What's new in Belkasoft X v.2.6
Belkasoft Evidence Center X (Belkasoft X) is Belkasoft's flagship product for digital forensics, cyber incident response, and eDiscovery.
Belkasoft X v.2.6 includes the following major features:
- A new method for Android acquisition
- Massively enhanced Timeline window with new design and performance boost
- BelkaGPT improvements
- New important artifact: Oura ring data
- Decryption of credit card data saved in browsers
- Frequently requested mobile brute-force trial
Upgrading from previous versions of Belkasoft X to v.2.6 is free for all customers with an active Software Maintenance and Support (SMS) contract. Customers with expired or expiring SMS contracts may review and renew them through the Customer Portal.
Affordable training with optional certification is also available, including on-demand options.
New Feature Details
Revamped Timeline Window
In this release, we have significantly reworked the Timeline window to make it more informative, quick, and easy to work with:
- A separate window with the Graphical Timeline is removed
- The graphical timeline is now placed on top of the grid-view timeline, enabling users to see both representations at the same time:
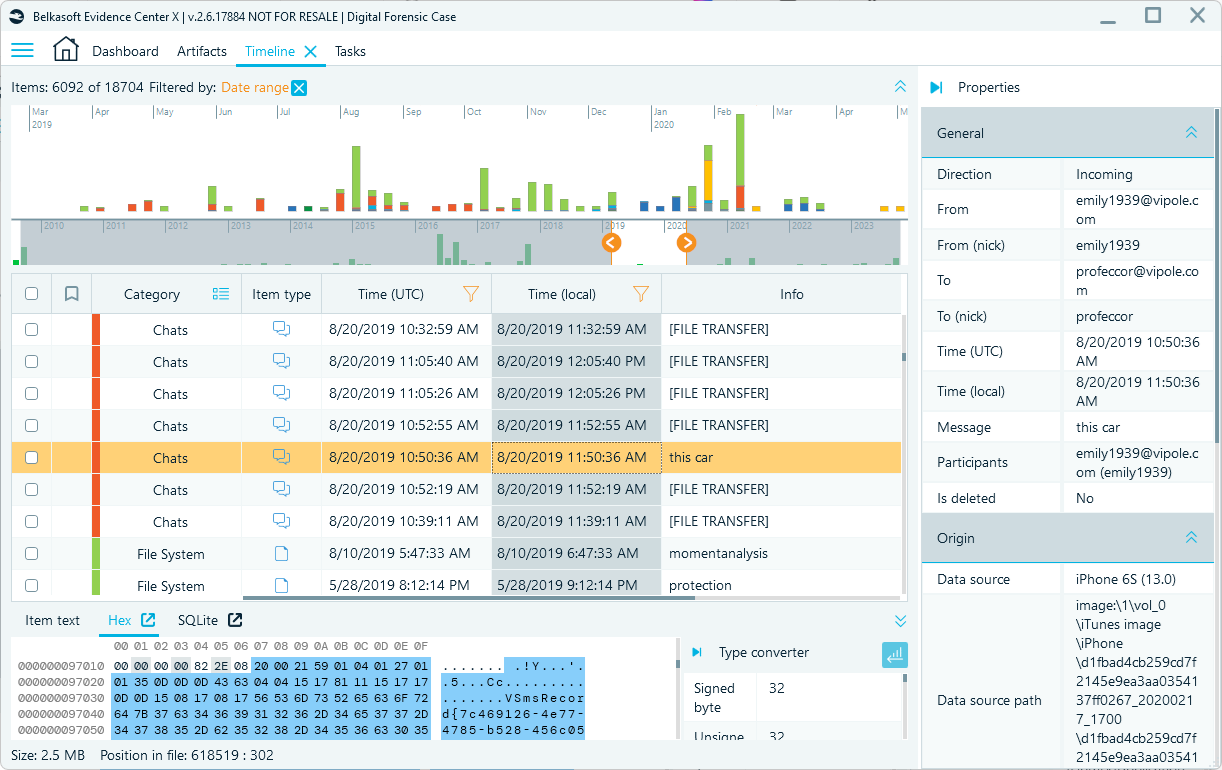
- File system timestamps are added as an additional source of time stamps (previously, only artifact times were considered)
- Fast filters by event type added:
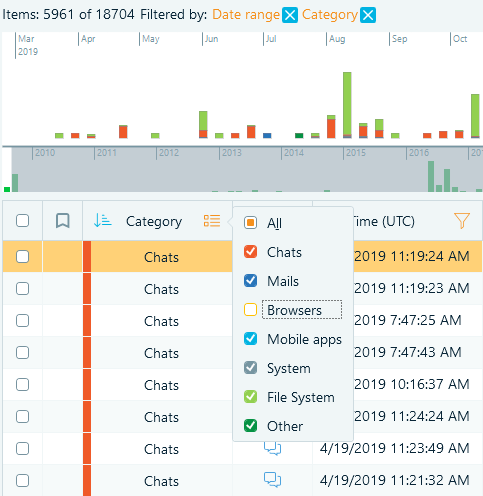
- Bookmarking supported: you can now bookmark timeline events, which will also bookmark the parent artifact (and, if that artifact belongs to another artifact, that one as well)
- Colored event categories have been added to the grid for quicker differentiation of various events
BelkaGPT
BelkaGPT is a cutting-edge AI DFIR tool from Belkasoft that helps digital forensic examiners uncover evidence using natural language queries, and its initial launch sparked a major boom in the DFIR market. With the latest version 2.6, it now boasts enhanced capabilities for processing nested data sources, making it even more powerful and effective for tackling complex cases.
Mobile Forensics
- Acquisition
- New method: application data acquisition Android 12 and 13. The new method works on every device that does not have Android 2024-03-01 security patch. The method is similar to APK downgrade on steroids, allowing you to acquire all application data for a chosen application
- Mobile Passcode Brute-Force: a trial version is now available. Previously, we only provided the full brute-force module to paid customers, however, many of you asked for a way to test the tool prior to purchase. In the new release, it is now possible. To test the module, you have to request this feature (it is not included into the trial version by default) and prepare a device with a passcode set to any value in between 0000-0099 or 000000-000099. The tool will check this range and will give you the correct passcode, if it is set to any of these, or will let you know otherwise
- MTK agent methods updated, a number of issues fixed
- Decryption of MTK FDE images improved
- F2FS parsing improved
Existing mobile artifacts updated, new ones added:
- iOS
- Encrypted notes (updated: v.15 supported)
- Firefox v.112.2 (updated)
- Gmail (updated)
- Instagram (updated: audio and video calls extraction improved)
- Microsoft Edge v.112.1722.64 (updated)
- Network interfaces (updated)
- Oura Ring (new). Oura Ring data is a small but crucial artifact for extracting valuable health and activity details that can provide insights into an individual's daily life and behaviors. This little ring collects information such as sleep patterns, heart rate, body temperature, and physical activity levels, making it a rich source of evidence in investigations. By analyzing this data, forensic experts can uncover critical details about a person's lifestyle and well-being, aiding in various legal and personal matters.
- Proton Mail (new)
- Snapchat v.12.34.0.28 (updated: cached attachment extraction implemented)
- Signal v.6.22 (updated: video call extraction supported)
- System configuration (updated)
- Telegram v.10.9.2 (updated: secret chat attachments and chat threads supported)
- Yubo v4.69 (updated)
- Android
- Slack (updated)
- Telegram v.10.9.2 and v.11.0.0 (updated)
- TikTok v.33.2.4 (updated)
Computer Forensics
Existing computer artifacts updated, new ones added:
- AVIF formats (new)
- Chrome credit card data (updated: decryption supported)
- Event log (updated)
- Linux Wi-Fi configuration data (updated)
- LNK files (updated: volume information improved)
- MAC vendor list (updated)
- Prefetch files (updated)
- RTF documents (updated: embedded font definitions supported)
- Skype (updated)
- Windows Microsoft Teams (new)
- Windows Notifications (updated)
- WMI event subscription analysis (updated)
On top of that:
- Text detection is improved for vector graphics
- Time extraction corrected for mail properties
Cloud Acquisition
- WhatsApp: QR code scanning restored
- Instagram with 2FA: Data acquisition restored
- Microsoft 365: Data acquisition restored
- iCloud Keychain: Timestamp extraction fixed
User Interface
- Translation to Vietnamese and Hungarian added
- More time filters added such as "by last credit card used time", "by user last online time", "by file access time" and others
- Artifacts properties: "Misc properties" removed from the properties list
- Tasks: Operation names updated, tooltip for trimmed names added
- Advanced options tabs: Content layout updated
- Picture analysis: Data loading improved
- Registry Viewer: "Find next" button behavior fixed
See also
Belkasoft X 2.5
Belkasoft X 2.4
Belkasoft X 2.3
Belkasoft X 2.2
Belkasoft X 2.1
Belkasoft X 2.0
Belkasoft X 1.17
Belkasoft X 1.16
Belkasoft X 1.15
Belkasoft X 1.14
Belkasoft X 1.13
Belkasoft X 1.12
Belkasoft X 1.11
Belkasoft X 1.10
Belkasoft X 1.9
Belkasoft X 1.8
Belkasoft X 1.7
Belkasoft X 1.6
Belkasoft X 1.5
Belkasoft X 1.4
Belkasoft X 1.3
Belkasoft X 1.2
Belkasoft X 1.1
Belkasoft X 1.0
Belkasoft Evidence Center 9.9
Belkasoft Evidence Center 9.8
Belkasoft Evidence Center 9.7
Belkasoft Evidence Center 9.6
Belkasoft Evidence Center 9.5
Belkasoft Evidence Center 9.4
Belkasoft Evidence Center 9.3
Belkasoft Evidence Center 9.2
Belkasoft Evidence Center 9.1
Belkasoft Evidence Center 9.0
Belkasoft Evidence Center 8.6
Belkasoft Evidence Center 8.5
Belkasoft Evidence Center 8.4
Belkasoft Evidence Center 8.3
Belkasoft Evidence Center 8.2
Belkasoft Evidence Center 8.1
Belkasoft Evidence Center 8.0
Belkasoft Evidence Center 7.5
Belkasoft Evidence Center 7.4
Belkasoft Evidence Center 7.3
Belkasoft Evidence Center 7.2
Belkasoft Evidence Center 7.1
Belkasoft Evidence Center 7.0
Belkasoft Evidence Center 6.3.1
Belkasoft Evidence Center 6.3
Belkasoft Evidence Center 6.2
Belkasoft Evidence Center 6.1
Belkasoft Evidence Center 6.0
Belkasoft Evidence Center 5.4
Belkasoft Evidence Center 5.3
Belkasoft Evidence Center 5.2
Belkasoft Evidence Center 5.1
Belkasoft Evidence Center 5.0
Belkasoft Evidence Center 4.2
Belkasoft Evidence Center 4.1
Belkasoft Evidence Center 4.0
Belkasoft Evidence Center 3.9
Belkasoft Evidence Center 3.8
Belkasoft Evidence Center 3.7
Belkasoft Evidence Center 3.6
Belkasoft Evidence Center 3.5
Belkasoft Evidence Center 3.0
Belkasoft Evidence Center 2.0


