How to Configure Hashcat Brute-Force Options in Belkasoft X
Belkasoft X supports integration with hashcat to brute-force certain password hashes found during data analysis. For detailed setup and usage scenarios, refer to the Belkasoft X User Reference Guide.
This article provides an overview of hashcat attack modes and other options that can help recover passwords more quickly if there is information about possible password patterns used by the creator.
Hashcat brute-force parameters are defined in the Hashcat options window:
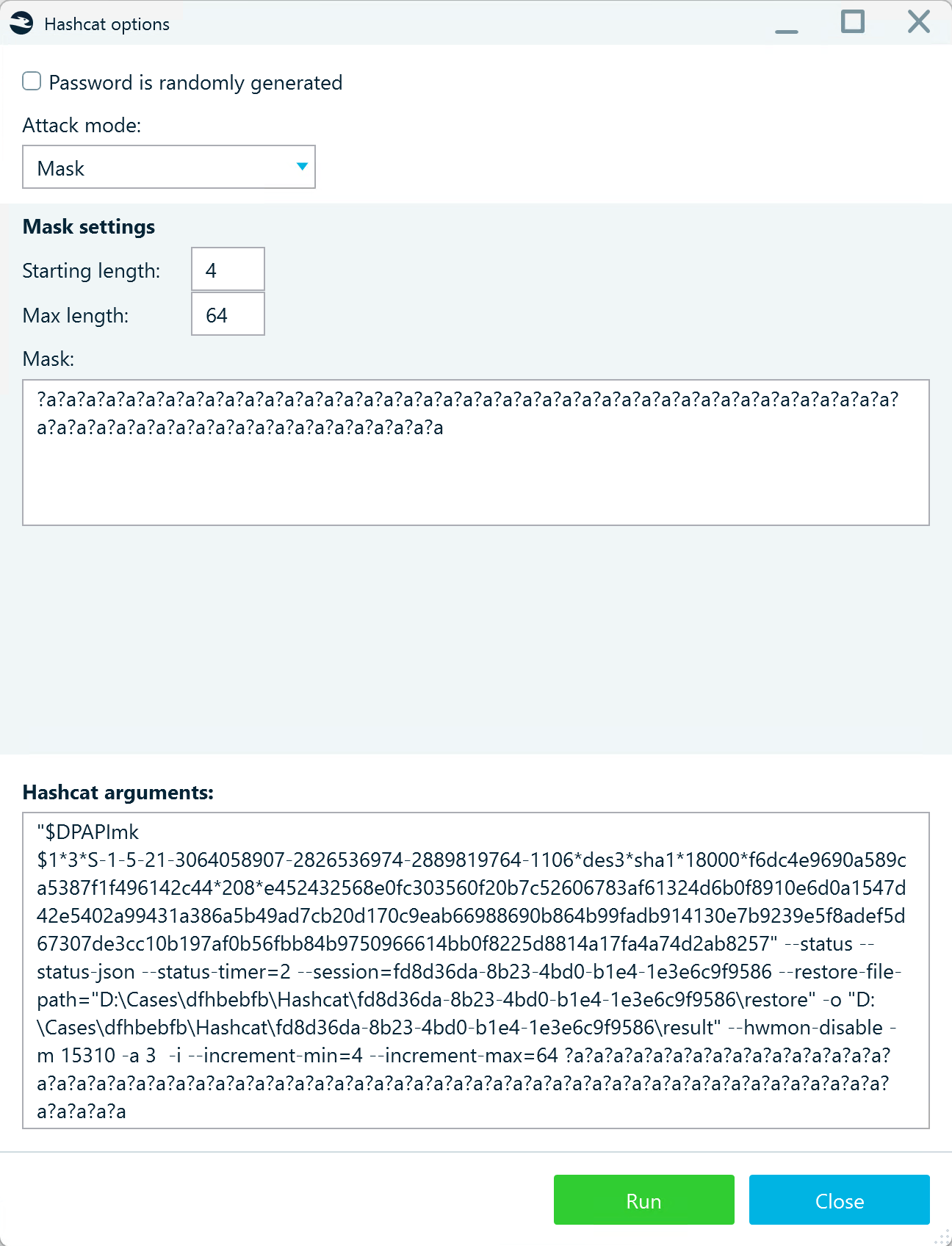
Let us review the available options and best practices for their usage.
Password is randomly generated
Select this checkbox if you assume that the password characters are not arranged according to any statistical patterns. For example, the password does not contain words, dates, or characters that are adjacent on the keyboard.
When this option is enabled, hashcat applies algorithms that are more effective for random passwords. You can use it together with different attack modes.
Attack mode
Hashcat attack mode settings are designed to reduce the number of possible character combinations, thus optimizing the brute-force speed. The available options include:
Mask
This hashcat mode enables you to define a pattern (or mask) for password guessing. You can specify the range of characters in the password, the exact characters, or their types.
Here are some common placeholders used to identify character types:
?l= lowercase letters (a–z)?u= uppercase letters (A–Z)?d= digits (0–9)?s= symbols (!@#$% and so on)?a= all of the above
You can find more information on how to create a mask in Hashcat Wiki - Mask Attack.
By default, Belkasoft X is configured to search for passwords between 4 and 64 characters in length, using all character types. This default is equivalent to a simple brute-force attack. If you know the possible password length or specific characters it contains, you can update the mask to reduce the number of combinations to try.
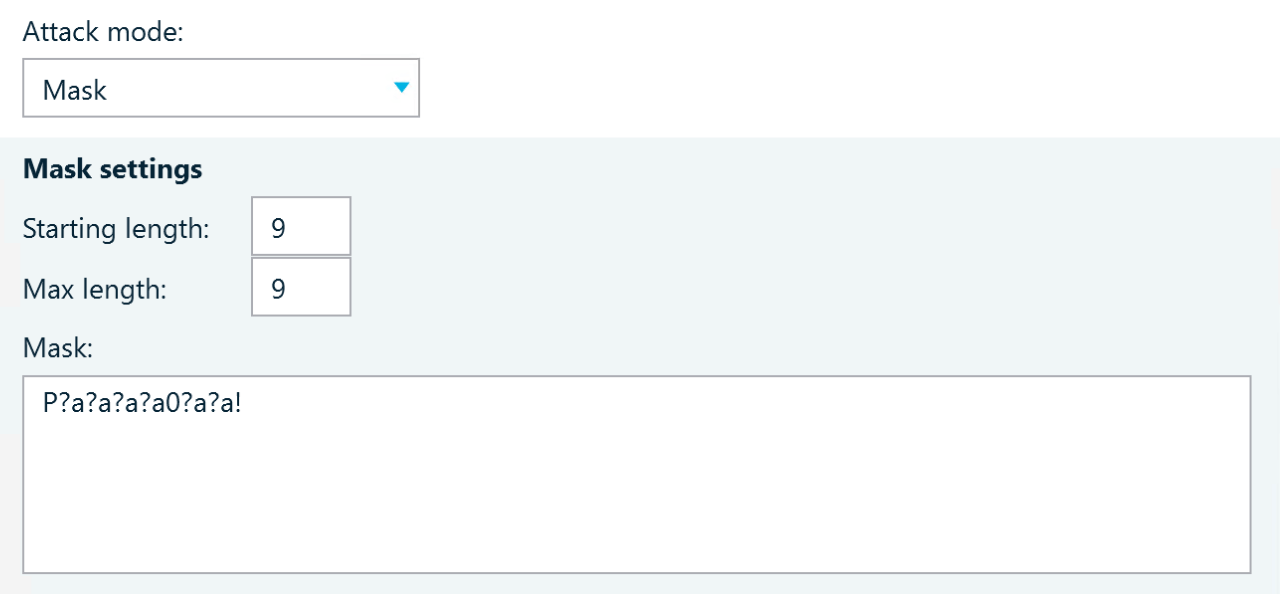
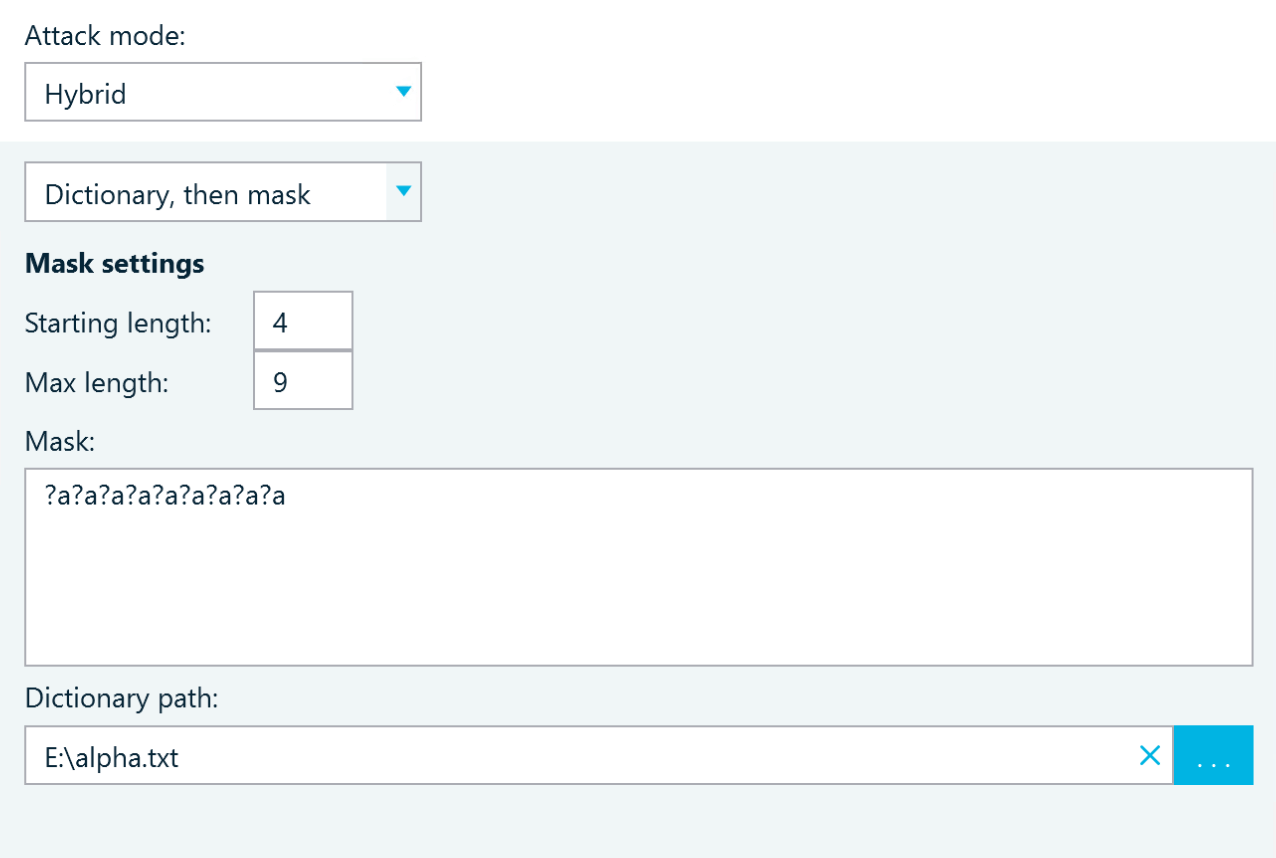
For example, with the mask shown in the screenshot below, hashcat will only check passwords with the following characteristics:
- Are exactly 9 characters long
- Start with P
- Have 0 as the sixth character
- End with !
Dictionary
This hashcat attack mode uses password values from a selected dictionary. You can create a custom dictionary, use a set of common passwords available online, or add a key dictionary generated from another Belkasoft X case.
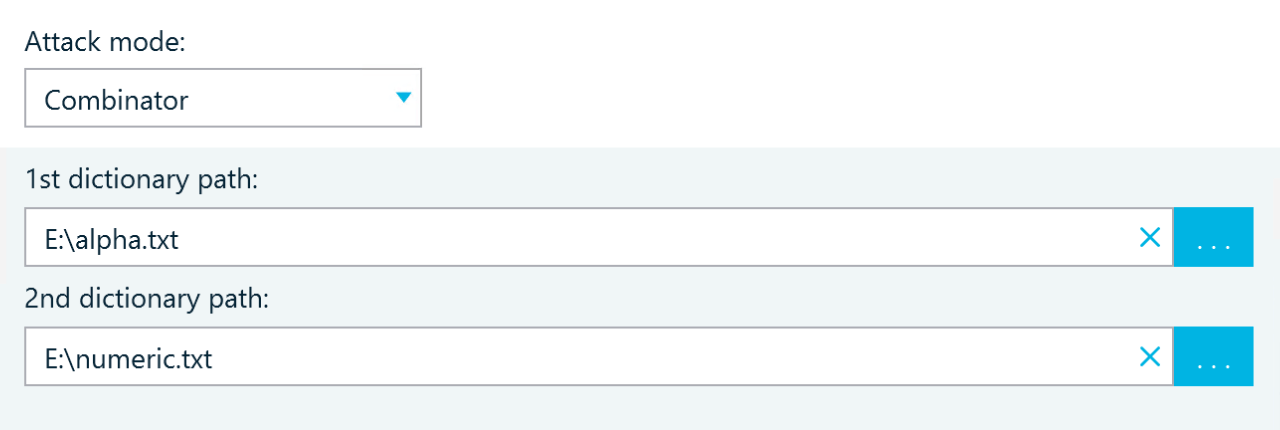
Combinator
This hashcat attack concatenates two dictionaries.
For example, if leaked password data shows that the password creator tends to use passwords consisting of a city name and a postcode, you can configure two dictionaries, one with city names and one with postcodes. Hashcat will combine the values during the attack to generate possible password candidates such as "Berlin10115" or "LondonSW1A".
Learn more in Hashcat Wiki - Combinator Attack.
Hybrid
This hashcat attack mode is similar to the Combinator attack, but it combines a Mask and a Dictionary. You can arrange them either in the Mask, then dictionary or in the Dictionary, then mask order.
This type of attack can be useful when you know that the password may include certain character combinations with random numbers or symbols at the beginning or at the end.
Learn more in Hashcat Wiki - Hybrid Attack.
Case key dictionary
This attack mode uses the key dictionary generated from the current case as a brute-force dictionary. No additional settings are required; simply select this attack and click Run. Belkasoft X will automatically collect character combinations that resemble passwords from the current case and use them for your hashcat brute-force attack.
Hashcat arguments
When you select options for an attack, Belkasoft X records them in the Hashcat arguments field. For instance, here is what the Combinator attack arguments for a Windows password hash (DPAPI) may look like:
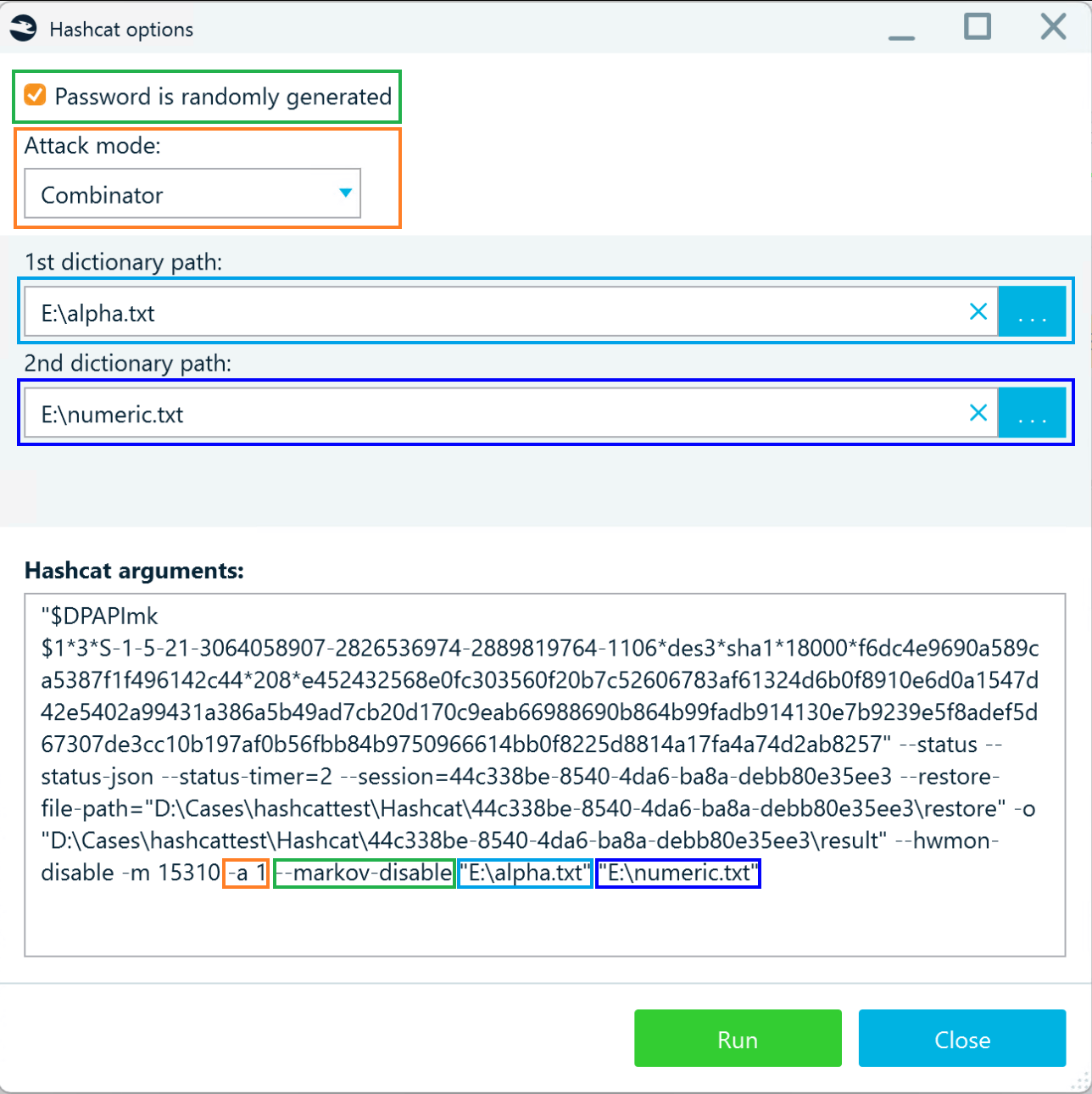
You can use this field to specify additional password generation parameters, optimizations, or other arguments supported by hashcat.
Note: Updating any options above the Hashcat arguments field clears manually added arguments.
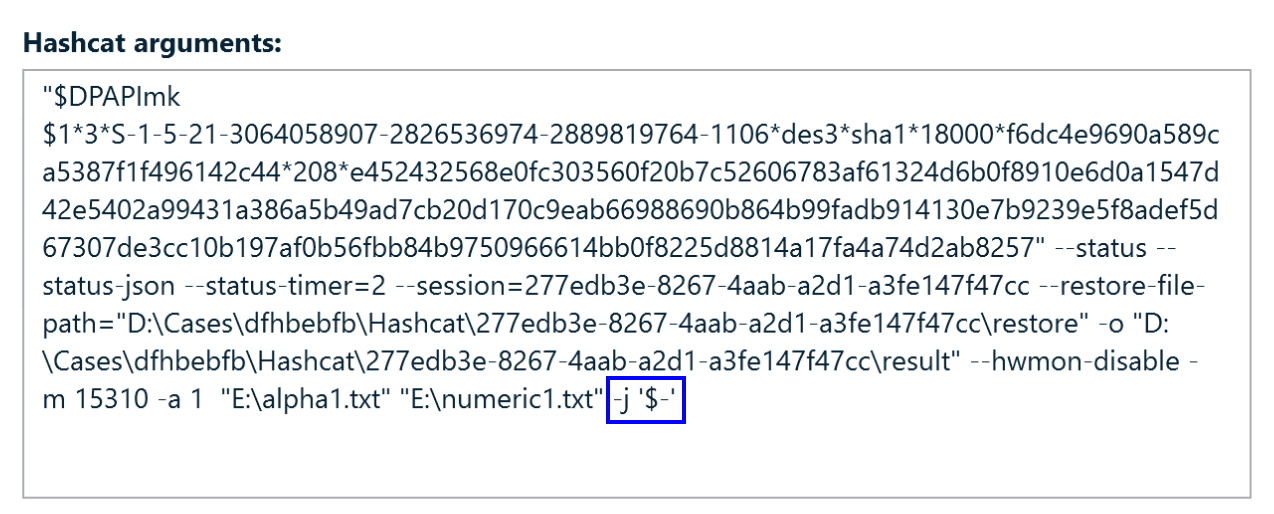
Some arguments can alter password generation rules. For example, if you are configuring a Combinator attack, and you know there is a hyphen between the first and the second part of the password, you can add the -j '$-' hashcat rule that will add a hyphen after the keys from the first dictionary:
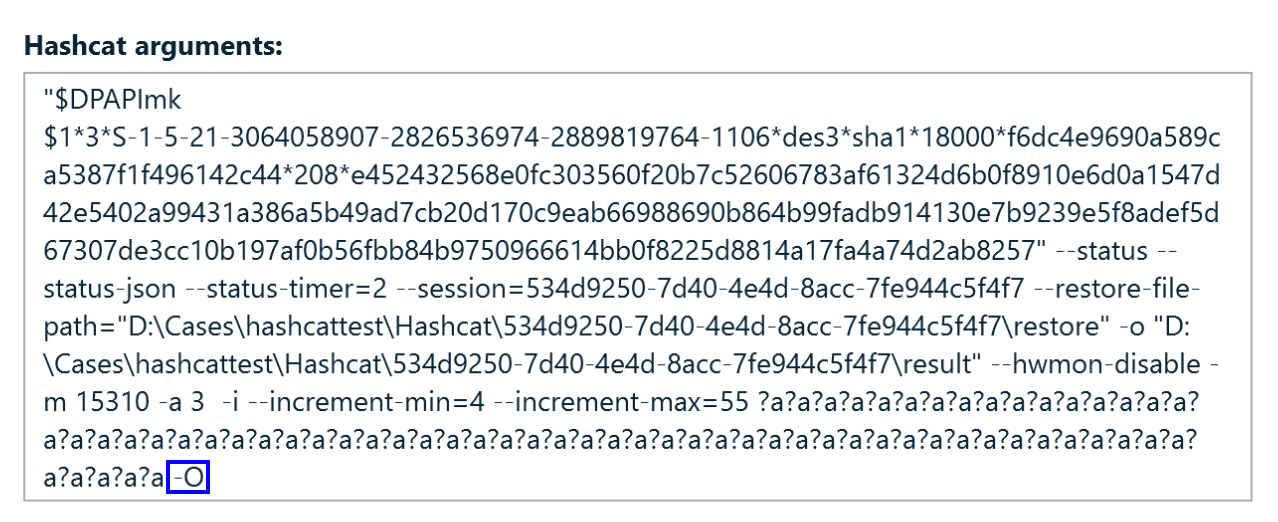
Hashcat also provides options to improve attack performance. For example, the -O argument enables optimized kernels, which are specialized GPU code versions designed for high-speed cracking. Using optimized kernels can significantly increase performance, but it also reduces the maximum supported password length (typically to 55 characters or fewer, depending on the hash type). For additional information on password length limitations when using optimized kernels, refer to Hashcat FAQ regarding the password length.
For more details on existing arguments and their usage, refer to Hashcat documentation.
See also:
Encryption amidst digital forensic and cyber incident response investigations
Mobile Passcode Brute-Force Module
iOS Signal Decryption
