Davide Gabrini, better known as Rebus, is a digital forensics expert and a law enforcement officer since late 90's. He collaborates with Italian universities and academic institutions and he's a part of Tsurugi Linux project. Since 2007 he publishes the almost daily newsletter Rebus'Digest, dedicated to digital forensics, cybercrime, hacking and related topics.
"In summary: Belkasoft is the legendary all-in-one solution, the concept chased with mixed success by many vendors over the past two decades."

Like many other technicians in the sector, I recently had an opportunity to test Belkasoft X, the renewed version of Belkasoft Evidence Center. The aims of the Belkasoft's flagship product are ambitious: a single solution for acquisition, analysis, and presentation of digital evidence, which can help an investigator to extract data from memory, mobile devices, and cloud services, it can also analyze the content of physical images, filesystems, unallocated space, archives, etc., identifying and interpreting the artifacts produced by operating systems and popular applications. In summary: Belkasoft is a legendary all-in-one solution, the concept chased with a mixed success by other vendors over the past two decades.
For my tests I used a forensic image of a Windows PC (produced by the trusted FTK Imager in EWF format), an image of a Xiaomi Android smartphone physically extracted by means of UFED 4PC and an Instagram account credentials. And later I included a Samsung Galaxy binary image.
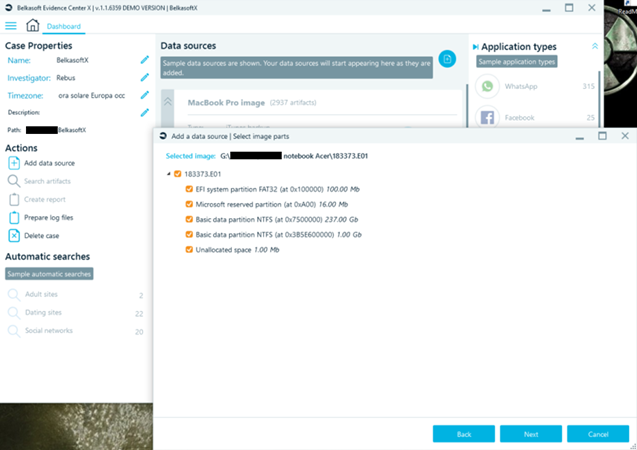
The first thing you will obviously love in Belkasoft X is a friendly and intuitive user interface. I will skip the first stage, or a case creation part, to demonstate the screenshot relating to the import of the first forensic copy. Once the E01 file has been indicated, Belkasoft X shows the detected partitioning and allows you to choose on which areas of the disk image to start workigng.
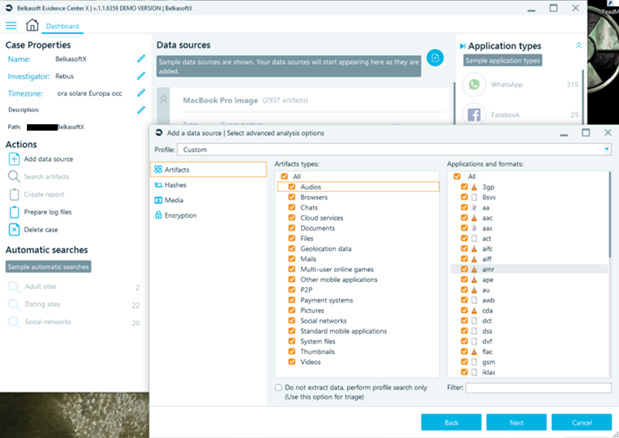
The next step is to instruct Belkasoft X which artifacts are of interest for the ongoing investigation, choosing from a wide set of possibilities divided by category:
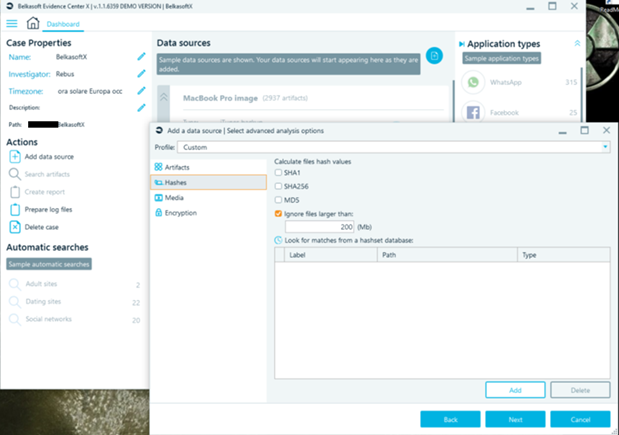
There is, of course, the possibility to calculate the most common hash file that will be processed and provided for the automated comparison with any hashset. Of course, it is possible to use both lists of 'known bad' elements to immediately identify content of interest, and lists of 'known good' ones, to allow the analyst to 'hide' irrelevant files for analysis.
The Media section offers the possibility to analyze the visual content to identify relevant elements such as faces, weapons, pornography or text (this functionality is very useful for numerous screenshots of messages often stored on mobile devices). There is also a file entropy estimation function which aims to identify any encrypted containers.
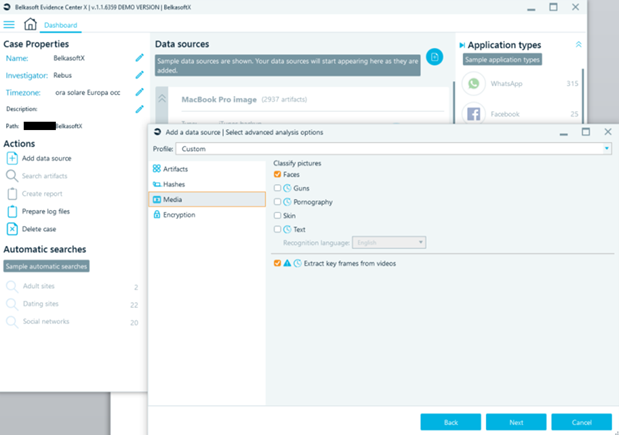
While scanning isin progress, identified and reconstructed elements progressively populate this impressive dashboard:
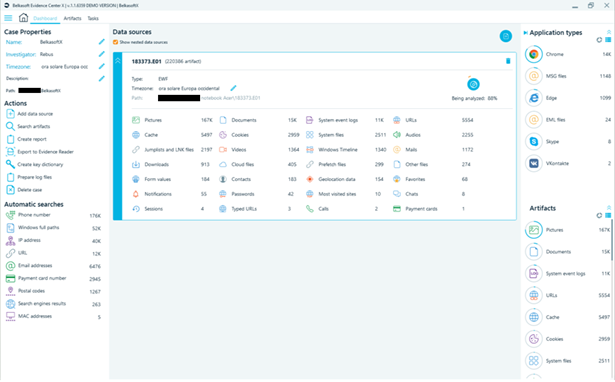
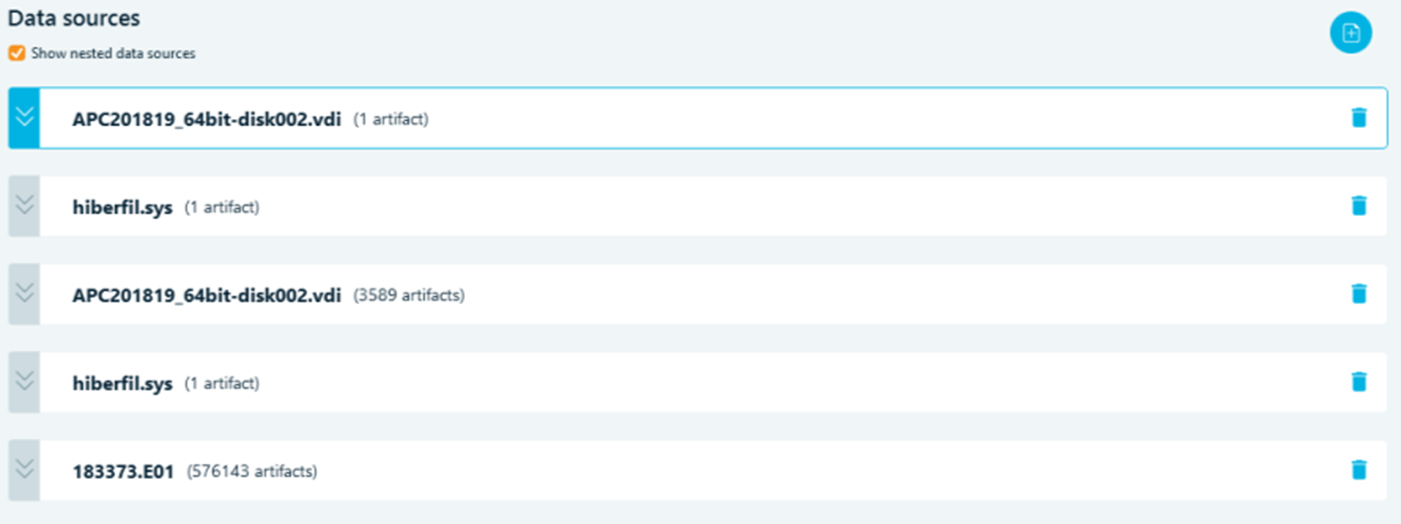
If during the analysis of a data source, one more data source is identified inside (i.e. a logical container such as a virtual disk, or a phone backup), it is automatically added as the source of the case and its analysis is performed as well:
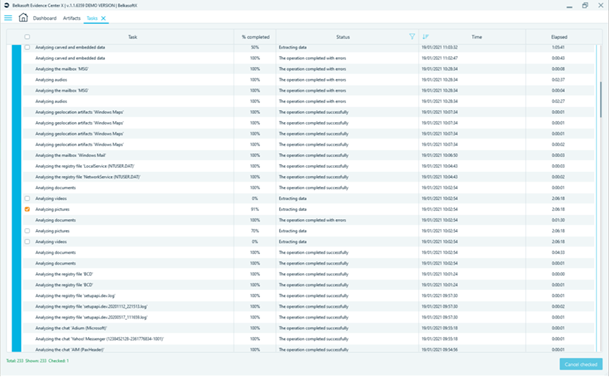
The Task manager offers an immediate and intuitive view of the progress of the work, it is also useful for audit purposes. When the system requires to add missing information from an examiner (for example, when an encrypted content is detected, for which it is necessary to enter the password to proceed with the analysis of the content) the alert "Enter missing data" appears and allows you to enter (when known) the missing information.
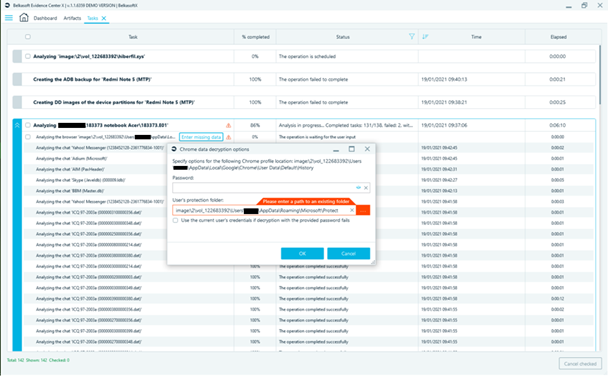
In general, you have a rather detailed view of tasks in progress and some limited possibilities for interaction (I took advantage of interrupting the tasks, which turned to be too long for processing, but I would prefer to pause them and, probably, resume later without restarting them all over again).
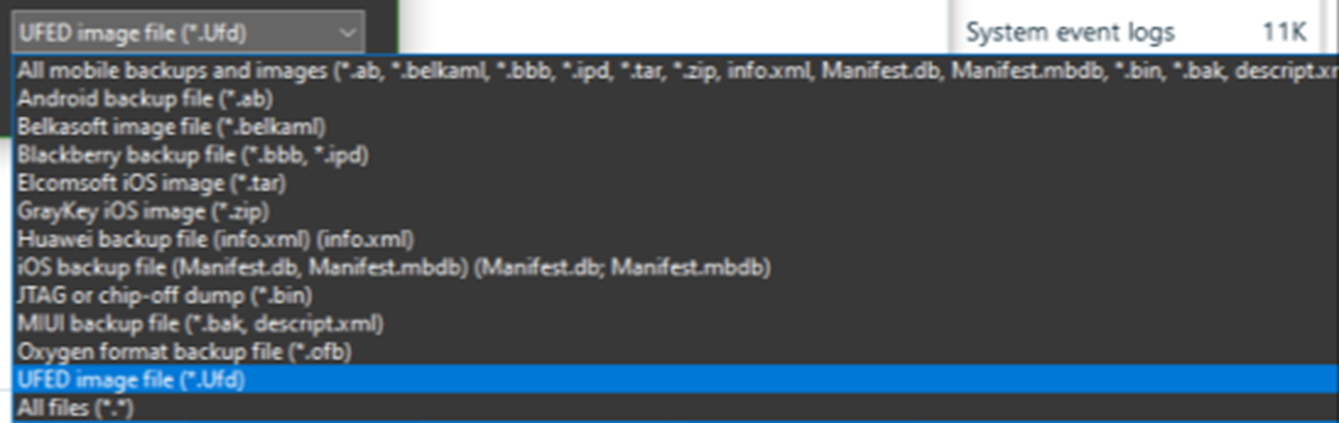
The acquisition of the Android smartphone with Belkasoft X was not successful: this model actually has limitations imposed by the manufacturer, and the acquisition procedure turned out to be problematic even with other tools. However, I managed to get a physical dump from UFED. Belkasoft X supports several image formats for mobile devices, including the raw binary, and, luckily, the UFD descriptor of the binary file of my interest.
I also took the opportunity to import the image of a Samsung Galaxy S9 which I previously analyzed with the other tools. I should mention here, that Belkasoft X offers several alternatives of mobile devices acquisition, including advanced ones, which include exploits for MTK chipsets, checkm8-based acquisition, full filesystem extraction from iOS devices using agents (you should have Apple developer credentials to be able to use agents).
Finally, the import of the cloud account, in my case, it was Instagram.
With Instagram, I noticed a shortcoming. The only authentication method proposed for this cloud service is through the combination of a username and password, there is no way to import session tokens from the outside. It is not possible to operate via proxy, so you need an Internet access, and I also found that there is no support for managing A two-factor authentication. The account under my investigation was configured to receive OTP via SMS, but for now Belkasoft X does not provide the insertion of the OTP, (in this case, it would be necessary to authenticate via browser, deactivate 2FA and return to Belkasoft X to perform the extraction, but it will be next time).
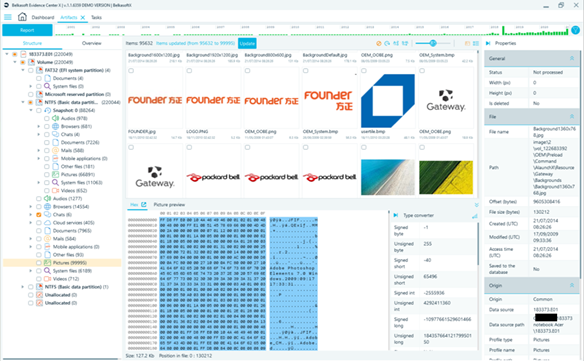
Finally, we are at the Artifacts section, which allows you to view what Belkasoft X has identified and interpreted, following the logical structure of data sources (Structure), or by combining all the artifacts by category, regardless of their origin (Overview).
The aggregation of geolocation data is extremely useful, especially in combination with the timeline filter which is always displayed at the top of the workspace, but my workstation is offline, so ...
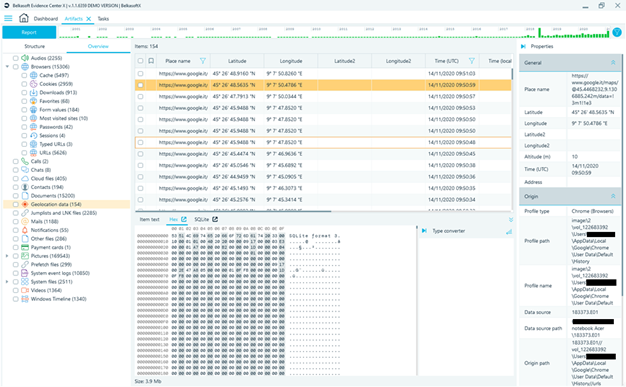
… I cannot see the GPS coordinates represented on the OpenStreetMap maps.
Offline maps support would be useful. However, I can easily export the data in KML format and have a look at it in Google Earth app, for example.
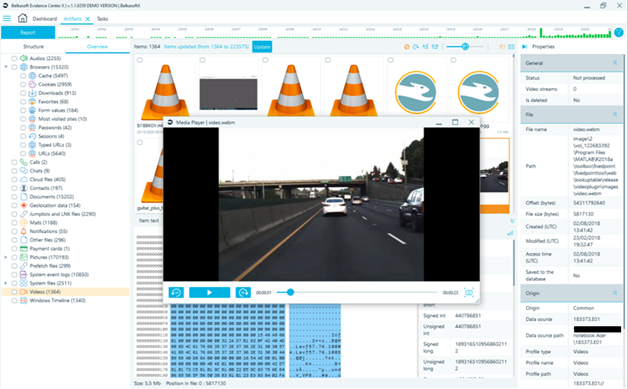
The gallery dedicated to videos is useful as well, but it can be improved by integrating the inline player into the basic interface to avoid the tedious double click at each videofile to view it:
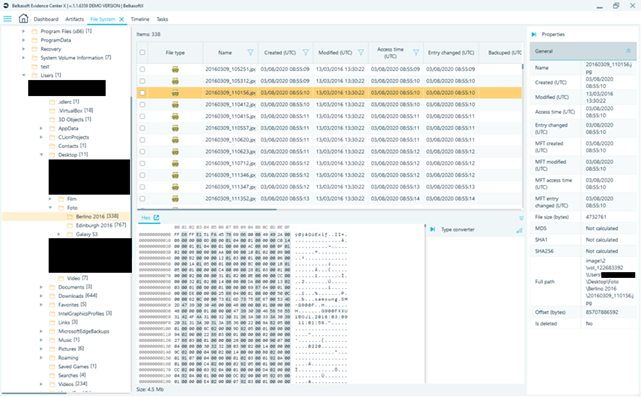
The Filesystem section allows you to browse the data sources by hierarchically going through the filesystems presentation, as almost any forensic software does. The interaction with the files, however, is limited, and the number of viewers can be increased (I would suggest along with the HEX viewer to add, for example, an extraction of strings and a preview of the contents - at least for some universal formats such as jpeg, pdf, office ...).
Some types of files (Windows registry, Plist, SQlite database) can then be analyzed with specific modules, which can be recalled at the same time, or sent to VirusTotal for feedback. As I was testing the product being offline, I have not checked whether it is possible to choose to send only the MD5 hash of the files, or whether the entire content is sent anyway.
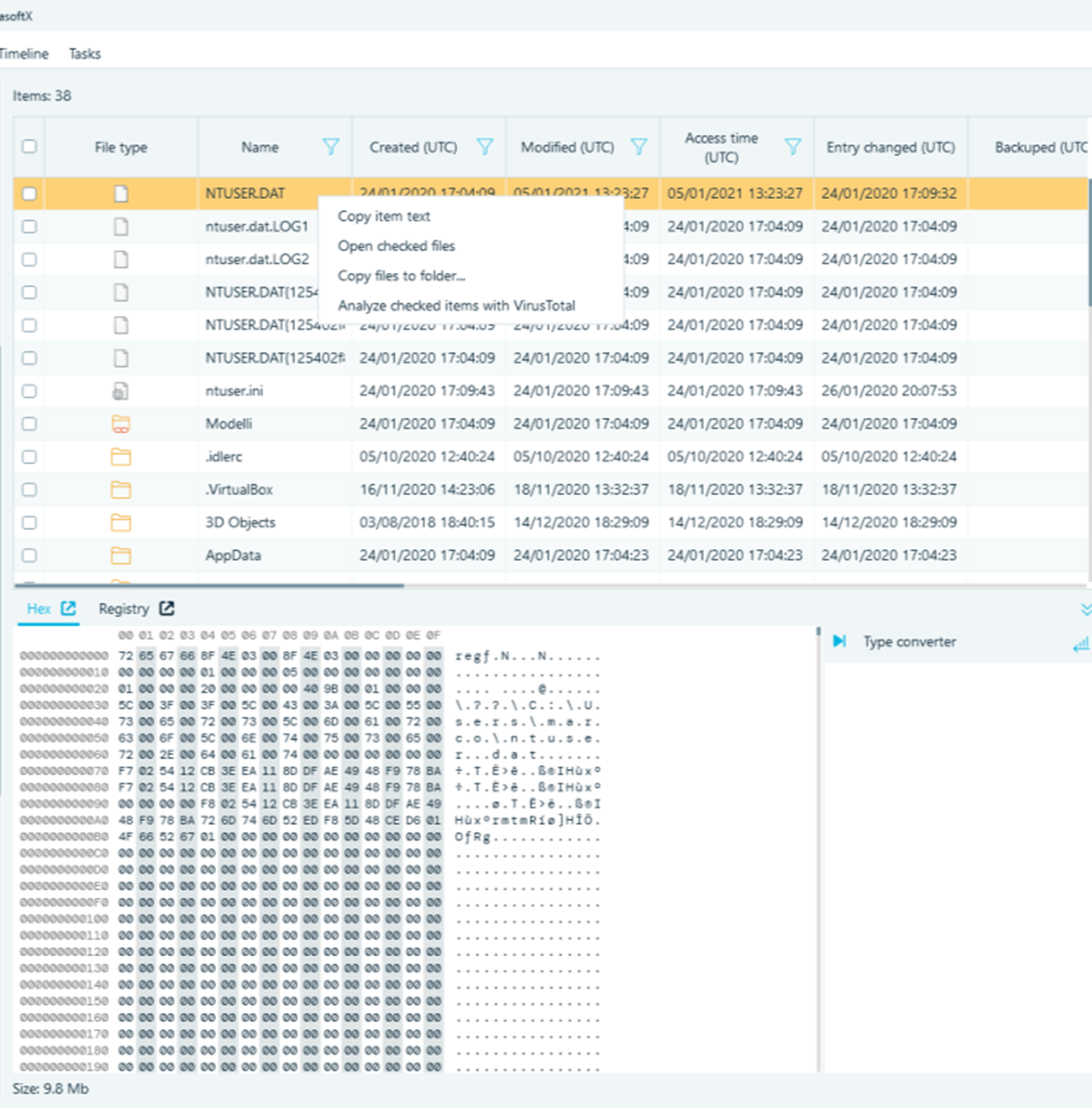
I had an issue when opening the Chat node, which should contain a few thousand WhatsApp messages from a Samsung Galaxy S9, but something was wrong:
Fortunately, the Task manager kept track of the analysis, also noting the failed scans and keeping an effective log, so I could at least understand what happened:
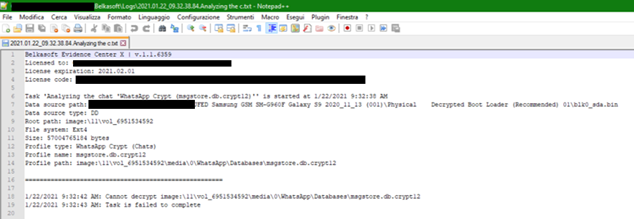
Unfortunately, I was not able to solve the problem. Since it is a physically acquired image, the key to decrypt msgstore should be available, and if I bothered to use the filesystem module, I am sure I could have isolated it, only ... I would have had to use it with an alternative tool anyway, since Belkasoft X limited itself to signaling the task as failed but did not ask me to insert the key, nor it offered the possibility to insert it manually. In any case, the recovery of the key and its use for the intelligible chats reconstruction is just one of those tasks that I'd love to delegate to an automated software, without having to worry about it personally, maybe only in some exceptional cases.
Last word on reporting: all formats you may possibly need are supported (text, HTML, XML, CSV, PDF, RTF, Excel, Word, EML and, as anticipated, KML), but the most valuable resource is undoubtedly the ability to export the entire database or parts of it with a portable viewer, which I am sure is the ultimate solution for the most of my reporting needs.
Final judgement
I find that a great job has been done, and there is a ‘desperate’ need for a digital forensic tool like this, which make an analyst's work simpler and bring it back to a humanly manageable dimension. Over the last years we observed a continuous growth of the amounts of data we have to analyze, and the trend will stay the same in the future, so it is essential to be able to rely on digital forensic tools, which are able to acquire a great amount of data to perform a high-level analysis, correlations, visual representations, filtering, aggregations, and deduplications… But without losing the opportunity to go into details to isolate the single record, parse the single blob, split the bit in four. And all these functionalities exist in Belkasoft X: the great work that has been done in this direction can be perceived and appreciated.
In particular, I love the ease of use, thanks to the simple and intuitive interface, and an extensive support of various data source formats and especially multiple artifacts. In the course of my tests, Belkasoft X proved to be very stable, reasonably fast on the analysis stage and pleasantly responsive to user actions.
As the vendor ambitions are extremely high, it should be admitted that there is still so much more work to do. Fortunately, Belkasoft has proven to be a firmly active company attentive to users' needs. The proof of it is the fact that some of the feedback I provided after my tests has already been taken into consideration and included in the to-do list of the upcoming improvements, so I am convinced that a product like Belkasoft X will never be a finished work, but will be in a constant development, and that is exactly what we need.
Last words on Belkasoft X pricing: I wouldn't think about it too much. The price of the first year starts at 4,500 euros, and then becomes 1,400 in the following years. Maybe it seems like a lot, but if you count how many man-hours a similar program can save, you find that it is quick to pay for itself and support itself.
See also