Lorenzo Martínez Rodríguez is a Computer Science Engineer, who has an extensive experience in IT security consulting companies, as well as multinational security vendors.

He currently runs his own company, Securízame, specializing in communication systems and network security. Lorenzo is a co-founder and editor of the security blog Security By Default. He is also an expert in the National Association for Cybersecurity and Technological Expertise, ANCITE.
"Belkasoft Evidence Center X is a very useful tool for digital forensic analysis, that identifies and retrieves information, classifying it by type of file, which complements the manual investigation processes that we develop at Securízame."
Introduction
At Securízame we carry out investigations of cyber security incidents and commissions of computer forensic expertise on a regular basis. Depending on the case, the methodology that we usually use implies the identification of sources of evidence to be analyzed, from of the interpretation and correlation of system, user and system forensic artifacts of files.
However, there are several tools that forensic professionals can use to automate and enhance part of this analysis.
In the forensic field, among the best known and most veteran commercial suites is Belkasoft Evidence Center. A fully functional trial version is available. We have been able to test the version 1.0.5969 of Belkasoft X and we want to present our experience with the tool.
The phases of a digital forensic analysis investigation include the acquisition of evidence, their analysis and interpretation, the generation of the results report and the presentation of these to whom it may concern.
The GUI
Forensic analysis tools should be as intuitive as possible for their users. The operational complexity can lead to human errors, which can ruin the research.
Belkasoft Evidence Center X shows a minimalist graphic interface that guides the analyst to the available operations.
The acquisition or intake of data
The tool allows the creation of cases in which the data sources to be analyzed have multiple sources. From disk images or existing memory dumps, to the image creation from Android or Apple mobile devices. This is striking, being rare in suites of this type, which are usually specialized solely in forensics of mobile devices or in the treatment of volume images for Windows or Linux operating systems.
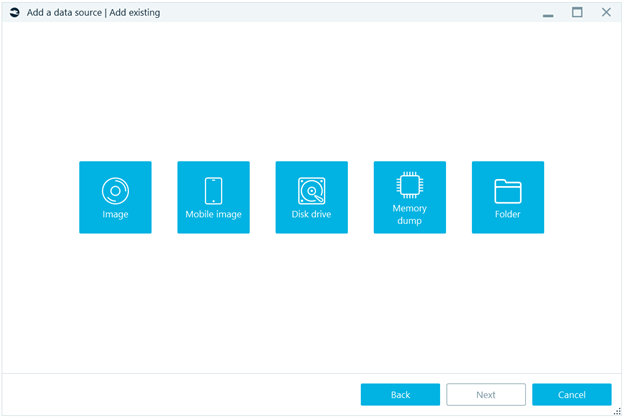
Figure 1. Add data source
The possible options within the data analysis make up the identification of different type of files, carving in free space of file systems and unallocated space, as well as identification of images that belong to categories to identify weapons, drugs or pornography.
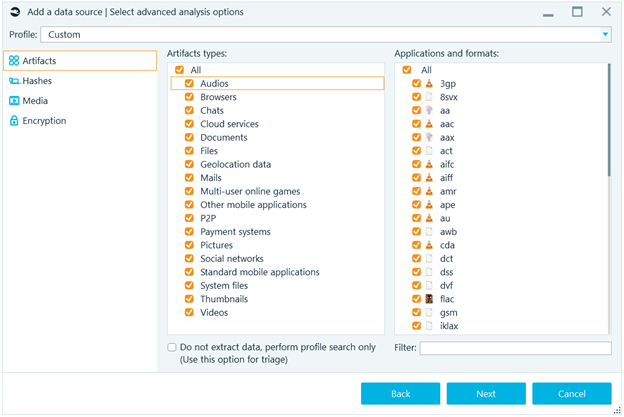
Figure 2. Types of files to identify
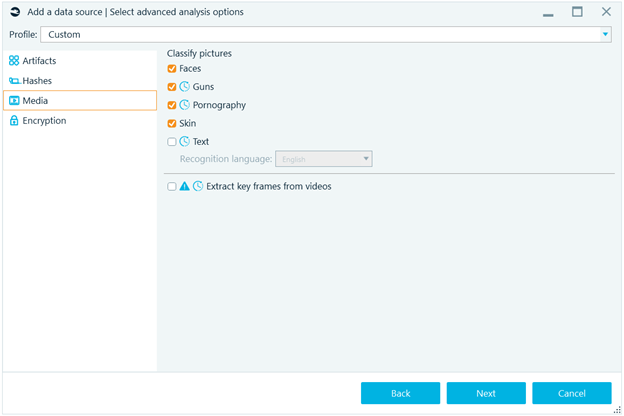
Figure 3. Advanced identification in images
Depending on the options selected and the size of the evidence to be acquired, the process may take several hours.
The analysis
Once the acquisition and classification of information is completed, the tool will allow the user to access the different elements identified, according to the type of file, allowing it both on the current file systems of the selected volumes, as well as in the Shadow Copies of them.
The power of forensic tools of this type is given by the amount of supported applications for identification and interpretation. Thus BEC X classifies contents identified evidence such as Audios, Browsers, Chats, Documents, Encrypted documents, Mailboxes, Mobile applications, Pictures, System files, Thumbnails and Videos.
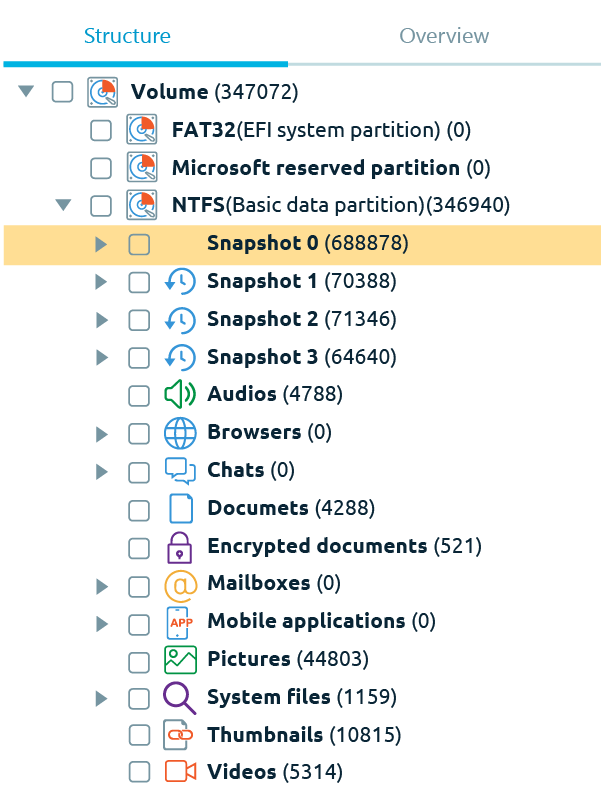
Figure 4. Index of results obtained
In the results obtained, BEC X allows to carry out narrow searches between ranges of start and end date/time. Identifying activity over a period of time is vital in investigations, since in many cases the important thing is to focus on what happened in a system on a specific date.
Report generation
Every investigation always ends in a written report. The quality of it will depend on the quantity and usefulness of the information extracted and processed and, of course, the analyst skill and experience.
The structure and body of the report will depend on the requirements of each case, the findings extracted from sources of evidence and their relevance to the research. Belkasoft Evidence Center X allows the evidences to be exported to different formats.
Figure 5. Report formats
Processing this output can help the analyst identify possible breakpoints evidence that initially did not take into account, which may be key in the investigation. These results may also be added as annexes in a support of non-rewritable storage.
Conclusion
Belkasoft Evidence Center X is a very useful tool for digital forensic analysis, that identifies and retrieves information, classifying it by type of file, which complements the manual investigation processes that we develop at Securízame.
Its capabilities to automatically identify the content of pictures that may be illegal is very interesting for certain types of investigations.
It is also useful to carry out blind searches in the email and chat messages from some messaging systems.
See also