How-To: Kirin Brute-Force and Acquisition
Equipped with Mobile Passcode Brute-Force module, Belkasoft X can brute-force a Kirin device and bypass its lockscreen. As a result, a physical image and keystore can be acquired by Belkasoft X. Decryption keys are also acquired, what enables the product to deal with FBE (File Based Encryption) on a device.
How-to
- Create a case
- On the Dashboard, click on the 'Add data source' menu
- Select Acquire → Mobile → Android → Kirin
- Connect a device in COM-port mode:
- Power off the device
- Remove the back cover of the device
- Locate the Test Point on the motherboard; for certain devices, it may be necessary to partially remove a section of the board
- Using metal pliers, short the Test Point
by connecting it with a plate on the board:

- While still shorting the Test Point, connect the device to the PC using a standard USB cable
- A new port named 'HUAWEI USB COM 1.0' should appear in the Device Manager. If, after connecting the device, an unknown device named 'USB SER' appears instead of a new port in the Device Manager, it indicates that the necessary driver is missing—you will have to install a proper Huawei driver for the device
Installing a proper driver
While acquiring Kirin, it is crucial to connect the device in COM port mode. Confirm the correct COM port by checking the 'Ports' section in the Device Manager window, as illustrated in the screenshot below:
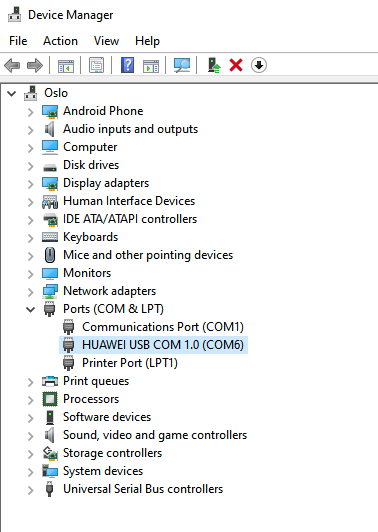
If the device does not appear under a COM port, follow these steps:
- Check if 'USB SER' is listed under the 'Other devices':
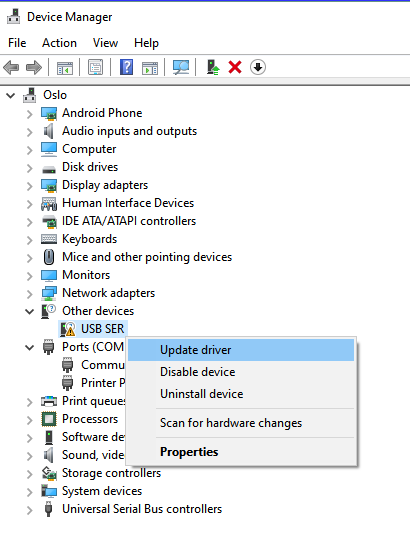
- Right-click on this item and choose 'Update driver'
- Opt for 'Browse my computer for drivers':
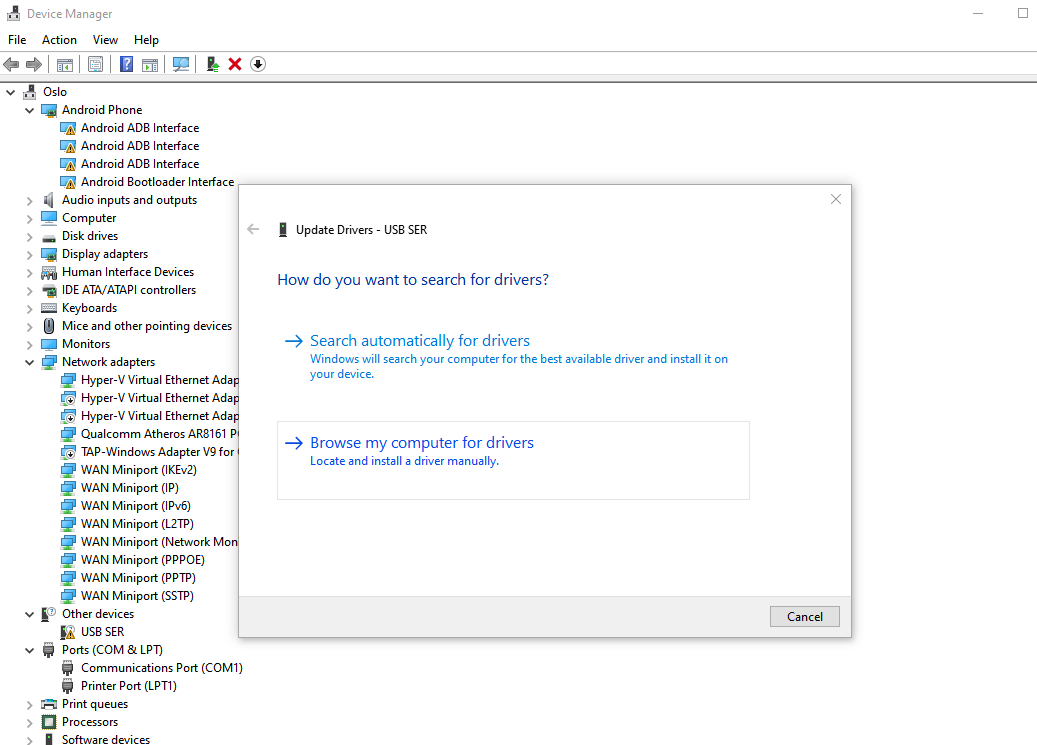
- Select 'Let me pick available drivers on my computer':
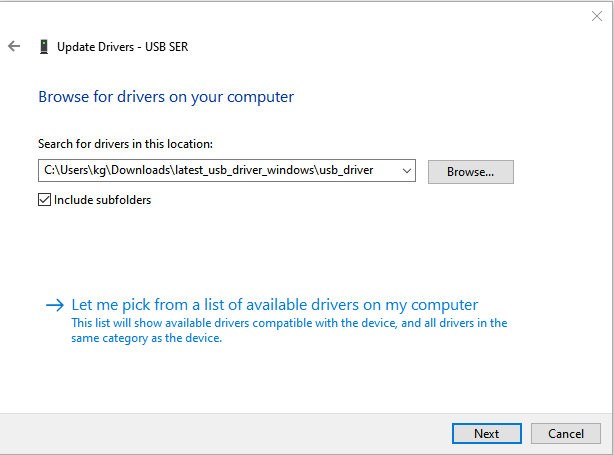
- Choose 'Ports (COM & LPT)':
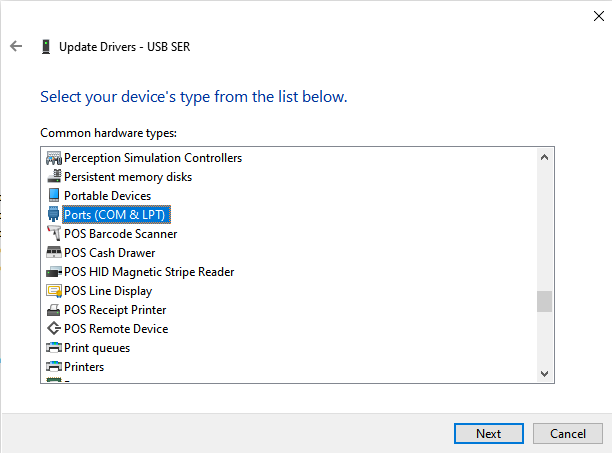
- Specify 'Huawei Incorporated' as the manufacturer and 'HUAWEI USB COM 1.0'
as the model:
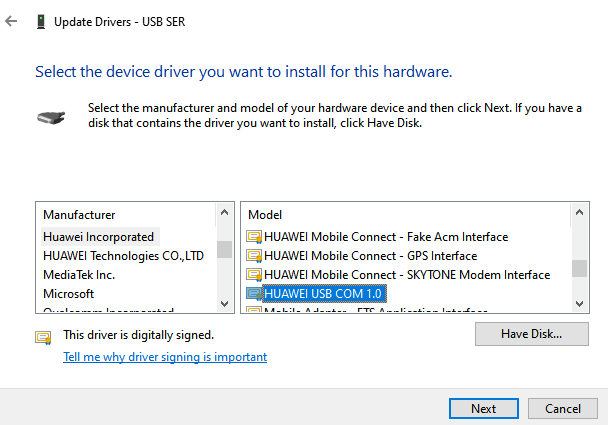
- Proceed with the driver installation:
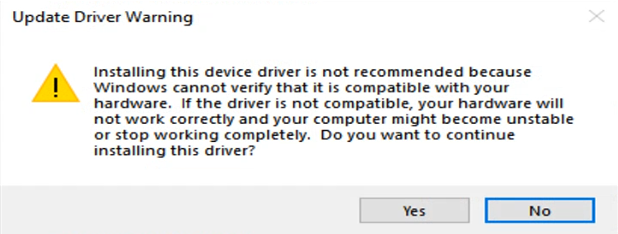
- If the driver is successfully installed, you will see the confirmation window:
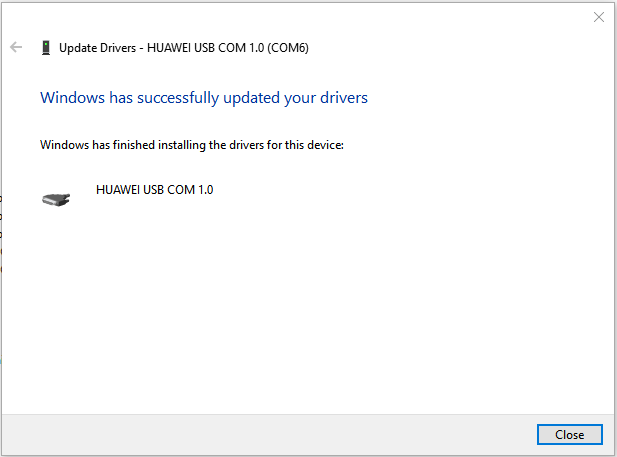
Now, upon checking the Device Manager again, 'HUAWEI USB COM 1.0' should be visible, as depicted in the initial screenshot above.
See also
- A list of devices supported by the Mobile Passcode Brute-Force module
- Why Belkasoft should be your tool of choice for Mobile Forensics
- Unlocking iOS Devices with Brute-Force