Acquiring iOS device
Acquiring mobile device
Using this option, you can acquire an iOS device connected to your machine.
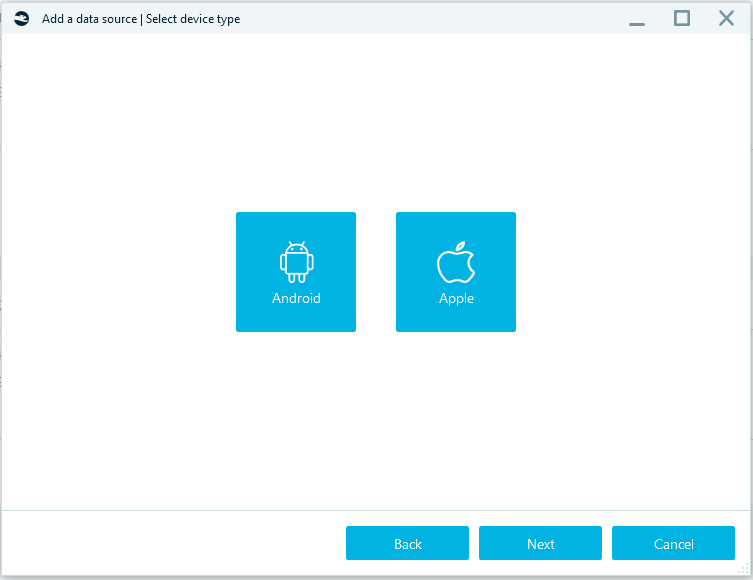
After clicking on Apple, you will see the list of acquisition types.
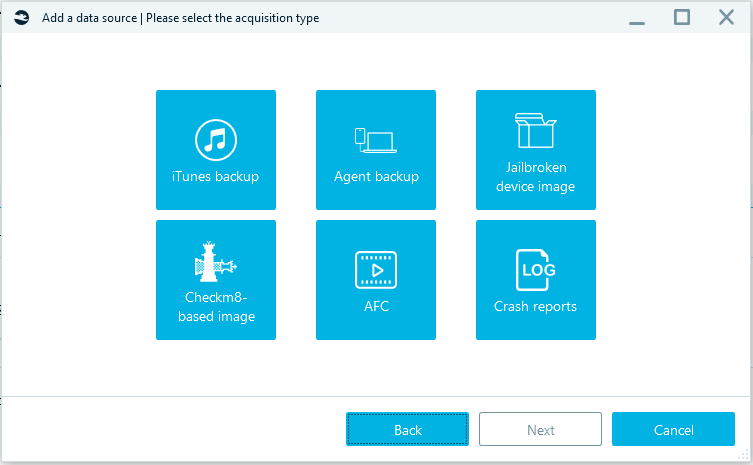
iTunes backup
This is the standard way to backup iOS device data. It requires iTunes to be installed on the machine where Belkasoft X is running.
Note: Encrypted backup contains more data. Belkasoft X automatically turns on encryption if no password is set in iTunes.
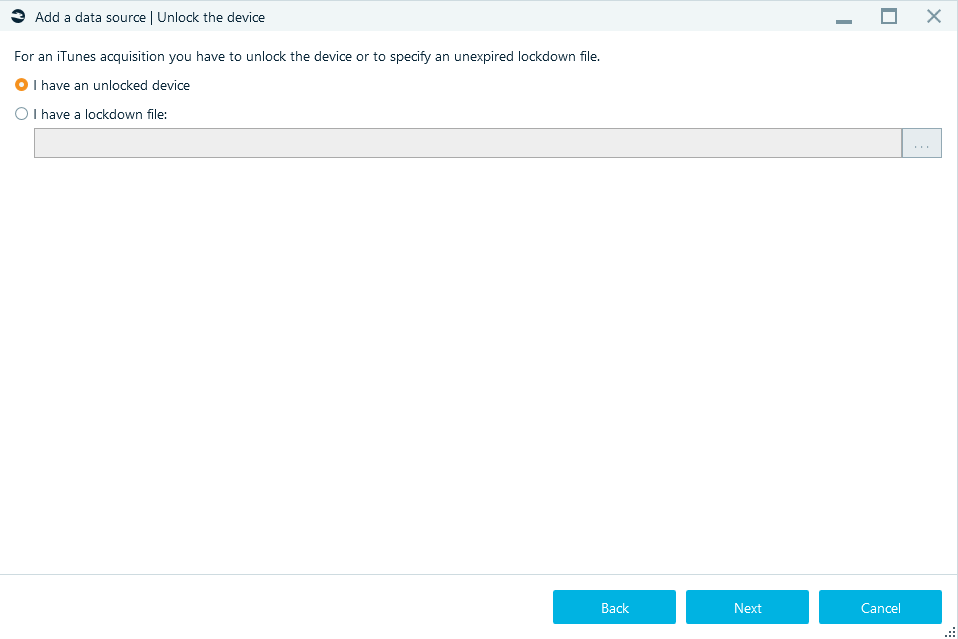
To continue acquisition, you need to unlock smartphone or determine the path to the lockdown file.
Specify the Target path (for the folder where the smartphone image will be stored) and click Start—acquisition will begin.
If the password in iTunes was not set, during the acquisition enter the iPhone Unlock password on smartphone twice: at the beginning of the acquisition and at the end.
Agent-based acquisition of iOS devices
This method copies the contents of the file system through the installation of a special agent application. The amount of extracted data will be the same as with full logical backup of jailbroken iOS devices acquisition or Checkm8-based acquisition of iOS devices (including data from keychain).
For the full list of supported device models and iOS versions, please refer to the agent-based acquisition page.
Before you start acquisition with the agent backup, check and confirm that:
- Computer has internet access if you are using an Apple Developer ID
- Device has internet access if you are using an Apple ID (free)
- Antivirus is stopped or paused
You will see the window below after selecting Agent backup in the window Add data source| Please select the acquisition type:
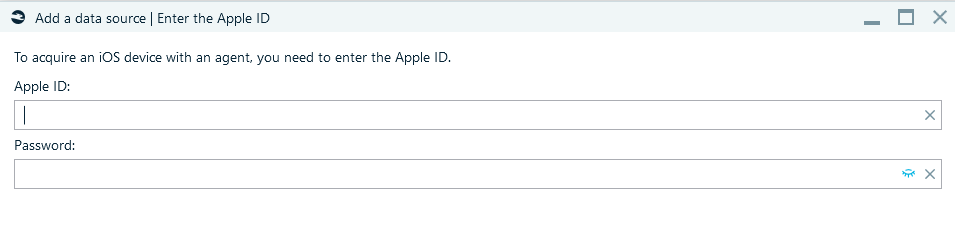
If you are using an Apple Developer ID (an Apple ID that participates in the Apple Developer Program) enter it and the App-specific password. Or use Free Apple ID and Password.
Unlock the iPhone or iPad using its passcode and connect the device to PC using a USB cable (port 3.0 is preferred). When you see the Trust this computer message on the iPhone, click Trust.
Specify the Target path and click Start—acquisition will begin.
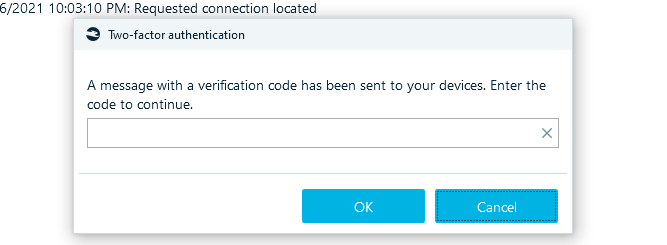
If an Apple ID has two-factor authentication, enter the verification code in the Two-factor authentication window:
Follow the instructions in window Acquire a mobile device:
In order for the application to work, the certificate must be confirmed in the device settings:
- In the iOS Settings scroll down and tap 'General'
- Scroll down and tap 'Profiles, Profiles & Device Management' or 'Device Management', depending on the iOS version.
- Select a profile with Apple ID.
- Tap 'Trust [Apple ID]' and confirm your choice.
- Waiting for the profile to be trusted.
After the Agent is downloaded to the smartphone, enter the smartphone password.
Jailbroken device image
This acquisition method is only available for jailbroken iOS devices; however, it allows extracting much more data than by using standard iTunes backup.
This requires iTunes to be installed on the machine running Belkasoft X.
After choosing Jailbroken device image and connecting smartphone, you will see the window below:
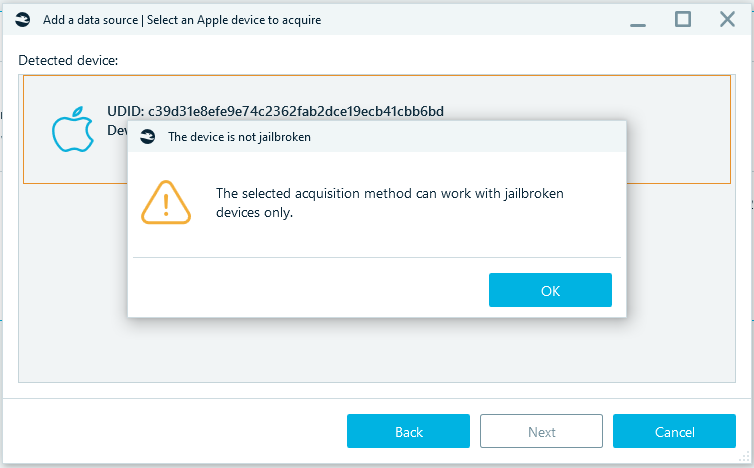
After clicking on the Next button, the jailbreak status of the phone will be checked. If jailbreak has not been completed on the device, a message will appear:
If jailbreak has been completed on the device you will see:
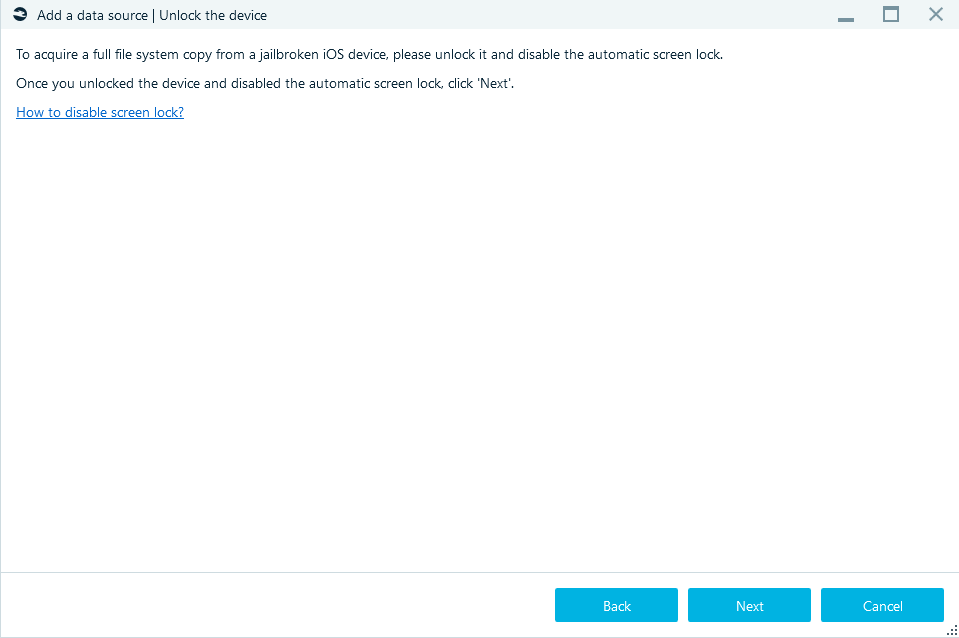
Then select Target folder, click Start, and the acquisition process begins. Once the process reaches completion, you will see the iPhone or iPad image, which comes out as a TAR archive housing all the acquired data (including keychain).
Checkm8-based acquisition of iOS devices
The Apple Checkm8 function provides direct access to the file system of iPhones and allows for forensically sound extraction of data from the devices.
For the full list of supported device models and iOS versions, please refer to the checkm8-based acquisition page.
Note: To run Belkasoft X and perform the task here, you need a Windows 10 PC with the latest iTunes version installed on it.
After selecting Apple Checkm8, connect the iPhone to your PC using a USB cable.
- The cable must be original
- Use a USB 3.0 port
- Confirm the correct settings are set on the phone: Settings - Display & Brightness - Auto-Lock should be Never.
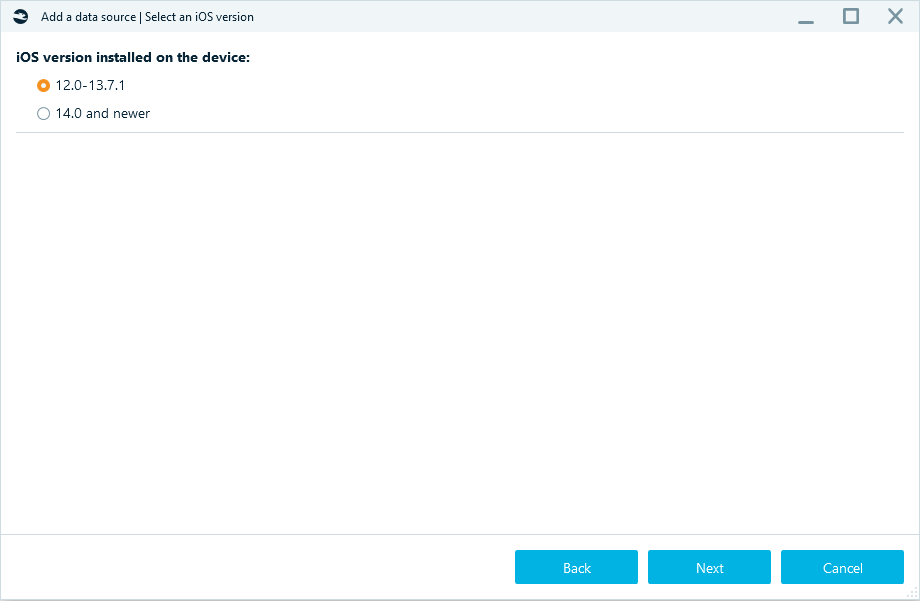
Choose the device iOS and iPhone model.
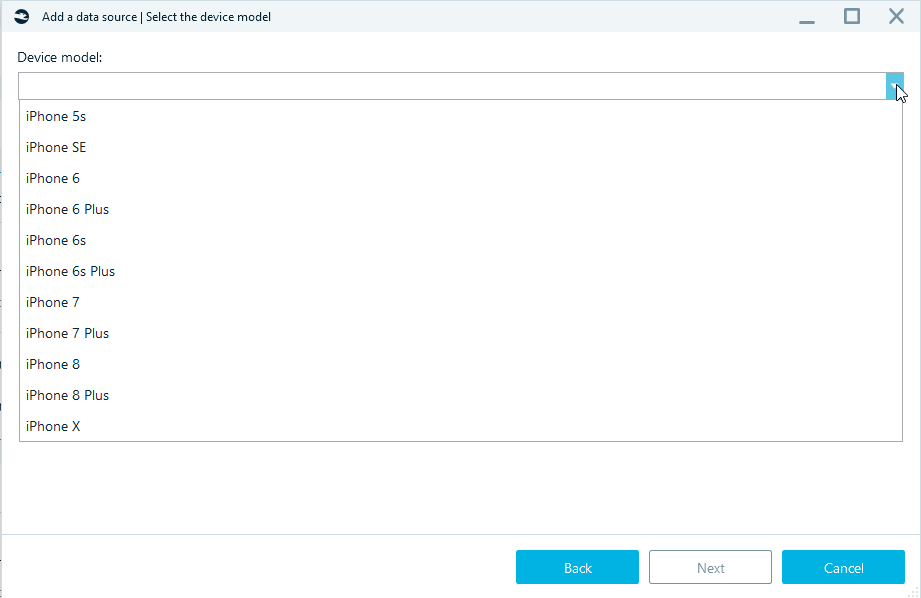
Select smartphone:
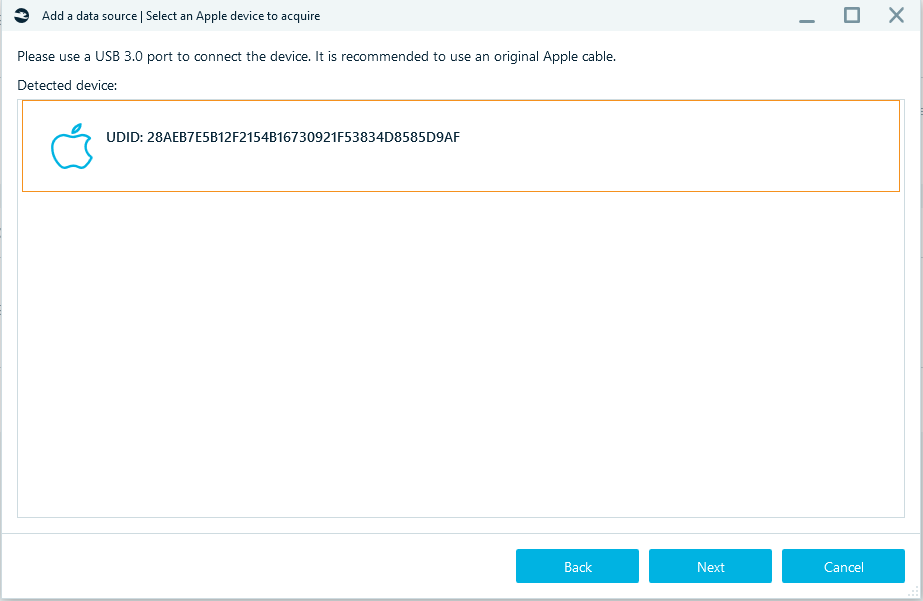
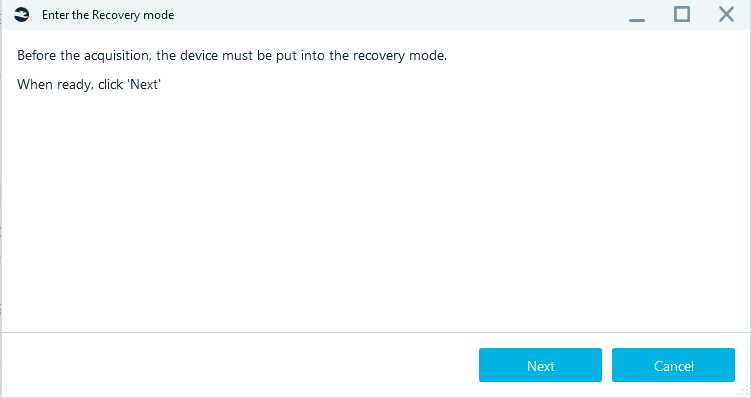
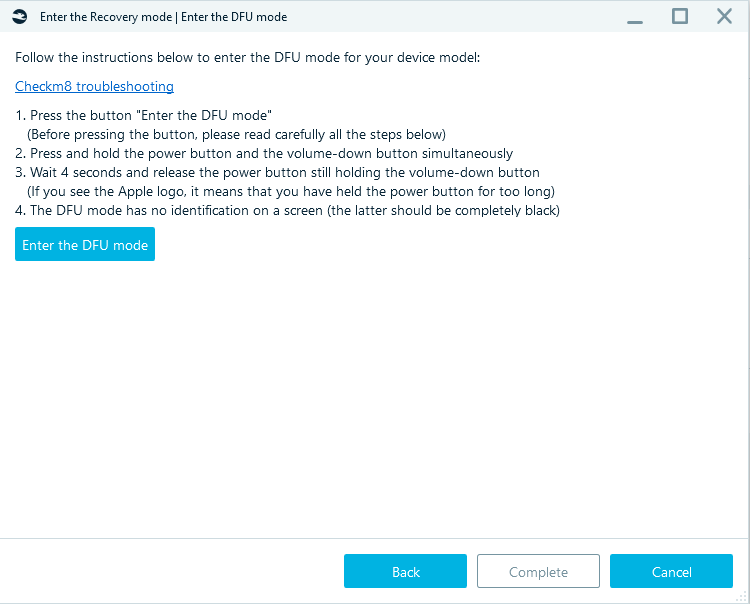
Specify the Target path, click Start and follow the steps required to get the iPhone into Recovery and then into DFU mode.
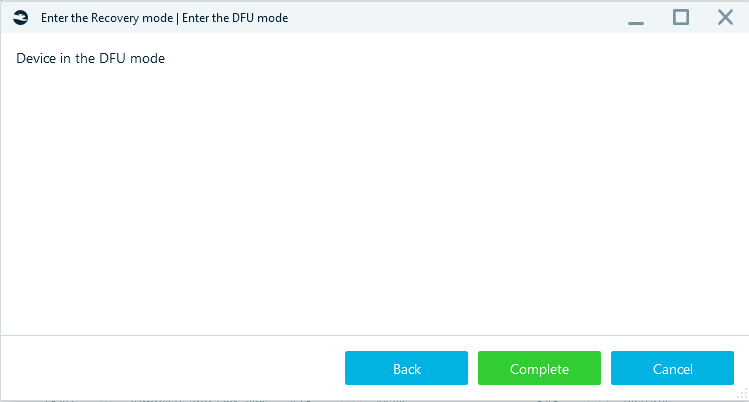
After clicking on the Complete button, Belkasoft X will communicate with the device and run the exploit.
The acquisition log will be displayed.
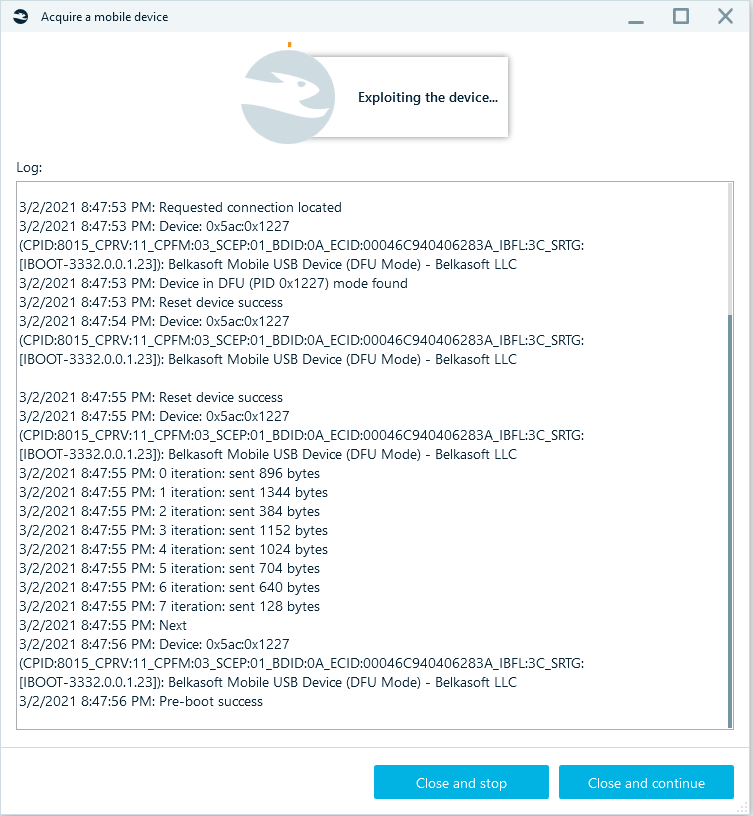
You should pay attention to them. Belkasoft X might prompt you to enter the passcode for the iPhone. If the password is known, use it to unlock the device now. Otherwise, if the passcode is unavailable, click on the OK button to dismiss the prompt. In any case, Belkasoft X will start copying data from the iPhone.
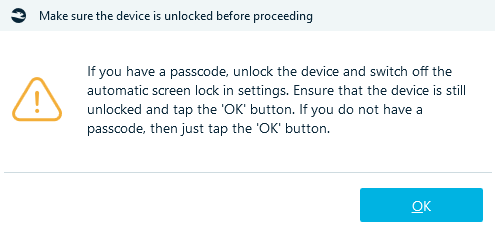
Then enter the password on the device.
At the end of it all, you will see the Operation completely successfully message.
FAQ
- Sometimes checkm8 works from second or third attempt only. Between attempts, please reboot the device twice.
- If the phone was previously jailbroken with other jailbreaks (or many times with checkra1n), it is common that it does not work with checkm8.
- Phones having MDM tools installed, have issues with checkm8 and checkra1n. The proper acquisition is not guaranteed, it is recommended to unregister them from the corresponding MDM.
- Other forensic tools, which support checkm8-based acquisition on Windows, may interfere Belkasoft work. It is recommended to separate these tools.
- If the USB Restricted Mode is enabled on the device and you do not
have the passcode to an iPhone, you will be able to acquire data in BFU (BFU
is an acronym for Before First Unlock). Belkasoft X disables USB Restricted
Mode automatically during the checkm8-based acquisition process. You do not
even need to perform manual or complicated maneuvers.
BFU acquisition can still provide you a lot of data. Here, you can see the results from one of our experiments—Belkasoft’s checkm8-based acquisition from the same iPhone with and without the passcode: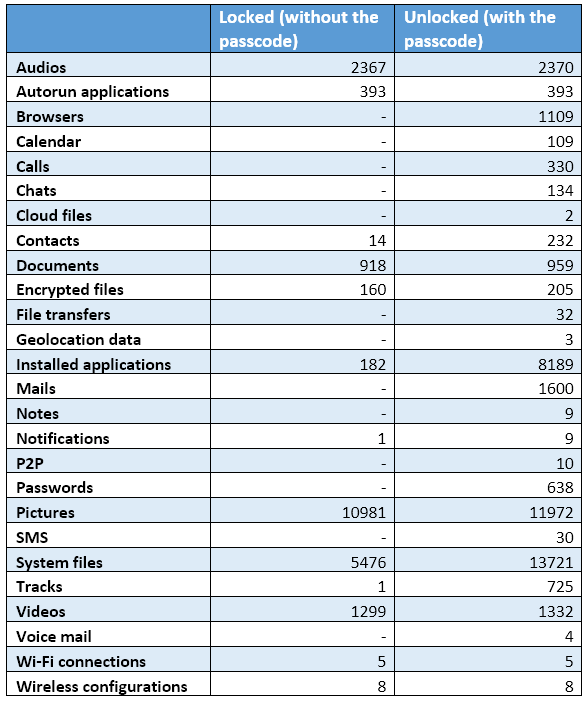
- If in the process of preparation for acquisition message 'Cannot locate
the iTunes service. Please install it from the Microsoft Store' appears:
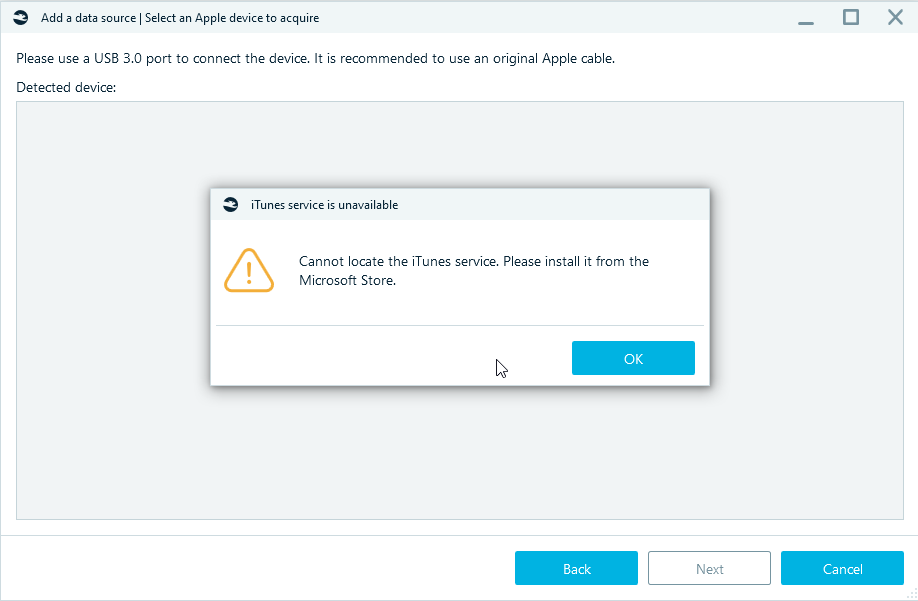
Try opening iTunes or reinstalling. The list of services should contain: AppleMobileDeviceService.exe (AppleMobileDeviceProcess.exe), ApplicationFrameHost.exe. - If you suspect that the issue is with the Belkasoft product, try manual checkra1n. If it does not work either, most possibly, you will not be able to acquire the device with software-based methods.
AFC
This type of acquisition uploads data through Apple File Conduit (AFC) protocol. Available files: Photos, Videos, and some apps.
It requires iTunes to be installed on the machine where Belkasoft X is running.
Crash reports
Extracting application and system crash logs on iOS.
To use this functionality, you do not need to jailbreak your device, it is sufficient to have a passcode or a lockdown file of the device.
Keychain extraction
Keychain is the password management system developed by Apple. Without the keychain, it is impossible decrypt the various encrypted data extracted with the full file system acquisition.
Belkasoft X can extract keychain through all methods that extract full file system image: using checkm8-based acquisition, jailbroken device acquisition, and, with some limitations, agent-based acquisition. Based on the extracted information, various decryption tasks become possible. For instance, Belkasoft X can decrypt iOS Signal and Wickr messengers out of the box.
