What's new in BEC v.9.5
What's New in Belkasoft Evidence Center 2019 Version 9.5
Belkasoft Evidence Center 2019 v.9.5 (or, in short, BEC) is an all-on-one forensic solution, combining mobile, computer, RAM, cloud and remote forensics in a single tool. Given its affordable price, it is one of the best choices among other available products on the market.
Version 9.5 of BEC 2019 is one of the biggest releases with regards to changes, over the last few years. A number of new large-scale features are added, including the following:
- Remote acquisition of computers, mobiles and RAM
- Incident investigation
- Cross-case search
- TWRP dump mounting and analysis
- Full logical backup of jailbroken iOS devices
- ANN detection for arrow and cross signs on images
- Telegram X decryption
- Decryption of Bitlocker and McAfee Endpoint Security encrypted images
- Multi-partition APFS support
- Massive update of multi-user Team Edition module
- Numerous updates to artifact extraction
- New 3-day official training along with optional BelkaCE (Belkasoft Certified Examiner) certification is added
Sign up for a webinar on BEC v.9.5!
Upgrading to version 9.5 is free to all customers with a non-expired Extended Software Maintenance and Support contract. Customers without a current contract can purchase it from the Customer Portal. An affordable User Refresher Course is also available for those who would like to catch up on all recent improvements. Training with optional certification is available.
New features in detail
Remote acquisition
Remote acquisition is aimed to help investigators in a distributed environment. When an organization has multiple locations and each location may receive seized devices, it can be a challenge to conduct forensic analysis of such devices in a timely manner. Invariably, some location will not have a trained specialist to perform acquisitions. It may also take a while to send the device to the central office or to send a specialist to that location. If a computer or a laptop memory must be acquired, then the option to send the device in, ceases.
These problems can be solved with remote forensics, now available with Belkasoft. The new version of BEC allows you to install an agent on any computer inside your network and with a minimum of efforts acquire computer hard drive, RAM memory or a connected mobile device. The acquired image can be then scheduled for the upload to the central location. It can be done at the night time so that the working hours Internet throughput does not suffer.
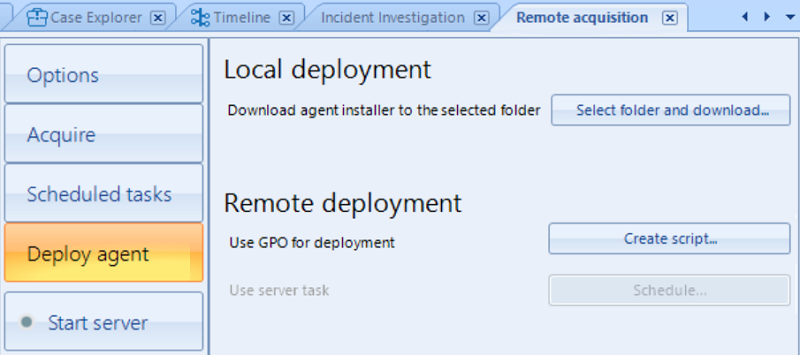
Using BEC you can easily deploy an agent to a remote computer, then acquire
a data source connected to this computer and then schedule uploading of the
created image back to your main computer
The new feature is helpful for LE departments having multiple offices as well as to private companies with centralized forensic departments. For the latter using BEC built-in remote acquisition capabilities could become a huge cost, time and effort saver.
Remote Acquisition is available as a separate paid plug-in.
Incident investigation
Incident investigation is a brand new feature, which further expands the usage of BEC for corporate customers. This new function is aimed in helping private companies investigate hacking attempts of Windows-based computers. By analyzing numerous sources such as registry, event logs and memory dumps, it can find traces, which are typical to various tricks used by hackers to penetrate company's infrastructure.
Belkasoft Evidence Center looks at various artifacts located inside Amcache, ShimCache, Syscache, BAM/DAM, AppInit DLLs, Change of default file association, scheduled tasks, remote connections (RDP, Remote Connection, TeamViewer and others), startup tasks, browser extensions and so on; it detects suspicious connections and scripts.
The results of analysis are then presented inside a brand new window of BEC making it easy to separate suspicious activities from regular forensic artifacts.
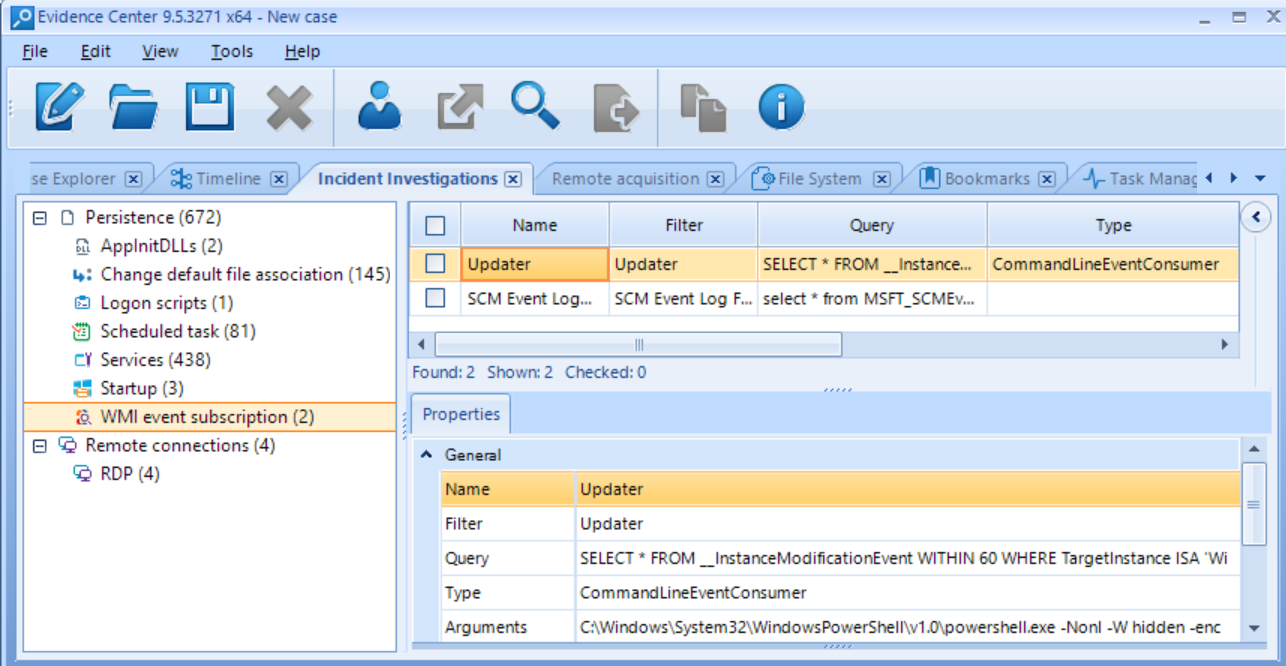
New BEC pane conveniently combines various sources to inspect in a course
of an incident response case
This new feature makes BEC a complete DFIR solution, which helps customers not just with "DF" part of the abbreviation but also with "IR".
Incident Investigation is available as a separate paid plug-in.
Cross-case search
This new feature of BEC 9.5 helps you and your fellow investigators find intersections of the current case being investigated with archived cases.
As the product analyzes the current case, it looks into previous cases worked on, and attempts to locate various data residing in the current case. You may configure the tool on what data to look for, as well as which older cases to look into.
If an email, a phone number, or a profile name found in the current case is also found in an older case, this might mean that people in these cases are somehow connected or have something in common. Understanding the importance of such information, any cross-search hit triggers an alert at the BEC's status bar, so that you can immediately notice that.
You can review the cross-search results under "Search Results" window of the BEC's interface under the new node called "Alerts".
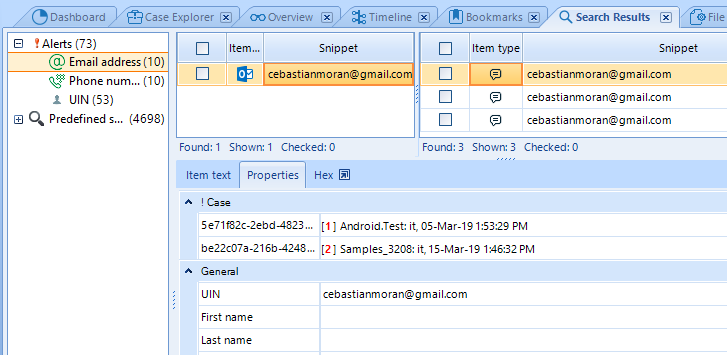
If the phone, email or UIN found in the current case met in earlier cases,
BEC will notify you about it using a special node inside Search Results window
This feature is especially useful with Team Edition of BEC since it will enable you to search not only inside your local BEC cases stored on a single machine but also go through your colleagues’ cases stored remotely.
Cross-case Search is available for free to the Team Edition license holders and as a separate paid plug-in for customers having the single-user license.
TWRP dump mounting and analysis
With v.9.5 BEC can mount and analyze Android TWRP images.
TWRP (Team Win Recovery Project) is an open-source custom recovery image for Android devices. With this tool, the user gets access to a substantial functionality for device management. Using TWRP, you can create a complete logical copy of a user's “/data” partition and then investigate it with BEC.
A list of supported devices can be found on the TWRP project website.
This feature is available for all BEC customers having up-to-date Mobile Device Analysis module.
Full logical backup of jailbroken iOS devices
With BEC v.9.5 you will now be able to do a full logical backup of iOS devices, which are jailbroken. Full copy of Apple devices contains much more info than a standard iTunes backup, including various chats and other applications. In particular, with such a backup you can even restore Telegram's secret chats after they have been deleted.
BEC supports making the full logical backup as well as analysis of acquired files, such as the abovementioned deleted Telegram secret chats recovery.
This feature is available for all BEC customers having up-to-date Mobile Device Analysis module.
ANN detection for arrow and cross signs on images
The new version of Belkasoft Evidence Center extends support for investigators dealing with drug-related crimes. One of artifacts, which may prove the fact of drug distribution, can be a specific set of pictures stored on a suspect's device. Such pictures contain a place where a drug tab is hidden along with a hand-drawn arrow or a cross on top of the picture.

This is a real example of an image used to mark a drug stash
Using state of art artificial neural networks, Belkasoft can find such pictures among hundreds of thousands of other pictures from a device, thus dramatically speeding up the investigation.
This feature is available for all BEC customers with valid SMS. The download of a separate installer is required (available inside your Customer Portal, make sure you download .ann version).
Android's Telegram X decryption
Belkasoft supports dozens of various applications in each release, but the newly appeared support of Telegram X stands apart. This popular messenger uses strong encryption, which details are not yet well documented. That is why Belkasoft specialists had to spend significant amount of hours in an effort to understand this format.
Belkasoft is a first digital forensic tool to support Android's Telegram X decryption.
This feature is available for all BEC customers having up-to-date Mobile Device Analysis module.
Multi-partition APFS support
APFS is a file system introduced in macOS High Sierra 10.13 in 2017. Belkasoft was one of the first three digital forensic tools to support APFS last year. We are constantly improving this support and, in this release, multi-partition APFS images were supported.
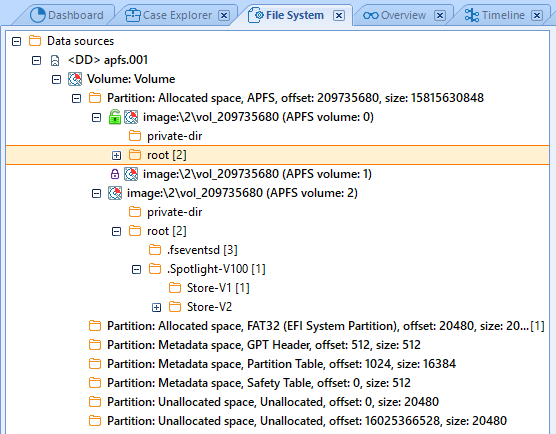
Artifact extraction from APFS is available for all BEC customers with valid SMS. File system view is available for customers having up-to-date File System Explorer module.
Massive update of multi-user Team Edition module
Team Edition enables private and government organizations, having multiple digital investigators to:
- efficiently split their work
- work on the same cases together
- store cases centrally in a high-performance Microsoft SQL Server database, thus enabling access to the case from different computers and by different people
- restrict user access rights to edit or view a case
- have local and remote cases in the same product interface
- use other investigator cases for cross-case searches
With v.9.5, Belkasoft significantly improves the user experience of Team Edition, its performance and robustness. Besides, new Cross-case search module is available for Team Edition license holders free.
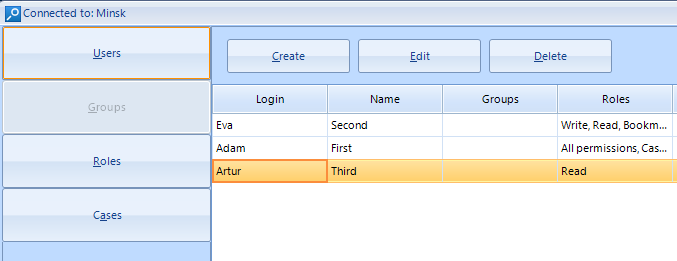
With convenient User Management screen an administrator can create users
and assign roles to them
This feature is available for all BEC customers with valid Team Edition license. Upgrades from single-user or network license are available.
Other improvements
Apart from major features introduced above, there are multiple other improvements. Among them are:
- Artifact analysis improved/supported
- All platforms: Chrome, Facebook, Instagram, Odnoklassniki, Safari, Skype, Skype cross-platform, Uber, Vipole, VK, WeChat, WhatsApp
- Windows: Avant and Sogou browsers, Map app
- iOS: Apple Mail, Chrome, KIK, Live me, Microsoft Edge, Opera, Twittie, Recently deleted notes for iOS Notes
- Android: Badoo, Dolphin browser, Gmail, Google+, Grindr, Hangout, ICQ, Imo, IM+, KateMobile, Mail.Ru agent, MeetMe, MeowChat, Next plus, ooVoo, Pinterest, Slack, Snapchat, Swarm, Tango, Telegram, Tinder, Twitter, Voxer, Xabber
- macOS: aMSN
- Computer forensics
- Bitlocker detection implemented
- Bitlocker decryption with a known decryption key implemented (requires Decryption Module)
- McAfee Endpoint Security decryption with a known decryption key implemented (requires Decryption Module)
- Video keyframe extraction updated
- Parsing of corrupted registry files improved
- MAC address extraction from LNK files fixed
- Extraction of recent files opened by various macOS applications supported
- Mobile forensics
- Parsing of Android sms/mms backup files added
- Cloud forensics
- iCloud authentication updated
- GSuite services download updated
- GUI and Usability
- Separate nodes for Pictures with face/pornography/guns/text are added in Overview
- SMS, Call, Conversation, Voice mail representation unified
- Separate "duration" column added where applicable for calls
- Separate "Delivery status" column added where applicable for chats and calls
- Save selected file to database fixed
- Recent cases sorted by opening date/time on Dashboard
- 'GPU is not found' warning removed where is not applicable
- Search in Plist and Registry Viewer added
- Sorting in SQLite Viewer added
- Automatic navigation to a registry branch where the selected artifact is stored, is implemented in Registry Viewer
- File Systems Explorer
- Long awaited filters added into File List
- Multiple improvements of Hash set analysis:
- Performance boost
- Fixed issue with not starting hash set analysis if artifact analysis is not selected
- File system is now visible in Evidence Reader (if original BEC had File System Explorer module)
Sign up for a webinar on new BEC v.9.5
See also:
Belkasoft Evidence Center 9.4
Belkasoft Evidence Center 9.3
Belkasoft Evidence Center 9.2
Belkasoft Evidence Center 9.1
Belkasoft Evidence Center 9.0
Belkasoft Evidence Center 8.6
Belkasoft Evidence Center 8.5
Belkasoft Evidence Center 8.4
Belkasoft Evidence Center 8.3
Belkasoft Evidence Center 8.2
Belkasoft Evidence Center 8.1
Belkasoft Evidence Center 8.0
Belkasoft Evidence Center 7.5
Belkasoft Evidence Center 7.4
Belkasoft Evidence Center 7.3
Belkasoft Evidence Center 7.2
Belkasoft Evidence Center 7.1
Belkasoft Evidence Center 7.0
Belkasoft Evidence Center 6.3.1
Belkasoft Evidence Center 6.3
Belkasoft Evidence Center 6.2
Belkasoft Evidence Center 6.1
Belkasoft Evidence Center 6.0
Belkasoft Evidence Center 5.4
Belkasoft Evidence Center 5.3
Belkasoft Evidence Center 5.2
Belkasoft Evidence Center 5.1
Belkasoft Evidence Center 5.0
Belkasoft Evidence Center 4.2
Belkasoft Evidence Center 4.1
Belkasoft Evidence Center 4.0
Belkasoft Evidence Center 3.9
Belkasoft Evidence Center 3.8
Belkasoft Evidence Center 3.7
Belkasoft Evidence Center 3.6
Belkasoft Evidence Center 3.5
Belkasoft Evidence Center 3.0
Belkasoft Evidence Center 2.0

