timestamps and look for a log from 4/2/2021, where the Kingston USB is 'ejected' and then reinserted
- Now to verify what we are seeing in .bash_history, we need to look into some system log files located at /var/log/kern.log.4.gz on 4/2/2021. Upon examining the log files we see the following output for new USB devices:
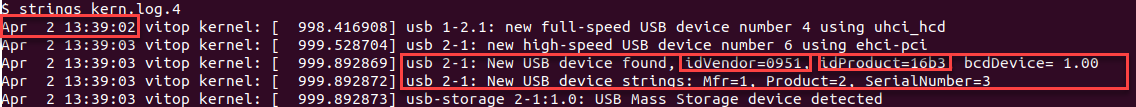
- usb 2-1: New USB device found, idVendor=0951, idProduct=16b3, bcdDevice=1.00
- usb 2-1: New USB device strings: Mfr=1, Product=2, SerialNumber=3
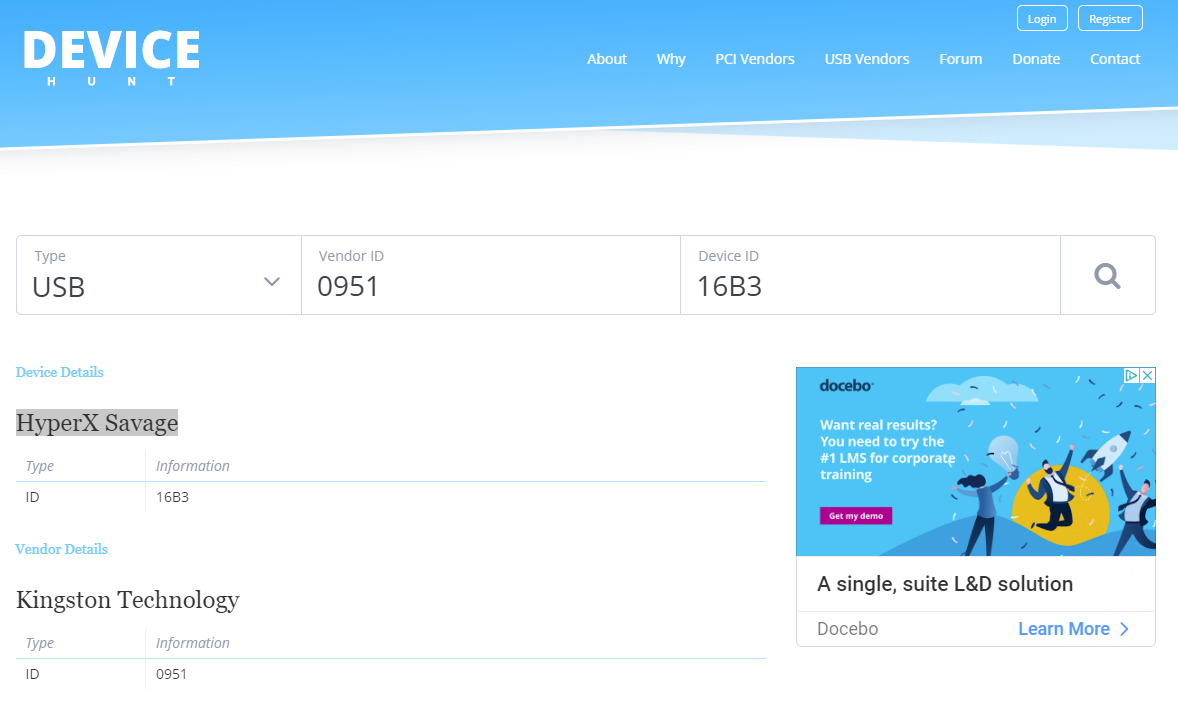
- Now a simple Google search of the Vendor information and Product ID will tell us what kind of USB this is—Kingston HyperX Savage
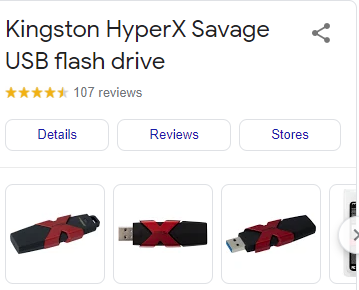
- Next, Google that USB to see what it looks like—red+black
Solution with Belkasoft X
- Navigate to File System → /home → /vt → .bash_history and open the hex viewer after selecting the .bash_history file:
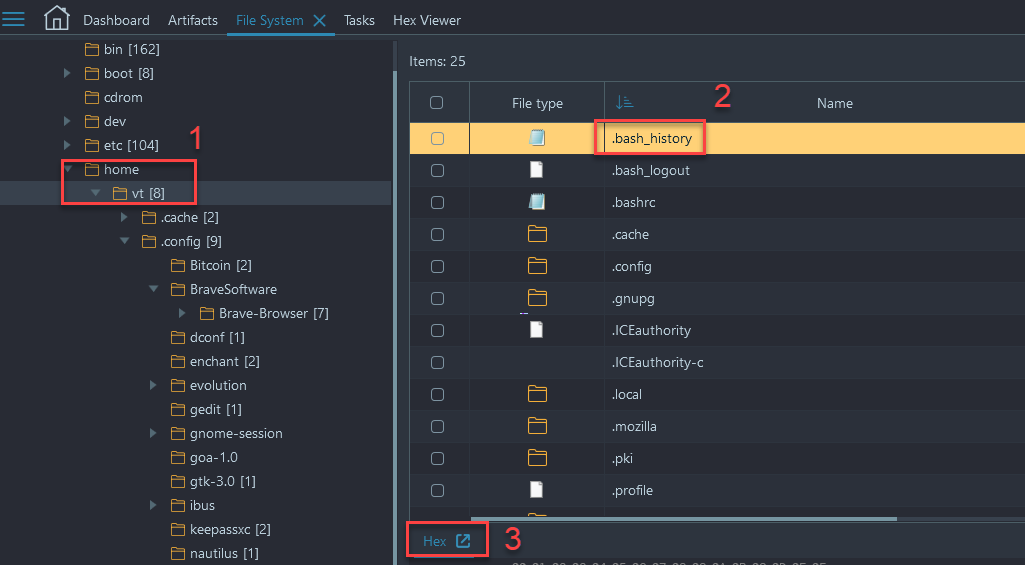
- Once in the built-in Hex Viewer do a text search for 'media' and you will get multiple hits for /media/Kingston_3C62-88A1/:
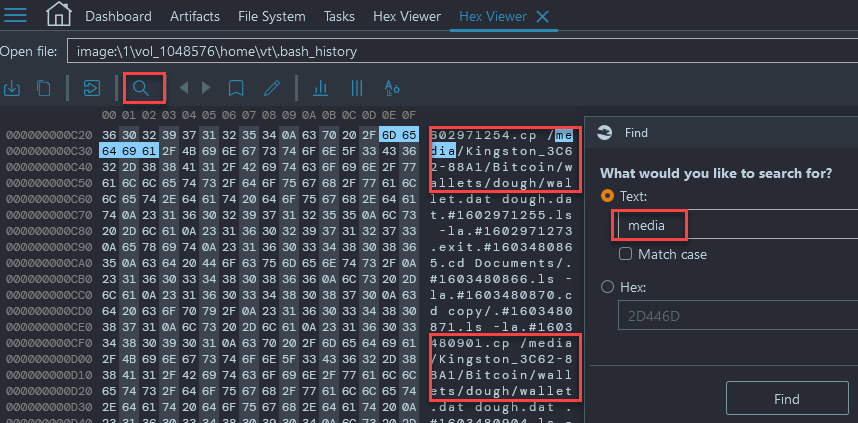
- Now to verify what we are seeing in .bash_history, we need to look into some system log files located at /var/log/kern.log.4.gz on 4/2/2021. Extract them from Belkasoft and unzip them in a Linux VM:

- Locate the USB that was plugged in on 4/2/2021, we will see the output for new USB device:
- Google the vendor and product id to get a USB type:
- Google what the USB type looks like:
Flag
Maker: Kingston, Model: HyperX Savage, Color: red+black (this task was solved 31 times)
6. CRM (Baby)
Question
What is the syndicate's CRM system URL?
Solution without Belkasoft X
- Load the image into forensic viewer of your choice and look for browser data in the /home/vt/.config/BraveSoftware/Brave-Browser/Default/Bookmarks
- Strings the file or open in a text viewer
- Select the custom-built URL: http://dopedoughyignlbq.onion (if you were following the story, the Chief gave you a hint about onion!)
Solution with Belkasoft X
- Navigate to Artifacts → Structure → Browsers → Chrome → Favorites
- You will notice several dozen URLs ending in '.onion' that seem to be randomly generated numbers and letters. However, one of these links spells out 'Dope Dough' which seems like a custom build URL:
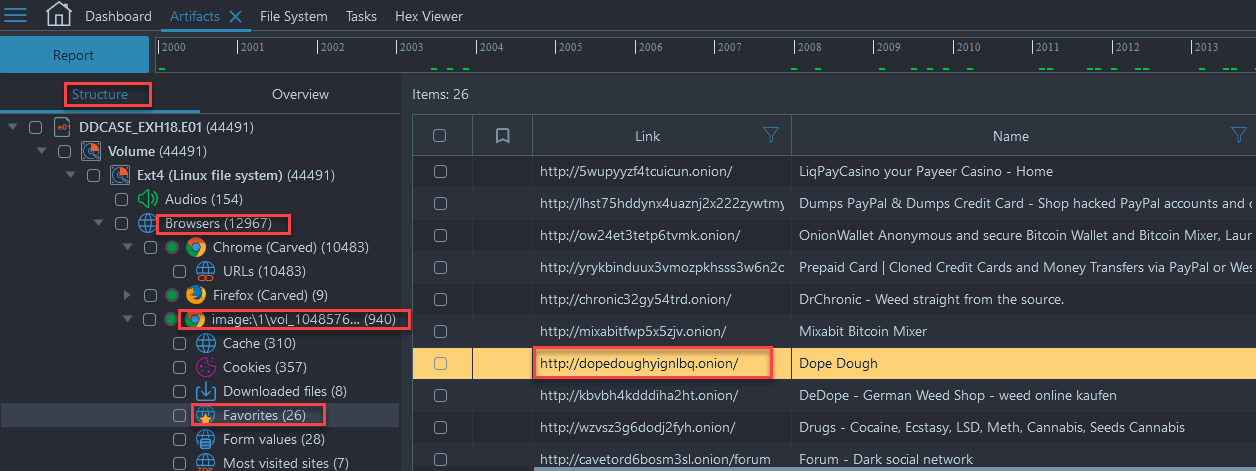
Flag
http://dopedoughyignlbq.onion/ (this task was solved 43 times)
7. Password (Tricky)
Question
What is the password to the syndicate's CRM system?
Solution without Belkasoft X
- Convert the E01 image file to DD format using FTK Imager or another tool of your choosing:
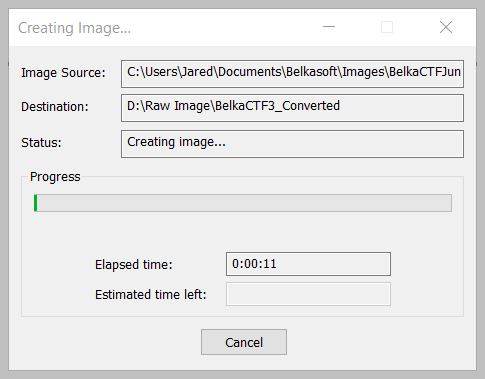
- Create a standard Ubuntu VM, and make the Hard drive 40GB Preallocated
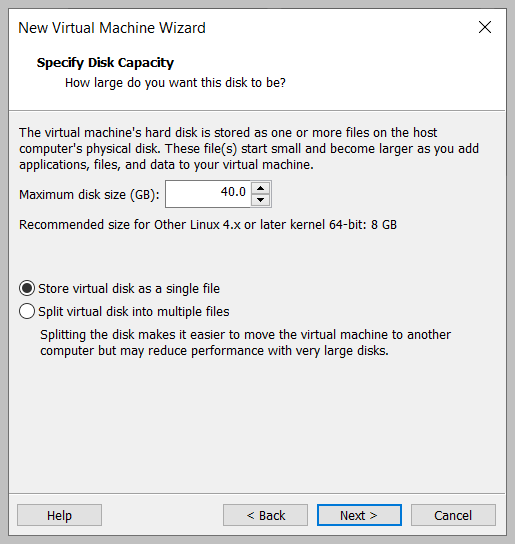
- Overwrite the *-flat.vmdk file that was created with your virtual machine with the newly converted DD image and boot the virtual machine.
- Once at the login screen, we now have to bypass the password for 'vt', to do this, we need to restart the VM from inside and hold the 'shift' key until you are prompted with the GRUB menu
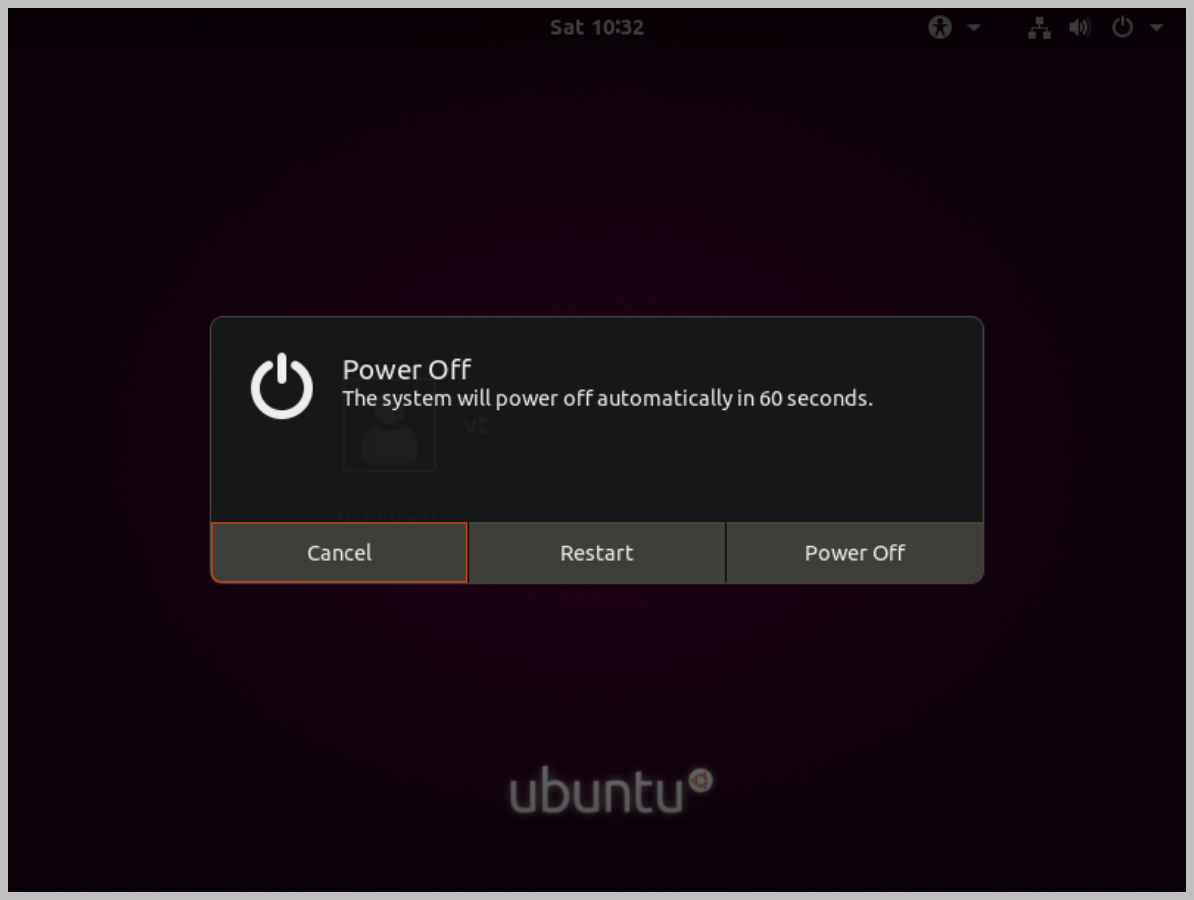
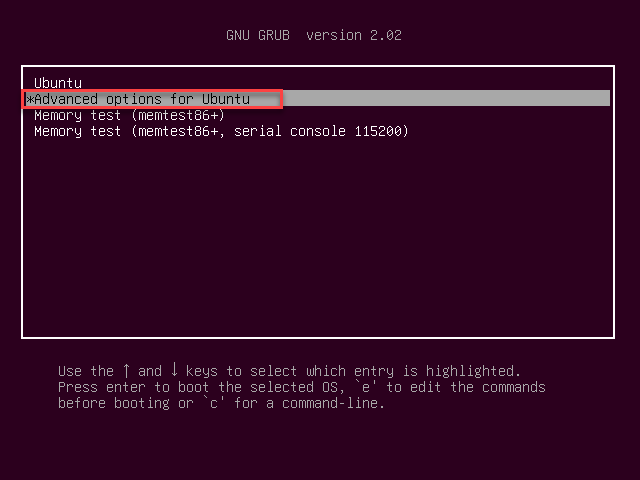
- Choose 'advanced options for Ubuntu' → Enter Recovery Mode → and select 'Root' → Hit 'Enter' key → change password for vt by issuing the following command: 'passwd vt' → Hit 'Ctrl+D' → and select 'Resume'
- Enter new password for vt → Open the Brave Browser and look for potential saved passwords in his browsers by selecting Settings → Advanced Options → Passwords → select the eye icon to view the passwords:
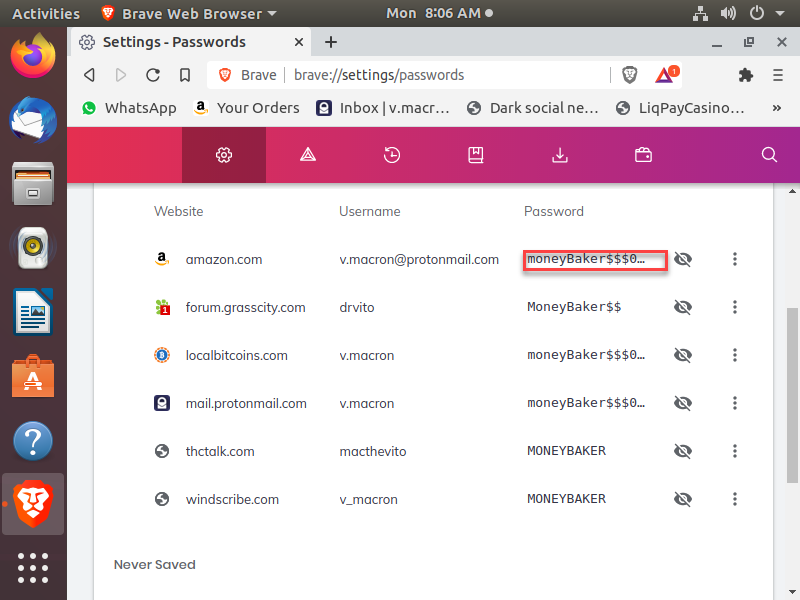
- There is no mention to dopedough in his saved passwords, but we can see a common password being used against all these different sites, so lets copy the top password and try it against the KeePassX password manager on the desktop
- Open KeePassX and supply the password found in the Brave Browser settings tab and you will be able to see the password for dopedough:
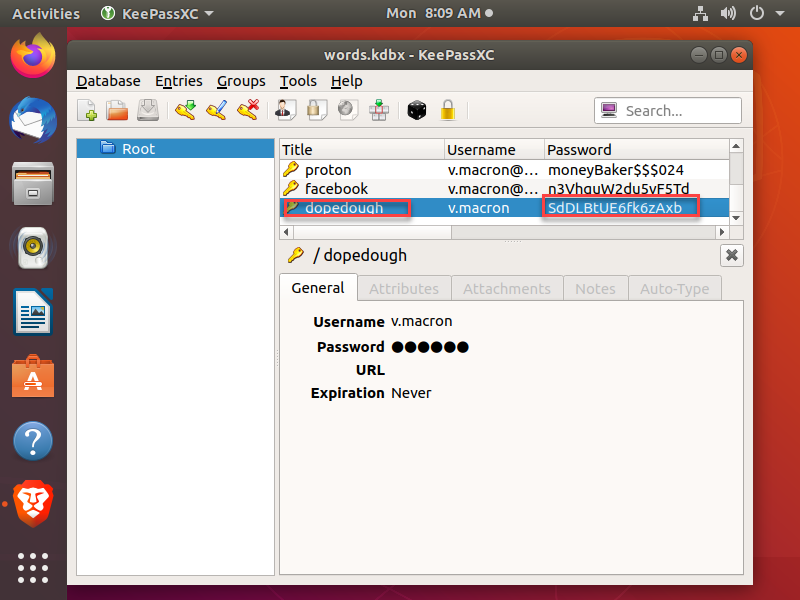
Solution with Belkasoft X
- The password cannot be found within Belkasoft X, but we have identified the user has favorited the CRM system URL from question 6, a necessary starting point to find the solution:
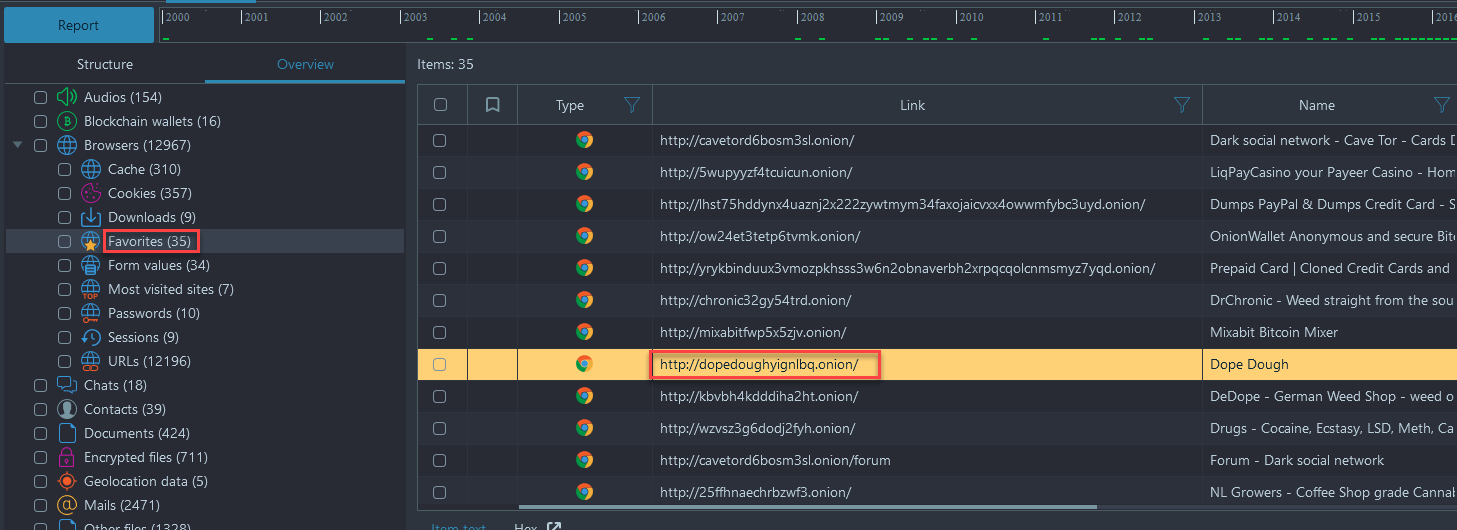
- Follow the steps above to complete the task, with the information gained through Belkasoft X
Flag
SdDLBtUE6fk6zAxbUTC (this task was solved 6 times)
8. Big Client (Hard)
Question
What is the name of the night club the Syndicate was providing drugs to in bulk?
Solution without Belkasoft X
- We must login to the CRM, within our VM, now that we know the login and password information we found in the last challenge: 'v.macron & SdDLBtUE6fk6zAxb'
- In the Virtual machine login to the CRM by browsing to the dopedough webpage → enter username and password → select 'Backup' → enter your email address → Record 1 and record 61893 and submit → it will send a backup of all orders to your email address, where you will download the backup.zip that was sent.
- Extract the 'backup.zip' and open in Excel or a viewer of your choosing
- Sort & Filter by highest margins and you will see an overwhelming amount of Las Vegas grid coordinates. A quick Google search points you to a general area where you can search for 'NightClubs'. They are too many, however:
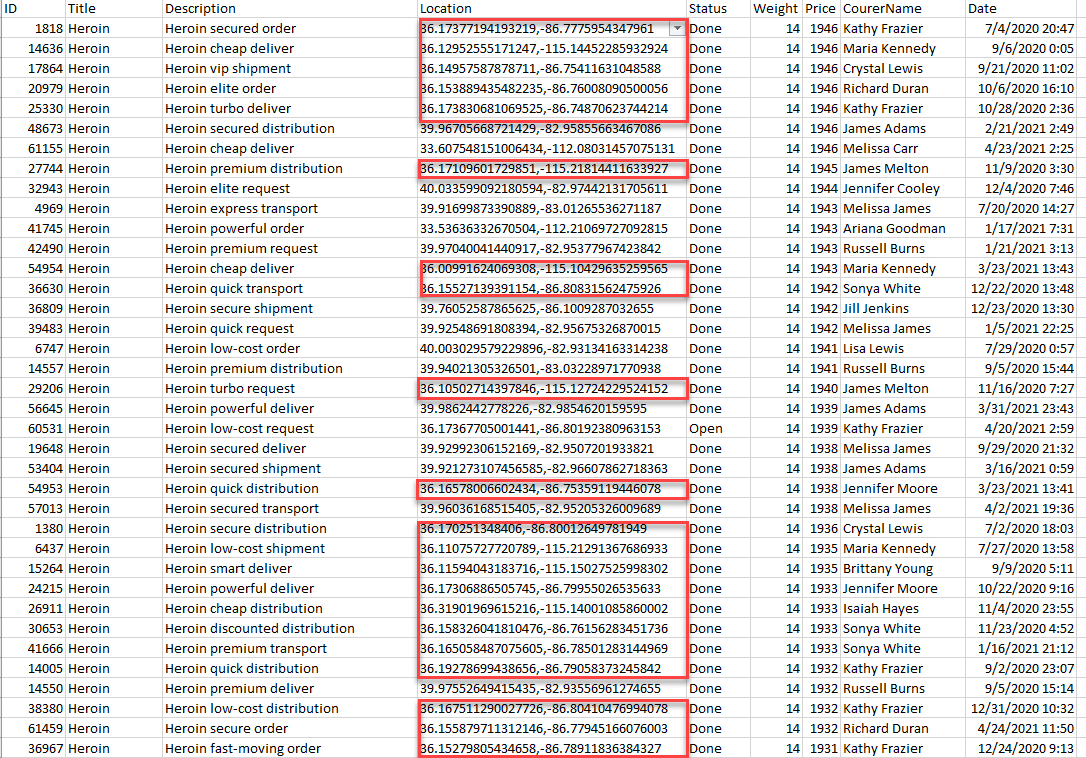
You can write a simple script to find out a location which has more hits, with some error margin to account for GPS noise. Your script may look like the following:
<?php
$buckets = [];
foreach (file("coords.txt") as $ln) {
list ($lat, $lon) = explode(',', trim($ln));
$lat = round($lat, 3);
$lon = round($lon, 3);
@$buckets["$lat,$lon"]++;
}
arsort($buckets);
print_r($buckets);
Once you found the most popular delivery location, you will get your flag:
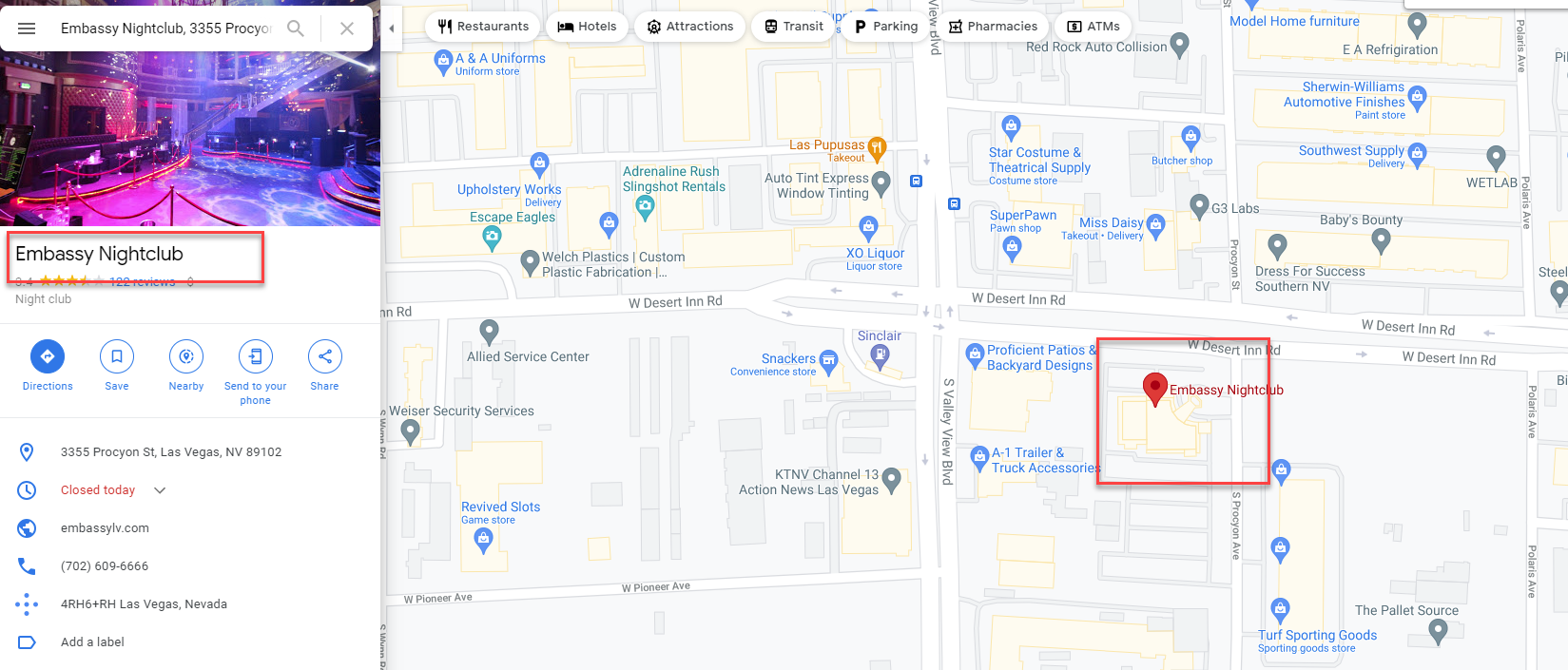
Solution with Belkasoft X
For this task, we must use content not available in the image to solve, we will follow the same procedures as the solution without Belkasoft X.
Flag
Embassy Nightclub (this task was solved 6 times)
9. Hosting (Tricky)
Question
What is the IP address their CRM system is hosted at?
Solution without Belkasoft X
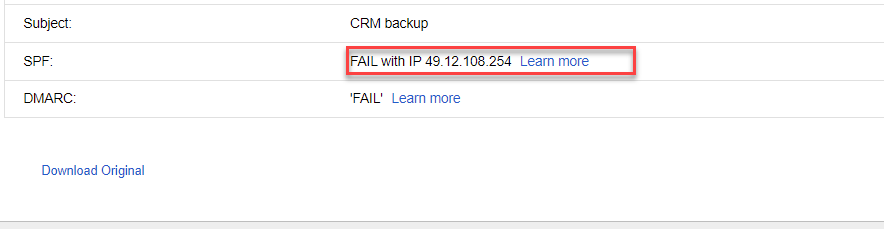
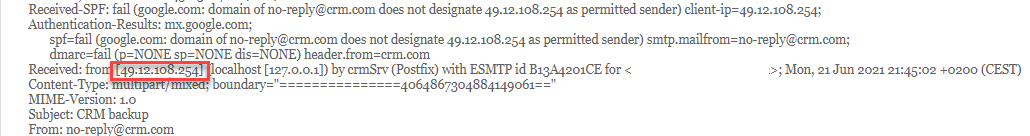
For this task, we need to go back into our email where we received the exported content from the CRM and examine the email headers to identify the IP address of the originator or by viewing the 'Original Message':
Solution with Belkasoft X
For this task, we must use content not available in the image to solve, we will follow the same procedures as the solution without Belkasoft X.
Flag
49.12.108.254 (this task was solved 10 times)
10. Tranche (Tricky)
Question
What are the cryptocurrency wallet addresses the Boss had transferred salary to in the last batch? (4 of them)
Solution without Belkasoft X
- Extract with any tool, the 'wallet.dat' file that is located within the
following folder:
/home/vt/Documents/copy/dough_apr/
- Once extracted, review the 'DAT' file with the Bitcoin Core application: https://bitcoin.org/en/download
- There are (4) outgoing transfers with labels, the destination wallet of these transfers is the flag.
Solution with Belkasoft X
- Navigate to Artifacts → Overview → Blockchain Wallets:
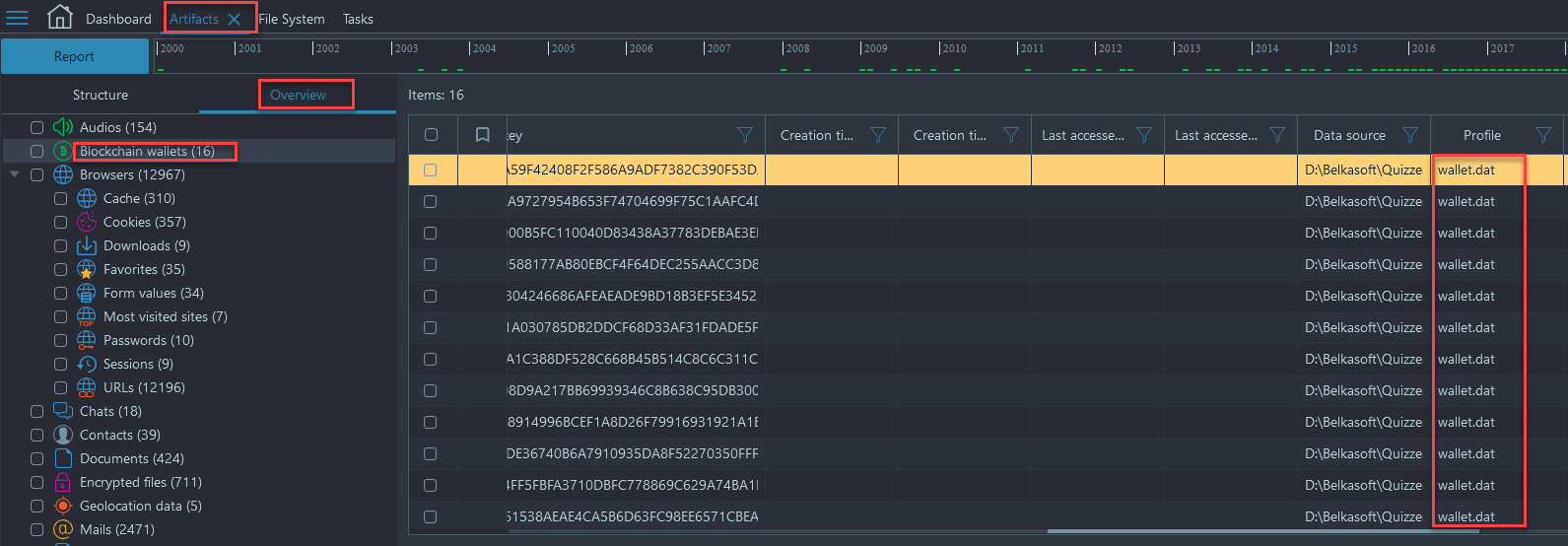
- You will see that all of the Blockchain wallets were found in a file called wallet.dat. Look in the 'Properties Pane' and look for origin path, which will show you were the file resides on the image, either right click and show on structure and then right click again and choose show on File System or follow the navigation within the File System Viewer below:
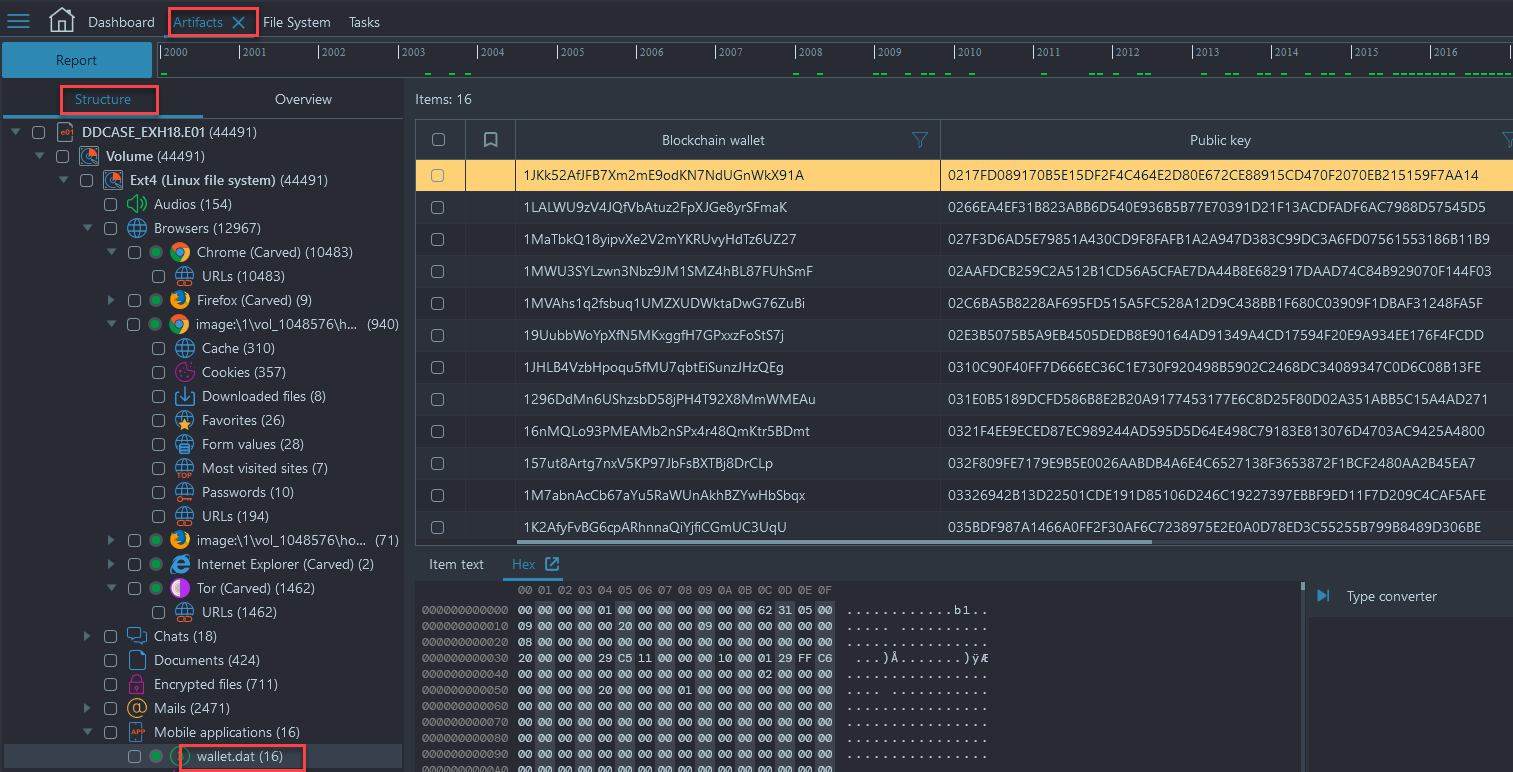
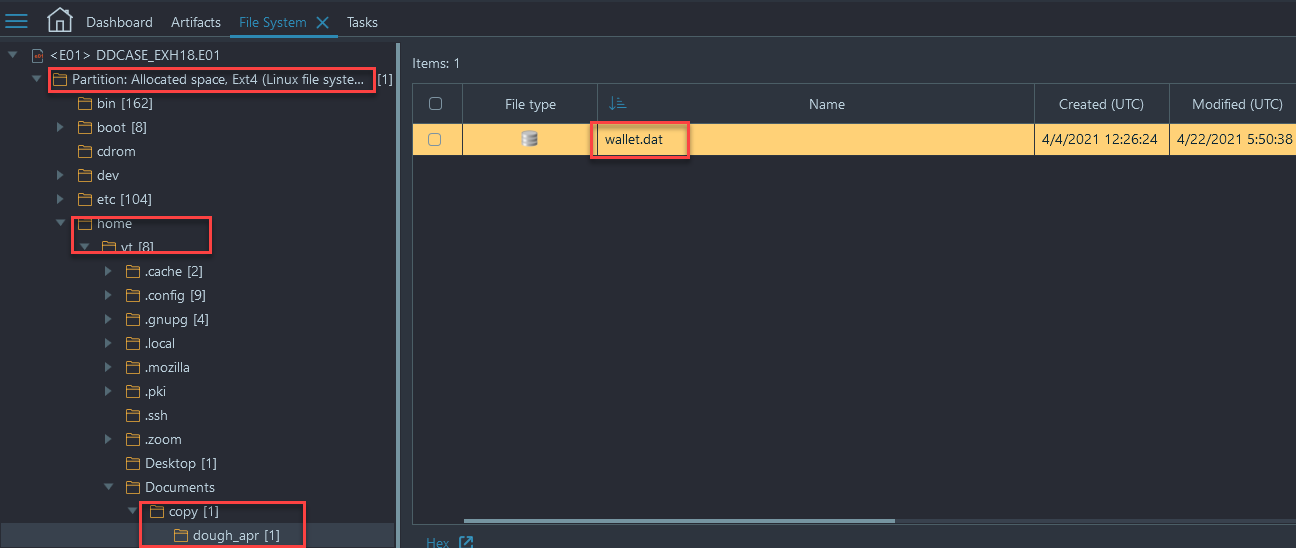
- File System → /home/vt/Documents/copy/dough_apr/
- In this location we have a Bitcoin wallet database that we can examine outside of Belkasoft X
- Select 'wallet.dat' and right click → choose 'copy files to folder'
- We must download Bitcoin Core to view the contents of the database, you can download Bitcoin Core from https://bitcoin.org/en/download
- Once you have it downloaded, you can load the .dat file into it and view the contents
- There are (4) outgoing transfers with labels, the transfer destinations of those wallets will give you the answer:
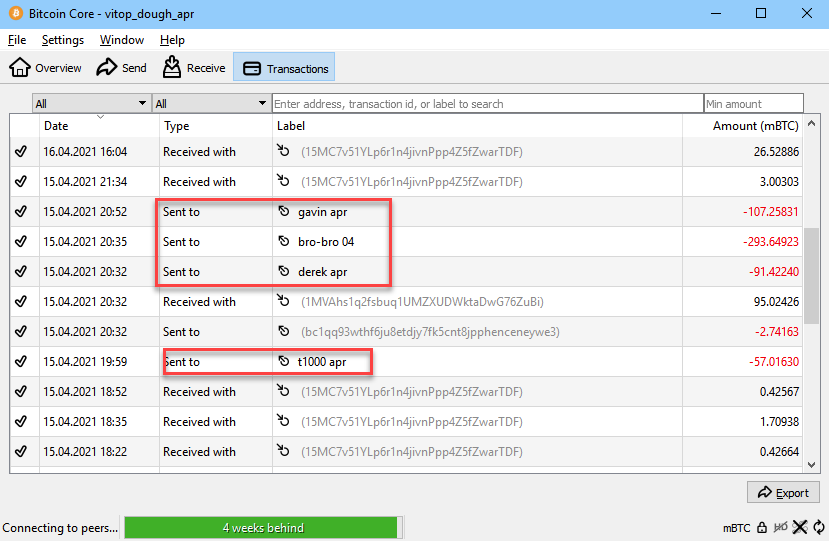
Flag
1B4uj2cMcVncGSsH7myYQF571JaojxCy4T
1HcZrD8gqDEtYhgmKJ2ECJAwA2stioknme
1FrxcR5Fj593ZbgYiiApVVEUV6PjvYfnqn
1NJXwLN5uC1PwWQ7yfvJiQTG76UUXTkrxr
(This task was solved 14 times)
11. Retrospective (Hard)
Question
What cryptocurrency wallets did the Boss transfer salary to in February? (4 addresses)
Solution without Belkasoft X
Follow same sequence of events as the solution with Belkasoft X, with a viewer of your choice.
Solution with Belkasoft X
- Navigate to File System → /home/vt/ → and view the .bash_history file by selecting the file, right clicking, and choosing the 'open checked files' option. We see the reference to a new wallet.dat being made on 4/2/2021:
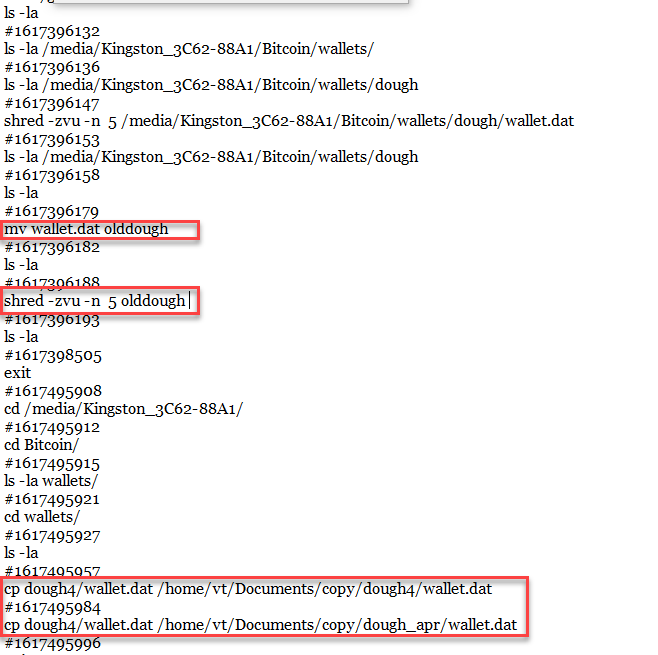
- Let's try searching the converted raw image we made earlier, perhaps we can find some remains of the old wallet file somewhere on the FS. For that let's take some characteristic byte sequence from the April wallet, and suppose that it will occur in any wallet file. For example \x09timesmart\x0a16, looking at the wallet file we have, it is an attribute of transactions:
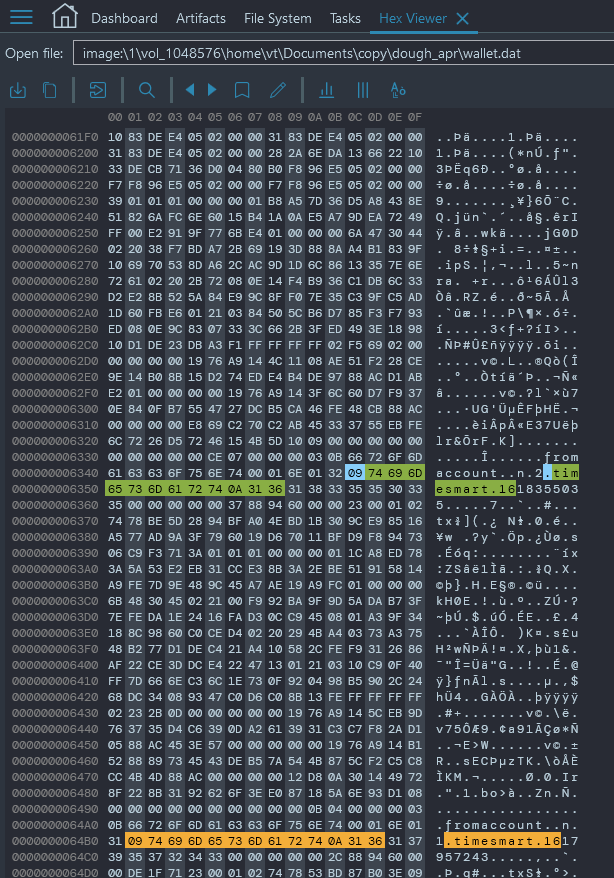
- Among that byte sequence occurences on the disk, there is a part where the timestamps near timesmart are just from February 2021:
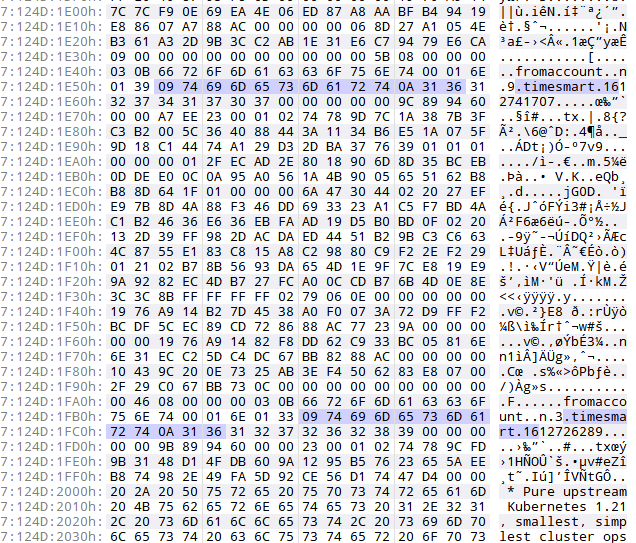
- Now if we look back at the wallet file we have, we can infer that the format is [label], 'name', [wallet]:
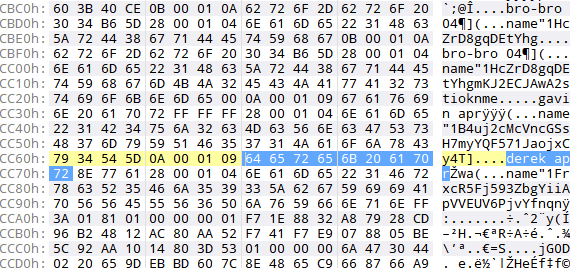
- So we can manually parse out the transaction labels from the raw wallet remains we found:

- If we filter these out by ones that relate to February, we receive our flags:

Flag
1GChpNsQ5x5yynwkuyXWq3Ea5JKYgdPKir
1CwWyNGGCjzmkuQnQRRA7H6zsUjt2Y9d8g
1PGLY1kFGi1RcZ4JAKY4v1VdcHJJwhY1Hs
19yJnHa5smr63fdDBpwrJUBCkud8J6EbSn
(this task was solved 1 time)
12. Congrats
Well, this was just a fun task, which opened 1 hour before the end of the competition. To score, one had to click on any 'social share' link at the bottom of the task box. We deliberately did not check if an actual post was made, so it was easy to cheat :). We hope, however, that those who enjoyed solving the CTF will share their thoughts voluntarily. Your posts motivate the team, that's our reward!
Please do not forget to use the #BelkaCTF hashtag.
Flag
flag{7hank5_f0r_pl4y1ng_and_s33_y4_n3xt_t1me} (this task was solved 21 times)
